
In today’s digital age, ensuring the security of web applications is paramount, especially when sensitive information such as passwords, credit card details, or personal data is being exchanged. One of the key components in safeguarding these communications is SSL/TLS (Secure Sockets Layer/Transport Layer Security), which encrypts data during transmission. However, vulnerabilities in SSL/TLS configurations can leave websites and users open to potential attacks. Kali Linux, a popular penetration testing operating system, offers various tools to identify and resolve these vulnerabilities. One such tool is TestSSL—a command-line tool designed specifically for SSL/TLS testing.
In this article, we’ll explore how to use TestSSL on Kali Linux to scan SSL/TLS vulnerabilities in websites and provide instructions on performing different types of scans. By the end, you’ll understand how to use this powerful tool to enhance the security of your websites and systems.
What is TestSSL?
TestSSL is a comprehensive SSL/TLS scanning tool that performs in-depth assessments of SSL/TLS configurations on web servers. It evaluates various aspects such as supported protocols, cipher suites, certificates, and overall SSL/TLS configuration security. TestSSL helps identify potential weaknesses that could be exploited by attackers, such as outdated or insecure protocols, weak ciphers, and misconfigured certificates.
TestSSL supports the detection of several SSL/TLS vulnerabilities, including:
- SSLv2/SSLv3 protocol support (outdated and insecure)
- Weak cipher suites (ciphers that can be cracked or are inefficient)
- Heartbleed vulnerability
- Insecure SSL/TLS versions (e.g., TLS 1.0, TLS 1.1)
- Misconfigured certificates and expired certificates
