
In the ever-evolving landscape of cybersecurity, the need for robust tools that can help in auditing web applications is paramount. One such tool is DIRB, a powerful web content scanner designed to uncover existing and hidden web objects.
This article will delve into what DIRB is, how it operates, its purpose in professional web application auditing, and how to effectively utilize it, especially within the Kali Linux environment.
What is DIRB?
DIRB is an open-source web content scanner that uses a dictionary-based attack to discover hidden directories and files on web servers. By sending a series of requests derived from a specified wordlist, DIRB analyzes the responses from the server to identify accessible resources.
This tool is not designed to find vulnerabilities but rather to help locate web content that may be obscured from public view.
DIRB is particularly useful for web application security testing, as it fills in gaps that traditional vulnerability scanners might overlook. Its primary objective is to assist security professionals in conducting thorough audits of web applications, ensuring that no hidden endpoints go undetected.
How DIRB Works
DIRB operates by performing directory and file enumeration. It sends requests to the target web server based on the entries in the chosen wordlist and checks the server’s responses. By analyzing HTTP status codes (such as 200, 404, 403, and 302) and file sizes, DIRB identifies which resources are accessible.
Installation and Syntax
DIRB comes pre-installed in Kali Linux, a popular distribution for penetration testing. To use DIRB, the basic syntax is:
dirb <target_url> [<wordlist_file>] [options]This allows users to specify the target URL and optionally a custom wordlist along with various operational parameters.
Basic DIRB Commands
For demonstration, we’ll use the Damn Vulnerable Web Application (DVWA) website. Below are some basic commands that can be executed in the Kali Linux terminal.
1. Check the Syntax and Options: Start by typing dirb in the terminal. This command will display the available options and syntax to familiarize yourself with the tool.
