
File upload functionality in web applications is a critical feature but can pose significant security risks if not properly implemented. One common vulnerability found in web applications is the file upload vulnerability, which attackers can exploit to gain unauthorized access, execute malicious commands, or upload harmful files onto the server. In this article, we will demonstrate how to test a file upload vulnerability using the DVWA (Damn Vulnerable Web Application) lab, a platform designed for security testing.
What is a File Upload Vulnerability?
A file upload vulnerability occurs when a web application improperly handles file uploads, allowing attackers to upload dangerous files (such as PHP scripts, executables, or other malicious content) to the server. These files can then be executed, often with the same privileges as the web server, leading to severe security breaches such as remote code execution, system compromise, or data theft.
Setting Up the DVWA Environment
For testing purposes, we are using DVWA (Damn Vulnerable Web Application), a tool designed to simulate common web application vulnerabilities, including file upload issues. To begin the testing, we first log in to the DVWA platform using valid credentials. Once logged in, we set the security level to “Low” to make the vulnerability easier to exploit.
Step 1: Accessing the File Upload Page
After logging in and setting the security level, we navigate to the file upload page by clicking on the “Upload” option in the left menu. Here, we will test the file upload functionality and examine its security weaknesses.
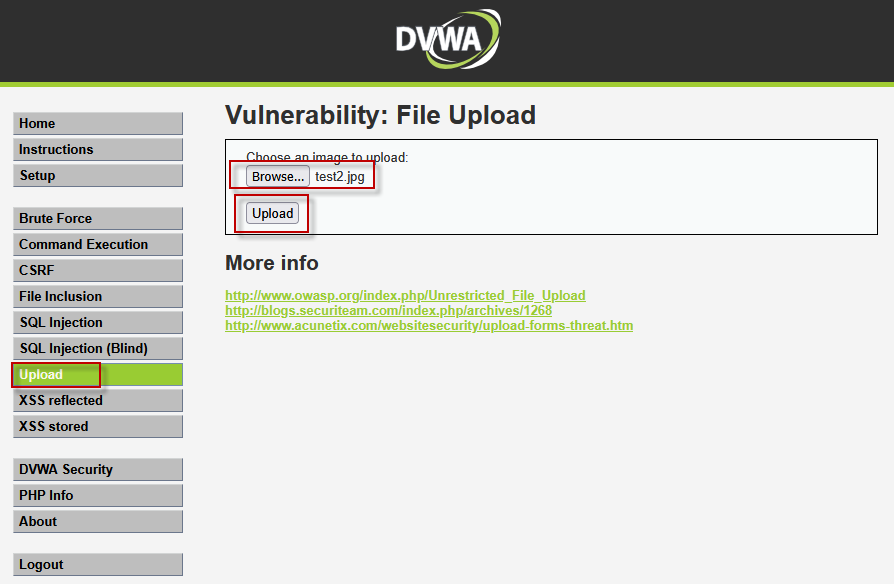
Step 2: Uploading a Simple .jpg File