Kali Linux comes pre-installed with TestSSL, making it a valuable tool for security experts, penetration testers, and anyone concerned with website security.
Installing TestSSL on Kali Linux
TestSSL is typically pre-installed in Kali Linux, but if it’s missing for some reason, you can install it manually with the following commands:
sudo apt update
sudo apt install testssl.shOnce installed, you can begin using TestSSL from the command line interface.
Basic TestSSL Usage
Checking Available Options
To begin using TestSSL, open the terminal on your Kali Linux machine and type the following command:
$ testssl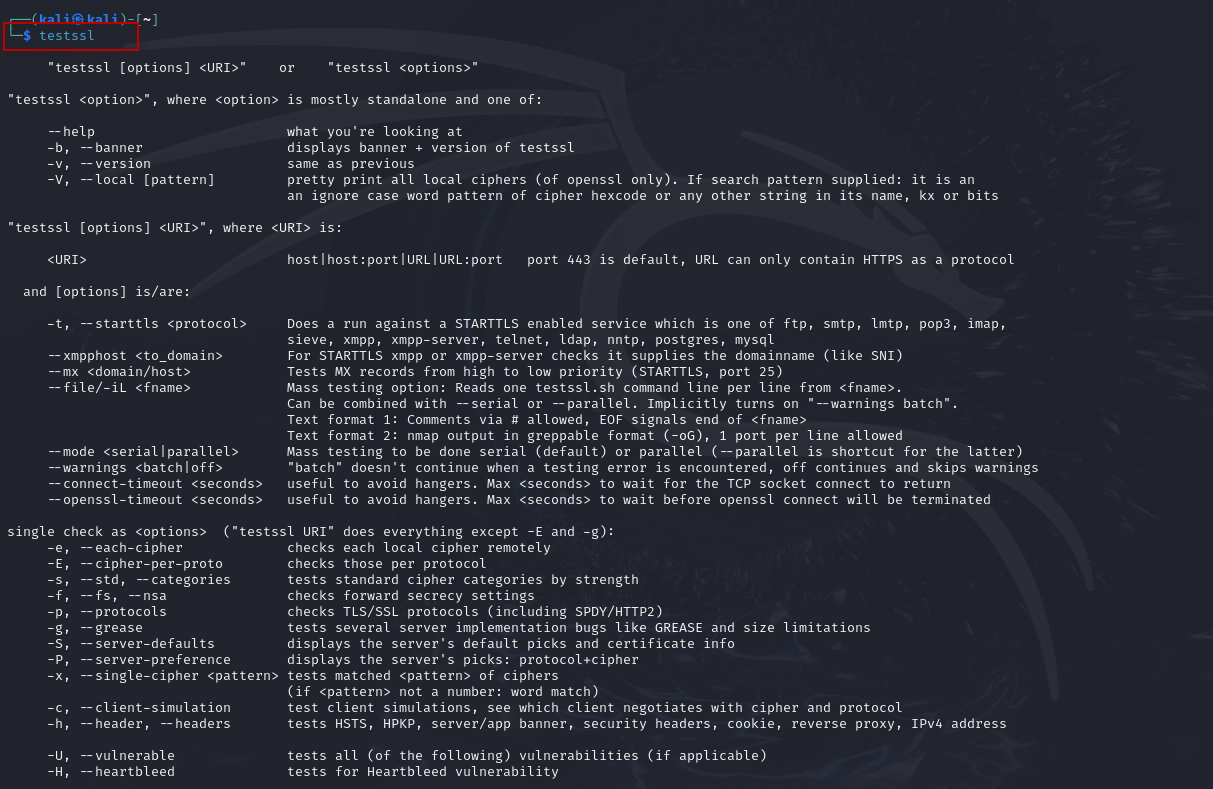
This command will display a list of available options and parameters for TestSSL. It includes various commands that can be used to customize your SSL/TLS scan, including options to specify specific vulnerabilities to test for, scan depth, verbosity, and more.
Scanning a Website for SSL/TLS Vulnerabilities
One of the most common use cases of TestSSL is scanning a website over SSL/TLS to identify potential vulnerabilities in its configuration. This can be done using the following command format:
$ testssl https://www.example.com/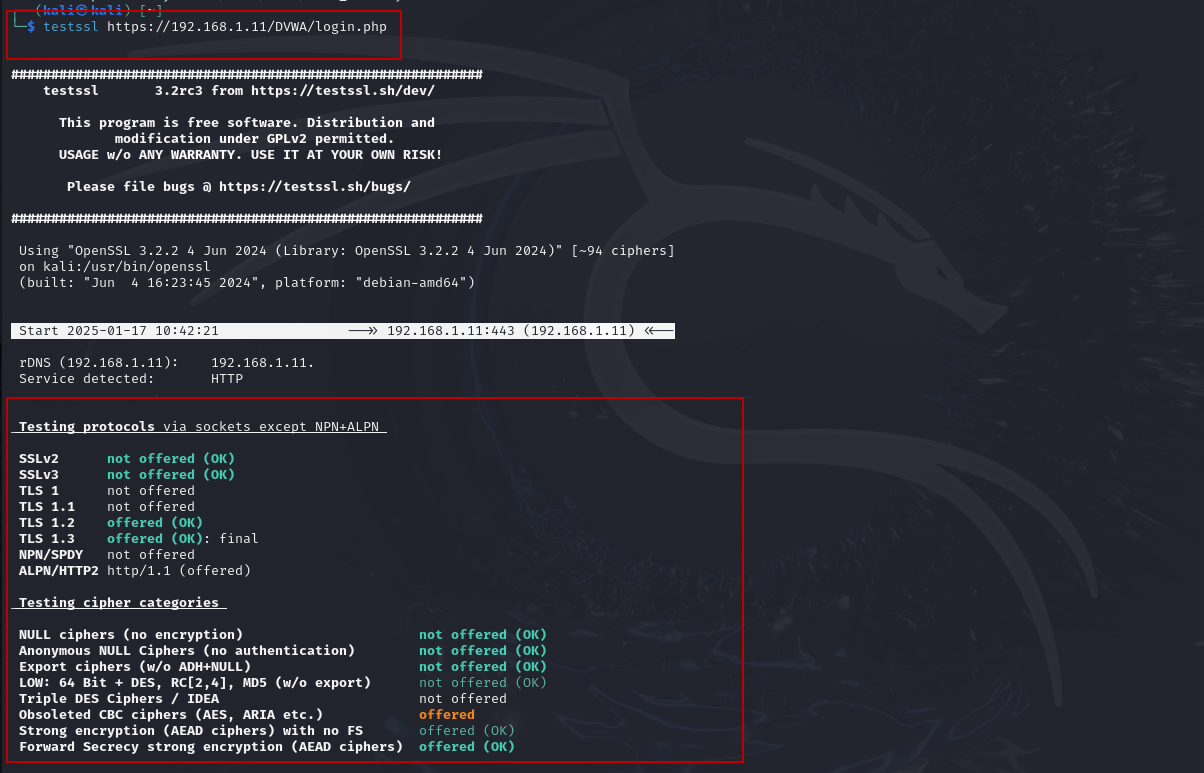
Replace www.example.com with the actual domain of the website you want to scan. This command will initiate a scan on the specified website and provide a comprehensive report of its SSL/TLS configuration, including:
- Supported SSL/TLS protocols (e.g., SSLv2, SSLv3, TLS 1.0, TLS 1.2, TLS 1.3)
- Available cipher suites (strong and weak ciphers)
- Certificate details (validity period, issuer, etc.)
- Potential vulnerabilities (such as Heartbleed or POODLE etc..)
- General security best practices (whether Perfect Forward Secrecy is enabled, for instance)
