
Brute force attacks are one of the most basic yet effective ways of testing web application vulnerabilities. In this tutorial, we will demonstrate how to perform a brute force attack on a vulnerable web application using Burp Suite. Specifically, we will use the Damn Vulnerable Web Application (DVWA) lab to exploit the brute force vulnerability. Follow this step-by-step guide to perform the attack and gain unauthorized access.
Prerequisites
Before diving into the brute force attack, make sure you have the following tools and setup in place:
- Burp Suite – A popular web application security testing tool that can intercept and modify HTTP/HTTPS requests.
- DVWA – A vulnerable web application designed to help security professionals practice penetration testing techniques.
- A browser configured to use Burp Suite as a proxy to capture and analyze web traffic.
- Dummy Username and Password Lists – You will need these lists to try different username and password combinations during the attack.
Step 1: Access DVWA and Prepare for the Attack
First, open the DVWA application in your browser. Login to DVWA, and once you’re inside the application, you should see a menu on the left side. Look for the Brute Force link and click on it. This will open a username and password form where we will initiate our brute force attack.
Step 2: Set Up Burp Suite Proxy
Now that you’ve reached the login form, we need to configure Burp Suite to intercept the request. Here’s how you can do it:
- Open Burp Suite and navigate to the Proxy tab.
- Ensure that the Intercept feature is turned on. This will allow Burp Suite to capture HTTP requests sent from your browser.
- Next, configure your browser to use Burp Suite as a proxy. By default, Burp Suite listens on 127.0.0.1:8080. Set the browser’s proxy settings to match this configuration.
- Once you’ve configured the proxy, any request you send through the browser will be captured by Burp Suite.
Step 3: Capture the Form Submission
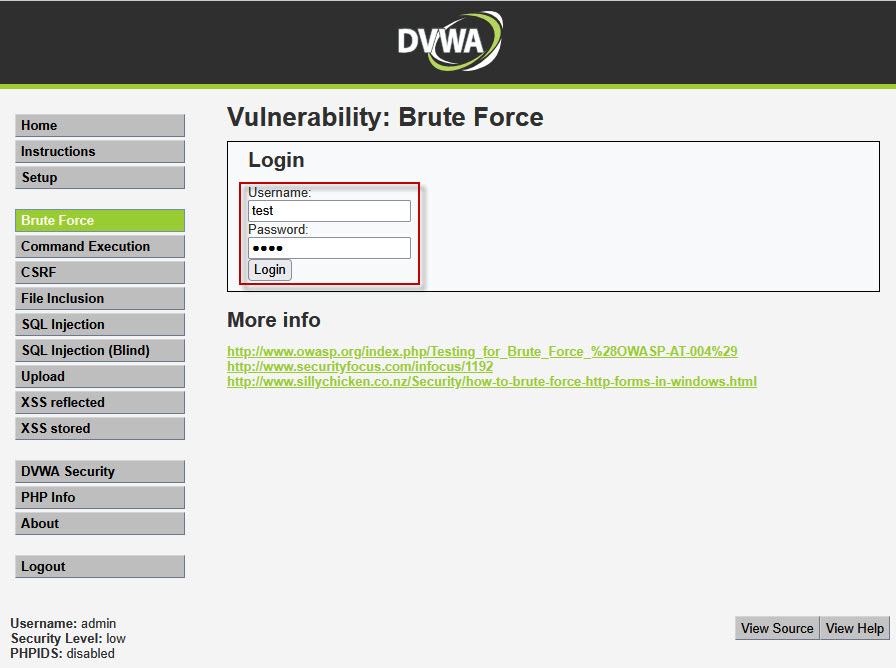
Now, in your browser, enter a dummy username and password in the DVWA form and click the Submit button. Burp Suite will capture this request as it’s sent to the server.