To begin, we upload a simple, non-malicious .jpg image file. After selecting the image, we submit the form. The application successfully uploads the image and displays a message indicating the file’s location:
"../../hackable/uploads/test2.jpg"
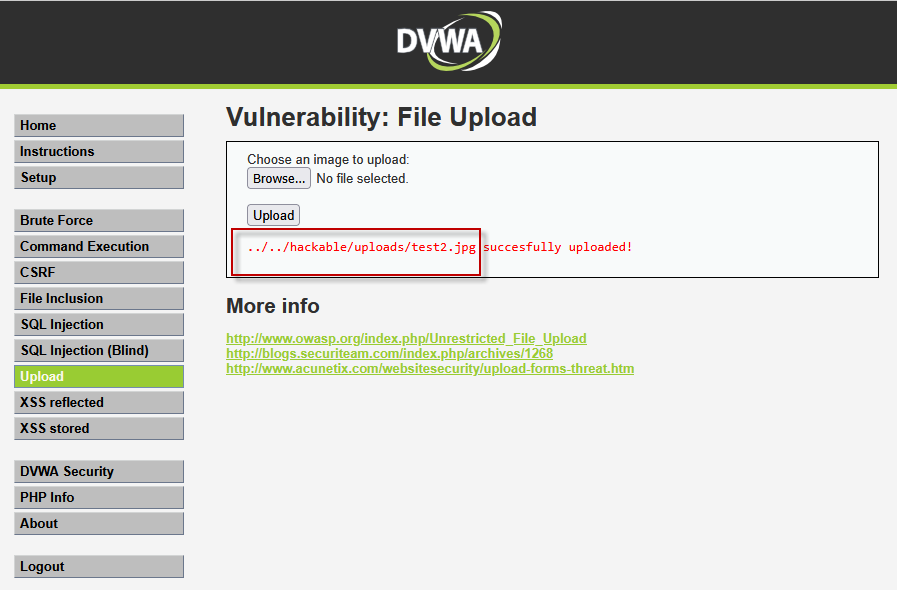
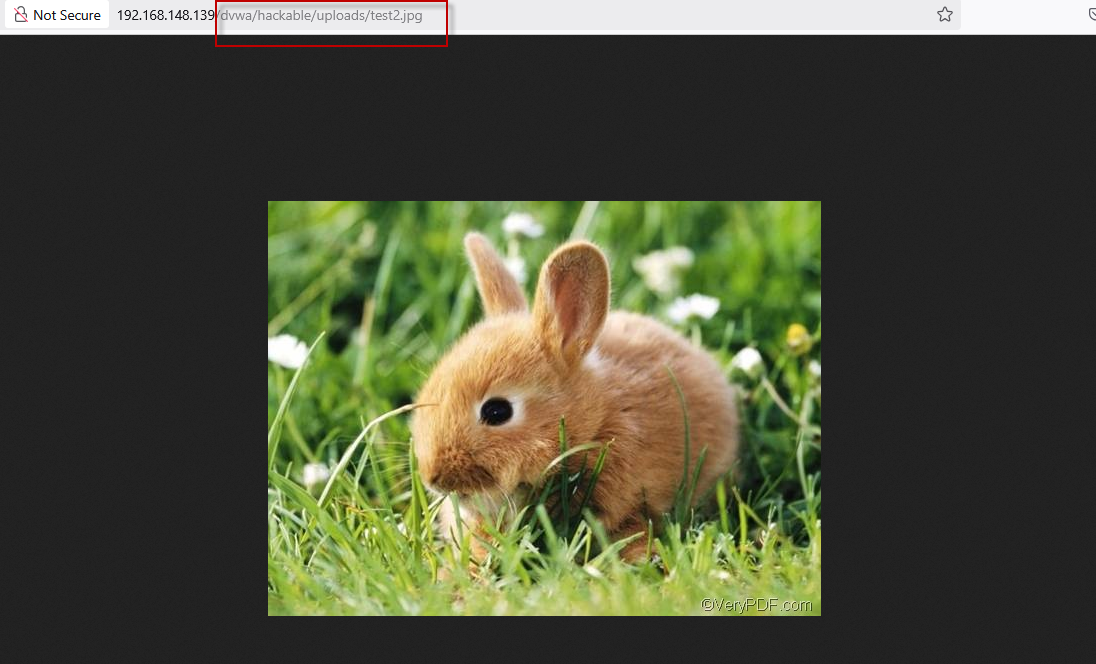
The path “../../” indicates that the file has been uploaded two directories back in the web server’s file structure. By navigating to the URL http://192.168.148.139/dvwa/hackable/uploads/test2.jpg, we can verify that the image was uploaded successfully.
Step 3: Uploading a Malicious File
Now that we know the file upload process is working, we test the vulnerability by attempting to upload a malicious PHP file. We create a file named malicious.php with the following content:
<?php system($_GET['cmd']); ?>

This code is a simple PHP script that allows the execution of commands via the cmd parameter in the URL. We then browse for this malicious file and click on the “Upload” button.
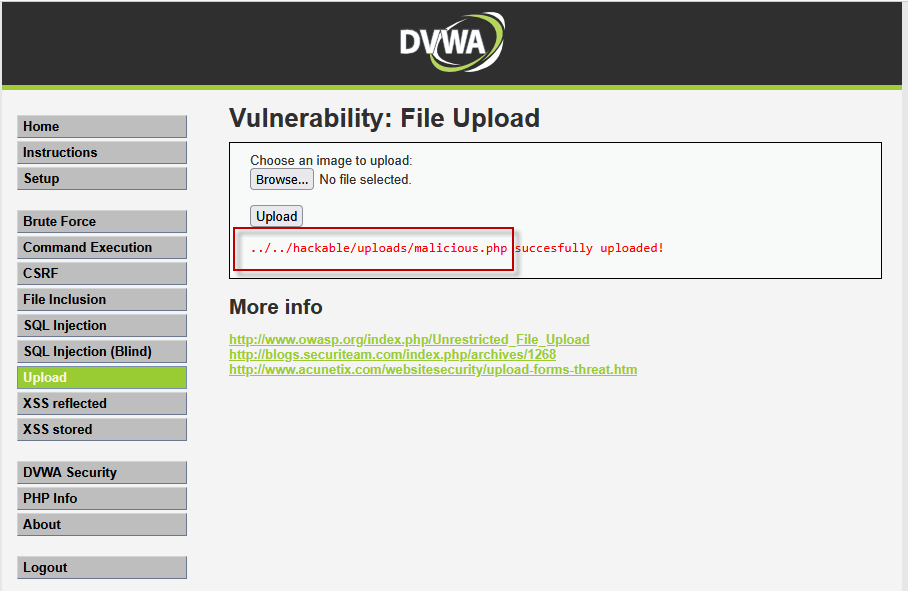
Since the security level is set to low, there is no validation to check the file extension or content. As a result, the malicious PHP file is uploaded successfully and stored at:
/hackable/uploads/malicious.php
Step 4: Accessing the Malicious File
With the malicious file uploaded, we know its location, so we try to access it by navigating to the following URL:
http://192.168.148.139/dvwa/hackable/uploads/malicious.php
Initially, we see an error because the file cannot be executed without the cmd parameter in the URL. The malicious file expects a command parameter, which allows an attacker to run arbitrary commands on the server.