dirb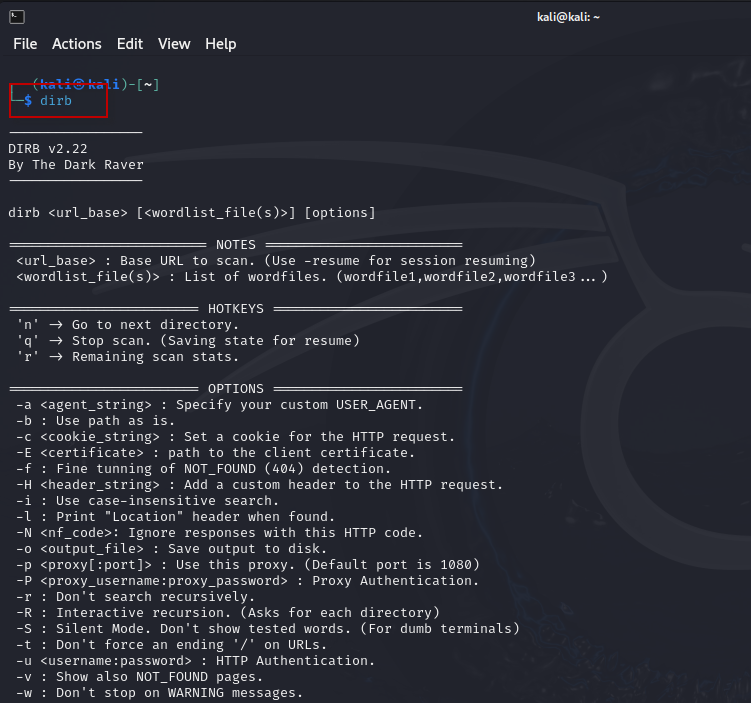
2. Basic Scan: Conduct a basic scan on the target website using the default wordlist.
dirb http://192.168.1.11/DVWA/
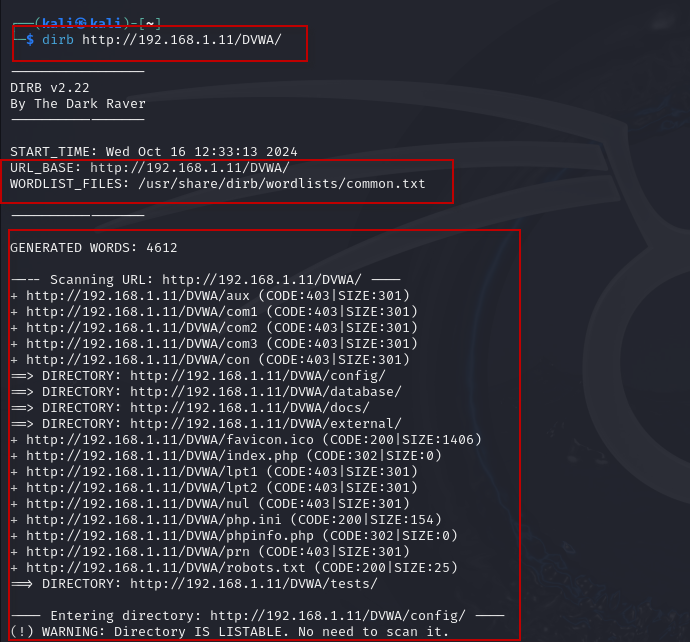
This command will utilize DIRB’s default wordlist to check for directories and files, analyzing the responses for different HTTP status codes.
3. Explore Inbuilt Wordlists: DIRB comes with several preconfigured wordlists. Navigate to the directory containing these files:
cd /usr/share/dirb/wordlists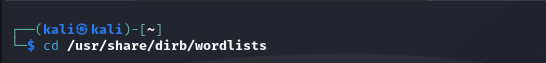
To view the available wordlists, use:
ls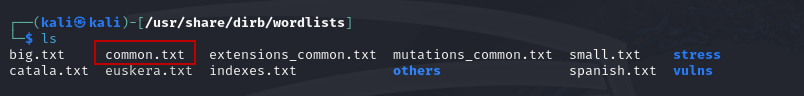
The default wordlist used by DIRB is common.txt.
4. Using Custom Wordlists: If you want to target a specific technology or web server, you can specify a different wordlist. For example, to scan an Apache web server:
dirb http://192.168.1.11/ /usr/share/dirb/wordlists/vulns/apache.txt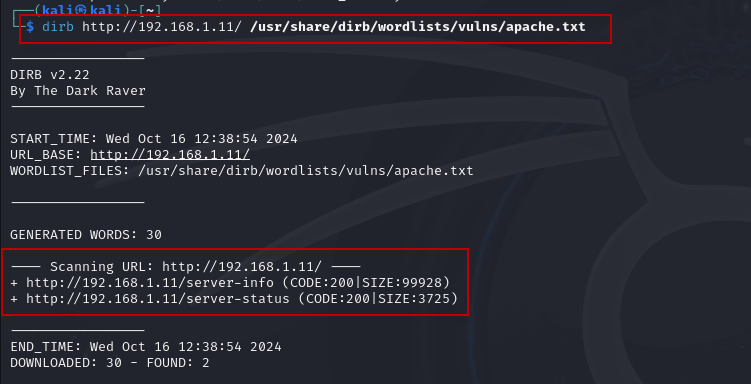
5. Saving Output to Disk: To save the results of your scan to a file for later analysis, use the -o option:
dirb http://192.168.1.11/DVWA/ -o result.txt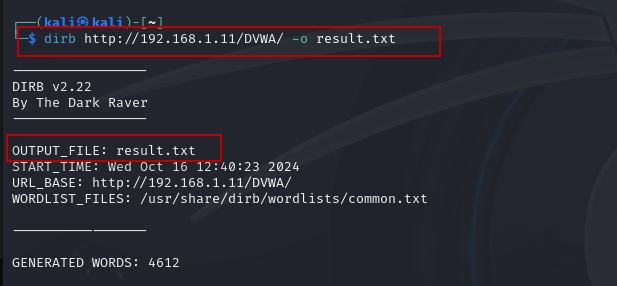
You can then read the output with:
cat result.txt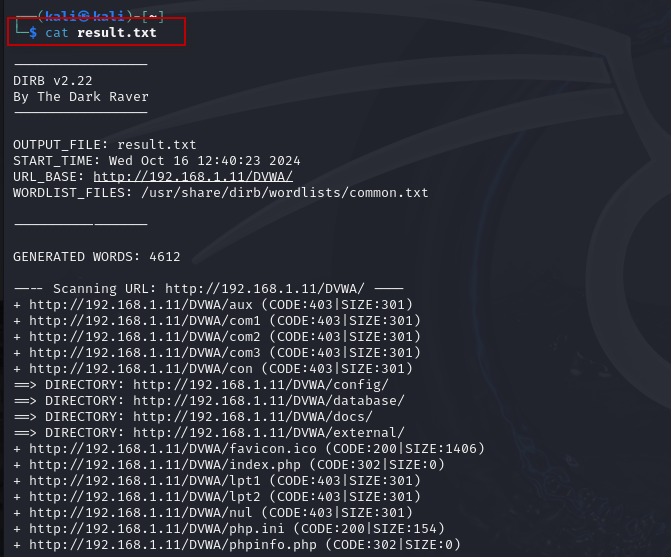
6. Appending Extensions: If you want to search specifically for files with a certain extension (e.g., .php), use the -X option:
dirb http://192.168.1.11/DVWA/ -X .php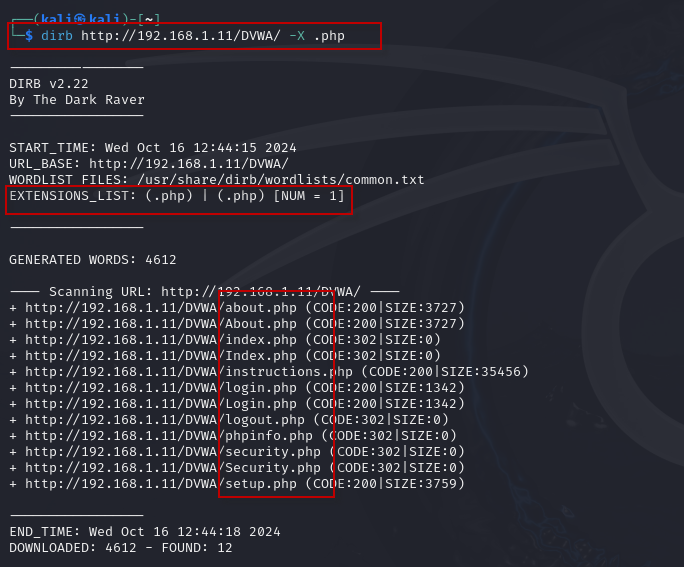
7. Ignoring Specific HTTP Codes: To exclude responses with certain status codes, such as 302 (Found), you can use the -N option:
dirb http://192.168.1.11/DVWA/ -N 302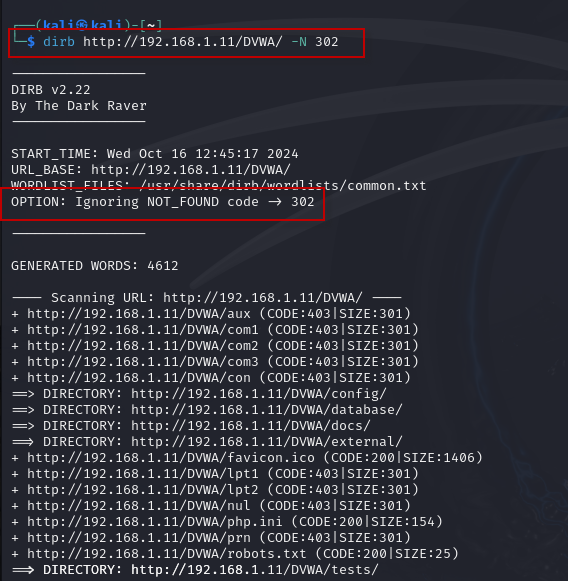
8. Preventing Recursive Searches: In scenarios where you need to limit the search to the first level of directories, use the -r option to disable recursive scanning:
dirb http://192.168.1.11/DVWA/ -r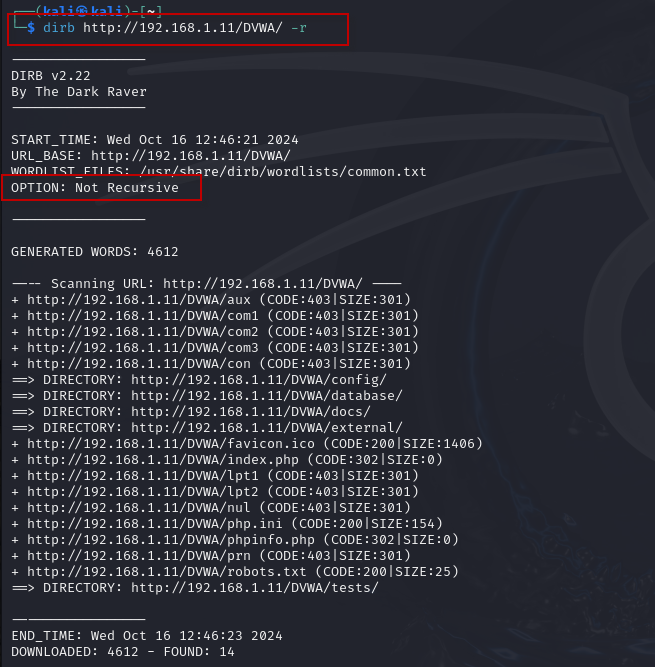
9. Adding Delays: To prevent overwhelming the server with requests, you can add a delay between requests using the -z option:
dirb http://192.168.1.11/DVWA/ -z 100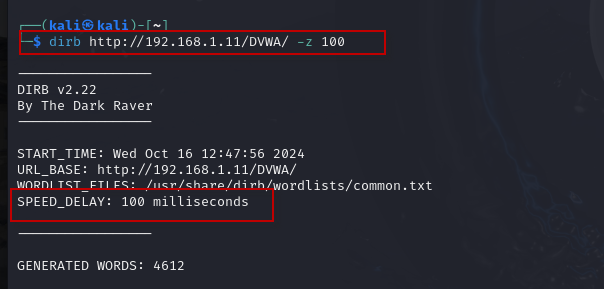