The output of this scan will allow you to determine if your website’s SSL/TLS configuration is secure or if improvements are needed.
Scanning for Vulnerabilities Only
While a full scan provides a comprehensive overview of the SSL/TLS configuration, there are times when you may want to focus specifically on vulnerabilities, without the extra information about certificates and protocols. To do this, TestSSL offers a vulnerability-specific scan option. Use the following command to perform a vulnerability-only scan:
$ testssl -U https://www.example.comThe -U flag instructs TestSSL to scan only for vulnerabilities, such as:
- Known vulnerabilities like Heartbleed ,POODLE,BEAST,LOGJAM etc..
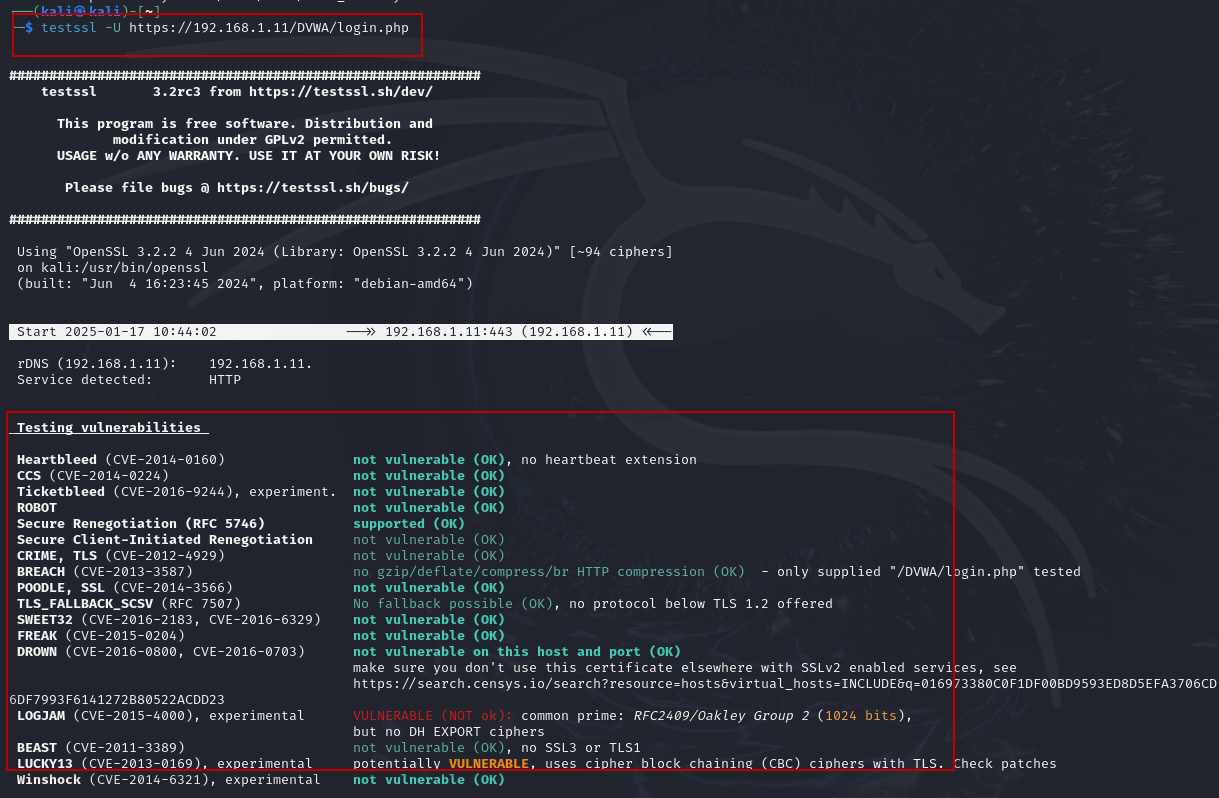
This targeted scan will generate a report focused on any critical security weaknesses that should be addressed to improve the SSL/TLS security posture of the website.
Understanding the Results
TestSSL produces detailed output after scanning a website. Below are some of the critical sections of the output and what they mean:
- SSL/TLS Protocol Support: TestSSL will list all SSL/TLS versions supported by the server, such as SSLv2, SSLv3, TLS 1.0, TLS 1.2, and TLS 1.3. Older versions like SSLv2 and SSLv3 should be disabled because they are insecure and vulnerable to attacks like POODLE and BEAST.
- Cipher Suites: A cipher suite is a combination of algorithms used to secure network connections. TestSSL checks whether the server supports strong cipher suites (e.g., those using AES encryption) or weak ones (e.g., those using RC4). Weak ciphers can be exploited, so it’s essential to use only strong ones.
- Perfect Forward Secrecy (PFS): PFS ensures that session keys are not compromised even if the private key of the server is exposed later. TestSSL checks if the server supports PFS and provides an analysis of its importance.