Step 5: Executing Commands via the Malicious File
To test the vulnerability, we append the cmd parameter to the URL and provide a simple command such as “ls” to list the files in the current directory:
http://192.168.148.139/dvwa/hackable/uploads/malicious.php?cmd=ls
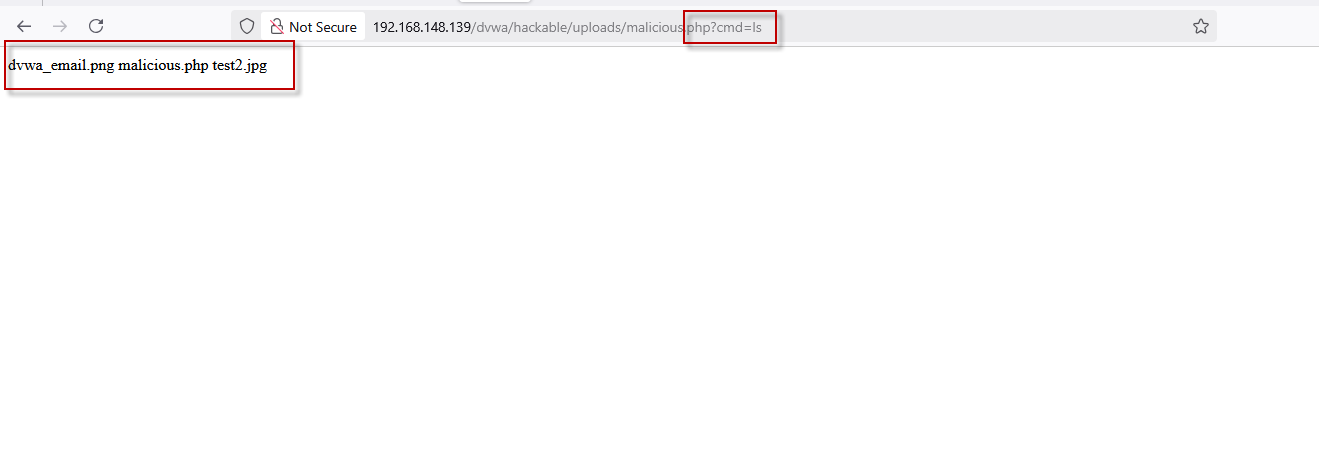
Executing this URL results in the server returning a list of files present in the directory, indicating that the malicious.php file is working as intended. The ls command is executed on the server, revealing potentially sensitive files or system details, which is a clear security issue.
Implications of the File Upload Vulnerability
The successful upload and execution of the malicious PHP file demonstrate the severity of the file upload vulnerability. Attackers can use this method to:
- Execute Arbitrary Commands: By uploading a malicious PHP file and executing commands on the server, attackers can compromise the system, gain access to sensitive information, or disrupt operations.
- Remote Code Execution (RCE): With remote code execution, attackers can run any commands they choose on the server, gaining full control over the web application or the underlying system.
- Privilege Escalation: If the web application is running with elevated privileges, attackers can exploit this vulnerability to escalate their privileges and gain unauthorized access to other systems or networks.
Mitigating File Upload Vulnerabilities
To prevent file upload vulnerabilities, developers must implement strict validation and security measures. Some key techniques include:
- File Type Validation: Always check the file type and ensure only safe file formats (such as images or PDFs) are allowed. This can be done by validating both the file extension and MIME type.
- File Size Limitation: Limit the size of files that can be uploaded to prevent large files from consuming excessive server resources or hiding malicious content.
- Renaming Uploaded Files: Rename uploaded files to prevent attackers from uploading files with malicious names (e.g., malicious.php).
- Disabling Script Execution: Disable the execution of scripts in the upload directory, or store uploaded files in a directory where they cannot be executed.
- Use of a Secure Upload Mechanism: Implement a secure upload process, such as storing uploaded files outside of the web root or using a file scanning solution to detect malicious content.
Conclusion
File upload vulnerabilities represent a significant risk to web applications, as they can lead to remote code execution, unauthorized access, and system compromise. By testing these vulnerabilities developers can identify weaknesses and apply the necessary security measures to mitigate these risks. Always ensure proper validation and secure file handling practices to protect your application from malicious attacks.

















1 Comment
Comments are closed.