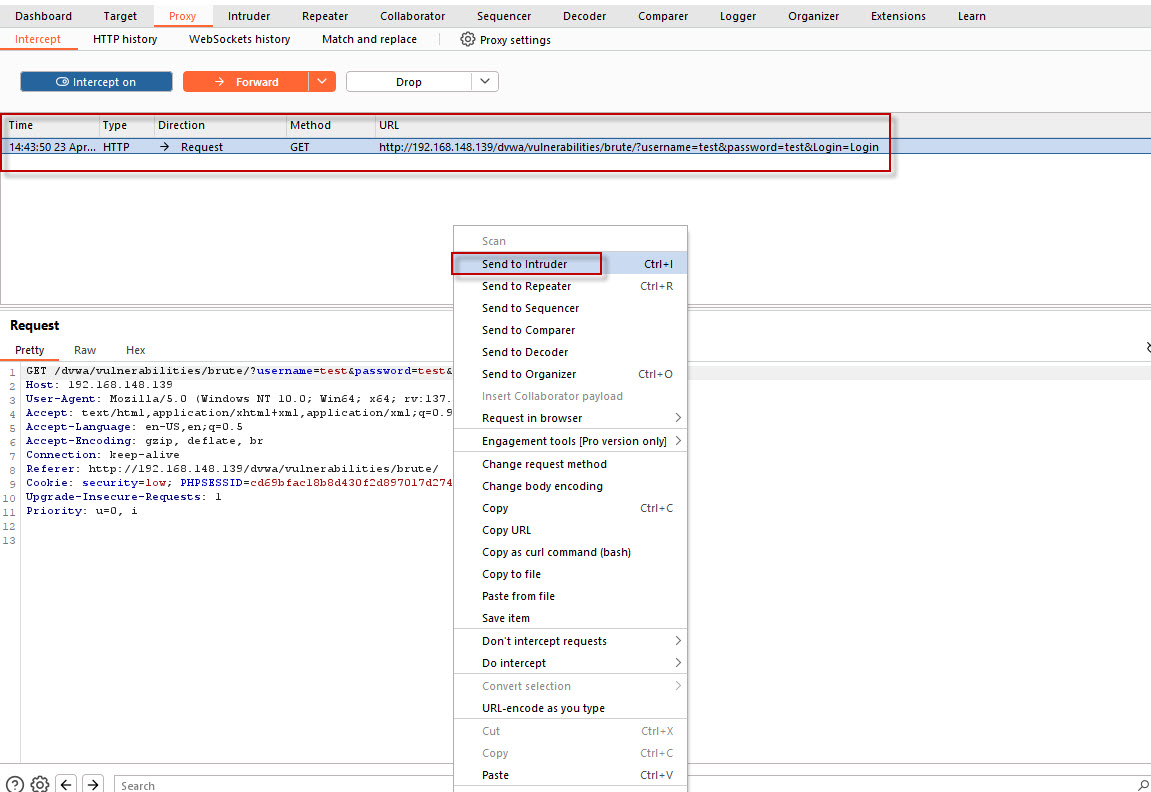
Go back to Burp Suite, and you should see the captured request under the Proxy > Intercept tab. Right-click on the request and select Send to Intruder. This will allow you to modify the request and use Burp Suite’s Intruder tool to perform the brute force attack.
Step 4: Configure Burp Suite Intruder for Brute Force Attack
Switch to the Intruder tab in Burp Suite to set up the brute force attack. Here’s how you can configure it:
- Select Attack Type: In the Intruder tab, you’ll see several attack types. Choose the Cluster Bomb attack type. This is useful when you want to test multiple combinations of usernames and passwords.
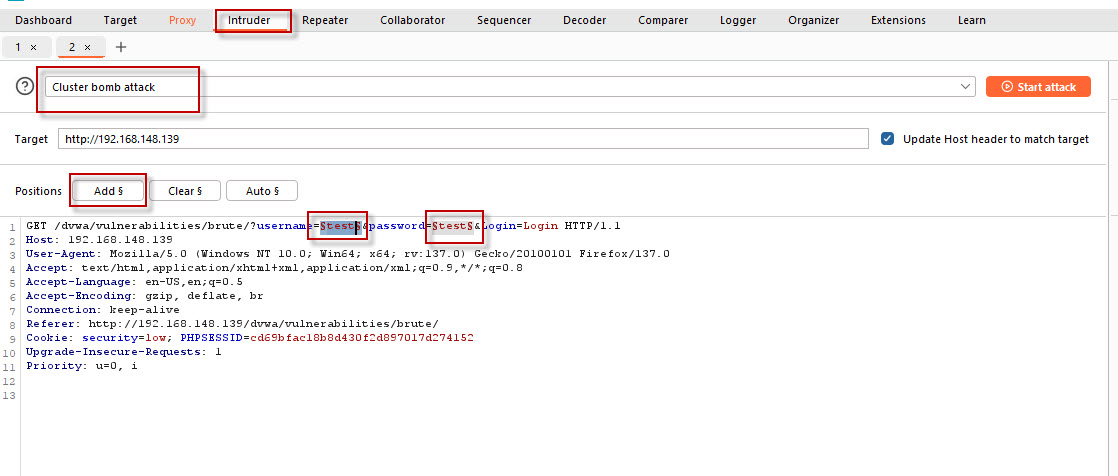
- Mark Positions: Now, Burp Suite needs to know which parts of the request should be tested with the payload lists. In the request window, highlight the username and password fields. Once selected, click the Add button to mark these positions as the ones to be attacked.
