
In the world of cybersecurity, attackers often use various methods to obfuscate their activities, evade detection, and cover their tracks. One such technique is steganography, a process where sensitive data is concealed within other files, such as images, audio, or video files. This practice allows for stealthy communication, making it harder for traditional security systems to detect malicious activities.
In this article, we will explore how steganography works, specifically through the Steghide tool in Kali Linux. We will demonstrate how attackers or security professionals can use Steghide to embed and extract sensitive data within an image file, providing a practical example of how steganography can be used for both offensive and defensive purposes in cybersecurity.
What is Steganography?
Steganography comes from the Greek words “steganos” meaning covered or hidden, and “grapho” meaning to write. Simply put, it is the art of hiding information within other non-suspicious media files, such as images, videos, or audio. The idea is that, even though the file appears normal to an observer, it contains hidden data.
This technique is often used by attackers for data exfiltration (stealing sensitive information from a victim’s system) or to evade detection from security monitoring tools. By embedding malicious payloads or sensitive information within seemingly harmless files, attackers can bypass security checks and move undetected across networks.
In the context of Kali Linux, a penetration testing distribution, tools like Steghide are used for performing steganographic tasks, such as embedding or extracting hidden data.
What is Steghide?
Steghide is an open-source command-line tool used for steganography in Linux-based systems. It allows users to embed arbitrary data (such as a file or message) inside an image or audio file, while still keeping the file’s structure and appearance unchanged. The tool uses a password-based encryption mechanism to ensure the hidden data remains secure.
Steghide supports several file formats for embedding data, including common image formats like JPEG, BMP, and PNG, as well as audio files like WAV. It is particularly popular in Kali Linux, a penetration testing distribution, where it is often used for educational or testing purposes.
Installing Steghide on Kali Linux
Steghide is available in the default Kali Linux repository, so it can be easily installed using the package manager. To install it, use the following command:
$ sudo apt install steghideOnce installed, you can access the tool directly from the terminal by typing steghide.
Example of Using Steghide to Hide and Extract Sensitive Data
Let’s go through a practical example of how to use Steghide to hide sensitive information within an image file and then retrieve it.
Step 1: Creating the Sensitive Data File
In our example, let’s assume we have a file called secret.txt, which contains sensitive information such as credit card data. To create this file, you can use a simple text editor or echo the contents into a file using the following command:
$ echo "Credit card data:
4012 8888 7777 7777 exp 01/31 ccv: 456
4031 9999 8888 6666 5555 exp 09/30 ccv: 123" > secret.txt
To verify that the contents of the file are correct, you can use the cat command:
$ cat secret.txt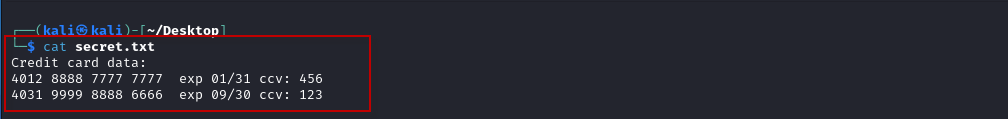
This will display the contents of secret.txt, which are the sensitive data you want to hide.
Step 2: Choosing an Image File
Next, we need an image file in which to embed the sensitive data. Let’s assume you have an image called mycomputer.jpg. This image file will serve as the carrier for our hidden data.
Step 3: Embedding the Data Using Steghide
Now that we have our secret.txt file with sensitive data and an image mycomputer.jpg, we can use Steghide to embed the contents of the text file into the image file.
To do this, run the following command:
$ steghide embed -ef secret.txt -cf mycomputer.jpg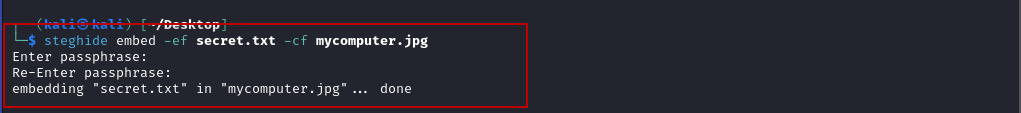
The -ef option specifies the file to be embedded (in this case, secret.txt), while the -cf option specifies the cover file (the image mycomputer.jpg). When you run this command, Steghide will ask you to enter a passphrase.
Enter passphrase: test
Re-Enter passphrase: testIn this example, we used the passphrase test. The passphrase ensures that the hidden data can only be extracted with the correct passphrase.
Step 4: Verifying the Embedded Data
At this point, the sensitive information has been successfully hidden inside the image file. However, the image will appear unchanged, and there is no obvious indication that data is hidden within it. You can verify the success of the operation by running the following command to check the properties of the image:
$ file mycomputer.jpgThis command will show the basic details of the image file, but it will not reveal any information about the hidden data.
Step 5: Extracting the Hidden Data
To retrieve the hidden data from the image file, you need to use the steghide extract command. You can do this by running the following:
$ steghide extract -sf mycomputer.jpg -xf extracted_data.txt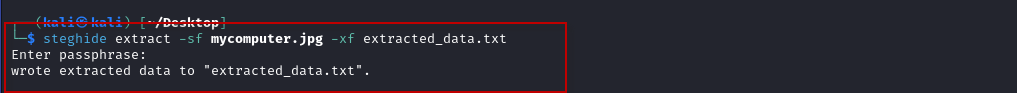
The -sf option specifies the steganographic file (in this case, mycomputer.jpg), and the -xf option specifies the file where the extracted data will be saved (extracted_data.txt).
Steghide will prompt you for the passphrase:
Enter passphrase: testIf the passphrase is correct, the hidden data will be extracted and saved to extracted_data.txt. To view the contents of the extracted file, you can use the cat command:
$ cat extracted_data.txt
This will display the sensitive data that was hidden inside the image file:
Credit card data:
4012 8888 7777 7777 exp 01/31 ccv: 456
4031 9999 8888 6666 5555 exp 09/30 ccv: 123Step 6: Conclusion
In this article, we demonstrated how Steghide can be used in Kali Linux for steganography. We showed how to hide sensitive data, such as credit card information, within an image file and how to retrieve that data using the appropriate commands. This technique can be used by attackers for data exfiltration or by security professionals to test the effectiveness of steganography detection systems.
While steganography can be a powerful tool for covert communication, it is important to understand the legal and ethical implications of using such techniques. In a penetration testing context, it can be valuable for simulating real-world attacks or protecting sensitive information. However, using steganography for malicious purposes is illegal and can result in severe consequences.
By mastering tools like Steghide, cybersecurity professionals can better understand and defend against steganographic attacks, ensuring that they can detect and prevent such covert data exfiltration methods.







2 Comments
Comments are closed.