
Web application security is more important than ever, with data breaches and cyberattacks becoming increasingly common. The OWASP Top 10 is a globally recognized list of the most critical security risks facing modern web applications. Published by the Open Web... Read more

Information gathering is the first and one of the most crucial steps in ethical hacking and cybersecurity assessments. Before launching any penetration test or vulnerability scan, cybersecurity professionals must collect as much data as possible about the target website. This... Read more

Spear phishing is a highly targeted form of phishing attack where cyber criminals impersonate a trusted individual or organization to deceive specific individuals into revealing confidential information. Unlike broad-based phishing campaigns that target large numbers of people, spear phishing attacks... Read more

In an era of heightened digital surveillance and cyber threats, privacy and security have become paramount concerns. Traditional encryption methods focus on scrambling data to make it unreadable, but steganography takes a different approach by hiding data within other, seemingly... Read more

Phishing is one of the most common and dangerous types of cyberattacks that continue to plague individuals, businesses, and organizations worldwide. It is a form of social engineering in which attackers impersonate legitimate institutions, people, or entities to deceive their... Read more

DirBuster is an essential tool for penetration testers and security professionals, allowing them to uncover hidden directories and files on web servers through brute force techniques. This multi-threaded Java application comes pre-installed in Kali Linux, a popular distribution used for... Read more

In the ever-evolving landscape of cybersecurity, the need for robust tools that can help in auditing web applications is paramount. One such tool is DIRB, a powerful web content scanner designed to uncover existing and hidden web objects. This article... Read more
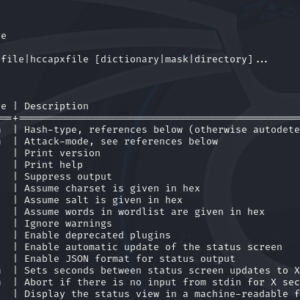
Hashcat is a powerful password recovery tool widely used for cracking hashes. It supports a variety of hash algorithms, including MD5, and can leverage wordlists to streamline the cracking process. This article will walk you through using Hashcat in Kali... Read more

In the ever-evolving landscape of web security, HTTP Host header attacks have emerged as a significant threat. These attacks exploit vulnerabilities in how websites handle HTTP Host headers, leading to various security issues, including password reset poisoning. This article delves... Read more
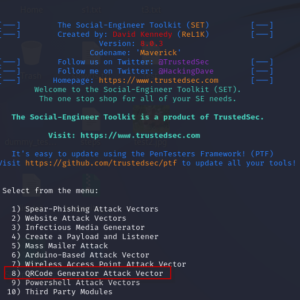
In the world of cybersecurity, social engineering is a powerful tool for exploiting human psychology to gain unauthorized access to systems and data. One of the most intriguing methods within the Social Engineering Toolkit (SET) is the QRCode Generator Attack... Read more