- Upload Payload Lists: Next, you need to upload your dummy lists for the attack.
Username List: Double-click the username field in the request to select its position. On the right side of Burp Suite, you will see a Payload section. Click the Upload button and browse for a simple username list that you have created. This list will contain the usernames you want to test.
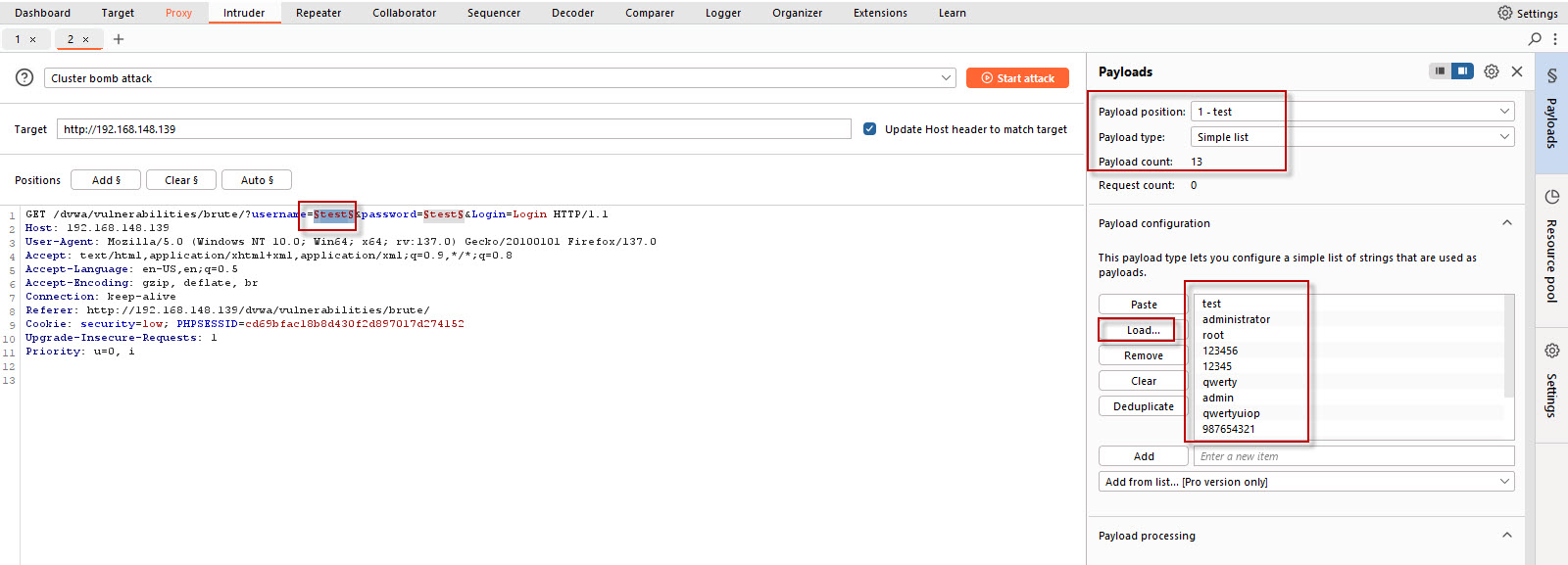
Password List: Similarly, click on the password field and upload the password list you created. This list will contain various password combinations to test against the usernames.

Step 5: Launch the Brute Force Attack
Once you’ve uploaded both the username and password lists, you’re ready to start the attack. To do this:
- Click on the Start Attack button in Burp Suite. Burp Suite will now start sending requests to the DVWA login form, one by one, testing different combinations of usernames and passwords from the lists you uploaded.