10. Ignoring Warnings: Sometimes, you might encounter warning messages that are not critical. To continue scanning despite these warnings, use the -w option:
dirb http://192.168.1.11/DVWA/ -w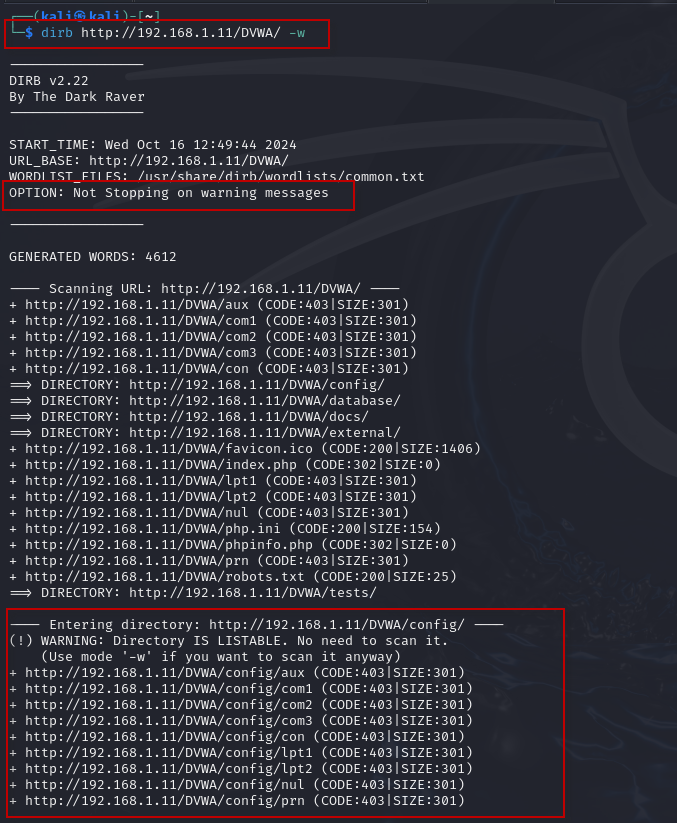
11. HTTP Authentication: If the target web application requires authentication, you can include credentials using the -u option:
dirb http://192.168.1.11/DVWA/login.php -u admin:passwordConclusion
DIRB is an invaluable tool for web application security testing, enabling security professionals to uncover hidden web content that might otherwise go unnoticed. By leveraging its dictionary-based scanning capabilities, DIRB complements traditional vulnerability scanners and enhances the overall security posture of web applications.
By following the commands and practices outlined in this article, you can effectively utilize DIRB in your security assessments, ensuring a thorough evaluation of web applications. Whether you are an experienced penetration tester or a newcomer to cybersecurity, mastering DIRB will enhance your toolkit for web content discovery and auditing.










2 Comments
Comments are closed.