- Certificate Information: The SSL certificate is the cornerstone of website encryption. TestSSL will show whether the certificate is valid, whether it’s self-signed, whether it has expired, and who the issuer is.
- Known Vulnerabilities: TestSSL checks for known SSL/TLS vulnerabilities, including the Heartbleed vulnerability (CVE-2014-0160), which allows attackers to read sensitive information from memory. If a vulnerability is detected, TestSSL will display relevant details to help mitigate the risk.
Advanced Features and Customization
TestSSL also offers advanced features to fine-tune your scans. Some of the commonly used options include:
- HTML Output: If you prefer to have the results in HTML format for easier reading or sharing, you can generate an HTML report with the
--htmloption:
$ testssl --html https://www.example.com- Scan particular vulnerabilities like:
Testing for Heartbleed vulnerability
$ testssl -H https://example.com
Testing for SSLv3 POODLE vulnerability
$ testssl -O https://example.comConclusion
TestSSL is an essential tool for security professionals and website administrators who want to ensure their SSL/TLS configurations are secure. By regularly scanning websites with TestSSL, you can identify vulnerabilities and improve the overall security posture of your site.
Whether you perform a full scan to get a comprehensive overview of SSL/TLS settings or use the -U option to check for specific vulnerabilities, TestSSL makes it easy to identify and address potential weaknesses in your encryption setup. On Kali Linux, it’s a straightforward yet powerful tool that helps keep your communications safe from threats.
Make sure to regularly audit your SSL/TLS configuration and address any security issues to protect your users’ data and privacy.