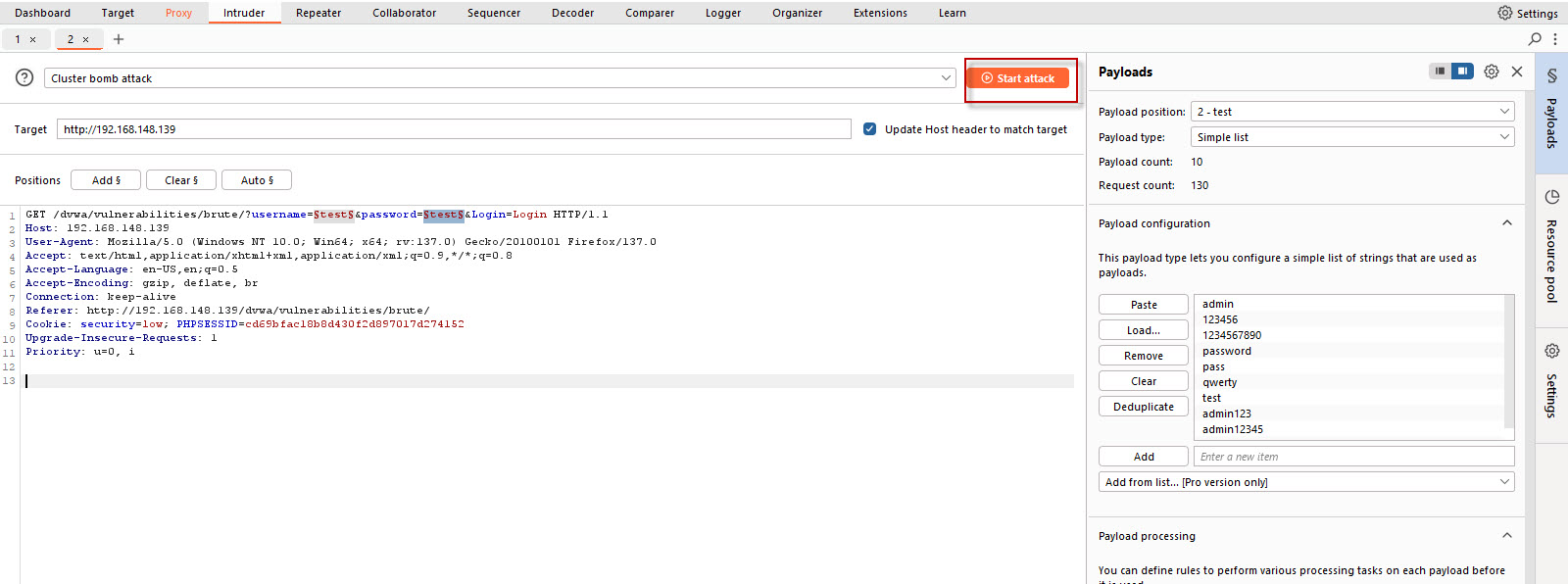
Step 6: Analyze Attack Results
As the attack runs, Burp Suite will display the results of each request, including the HTTP response code and the length of the response. Pay close attention to the length field in the response.
- Look for any response that has a noticeably different length compared to the others. A different length could indicate that the request was successful or that the server responded differently to the valid credentials.
- Once you find a response with a distinct length, take note of the username and password combination that was used in that request.
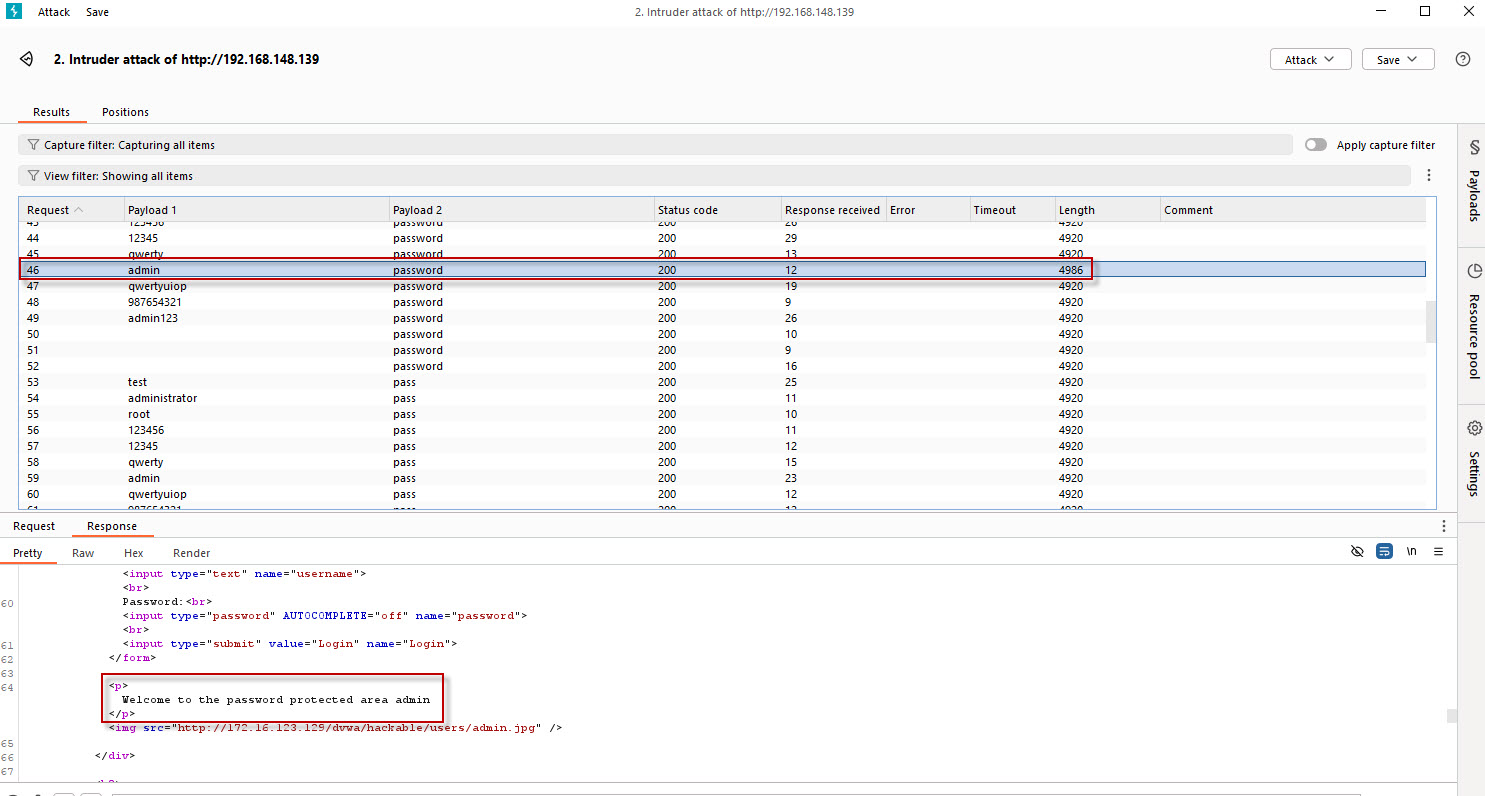
Step 7: Test the Valid Credentials
Now that you have identified a valid username/password pair based on the response length, go back to the DVWA login form and enter the username and password combination you discovered.
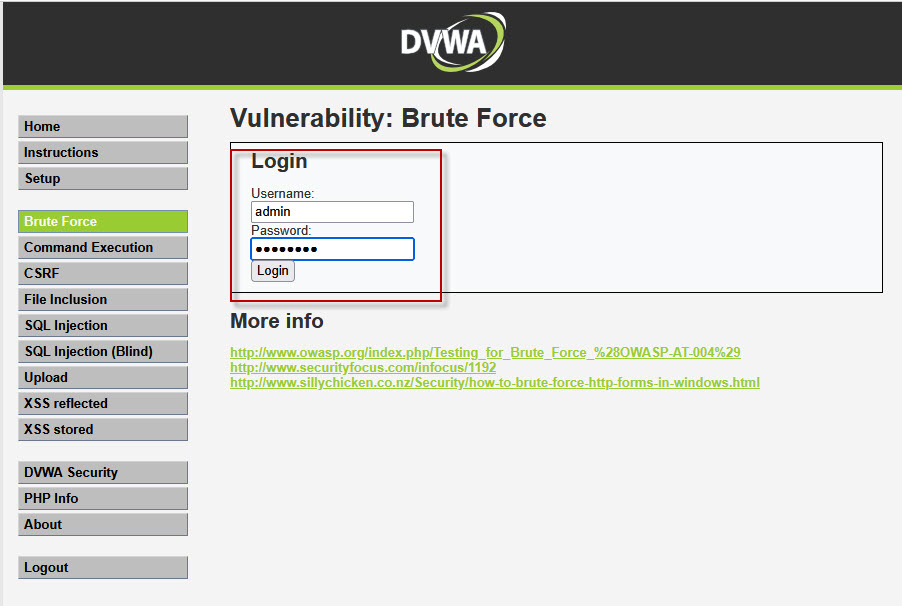
If everything was set up correctly, you should now be able to successfully log in to the application, bypassing the login page.

Conclusion
In this tutorial, we demonstrated how to perform a brute force attack using Burp Suite on the DVWA application. By using the Cluster Bomb attack type and analyzing the response lengths, we were able to identify valid username and password combinations and gain unauthorized access to the web application.
Remember, brute force attacks can be time-consuming and inefficient, so it’s always a good practice to use other methods such as password spraying or dictionary attacks when working with real-world applications. Additionally, it’s important to always have permission before testing any web application for vulnerabilities.










3 Comments
Comments are closed.