WPScan is a powerful, free, and open-source tool designed specifically for scanning WordPress websites for security vulnerabilities. It is one of the most widely used tools by ethical hackers and penetration testers to assess the security posture of WordPress installations. Since Kali Linux is a preferred platform for security testing, WPScan comes pre-installed or can be easily installed on it.
In this guide, we’ll explore how to set up, update, and use WPScan effectively on a Kali Linux system, along with real-world command examples for practical use.
What is WPScan?
WPScan is a command-line tool built for scanning WordPress websites. It checks for:
- Outdated WordPress versions
- Vulnerable plugins and themes
- Enumerates usernames
- Performs brute-force attacks (with permission)
- Configuration leaks and exposed files
WPScan uses the WPScan Vulnerability Database to fetch up-to-date information on known security issues.
Installing and Updating WPScan on Kali Linux
Although WPScan comes pre-installed in most Kali Linux distributions, you can install or update it manually using:
$ sudo apt update
$ sudo apt install wpscanTo update its vulnerability database:
$ wpscan --updateWPScan Command Line Usage and Examples
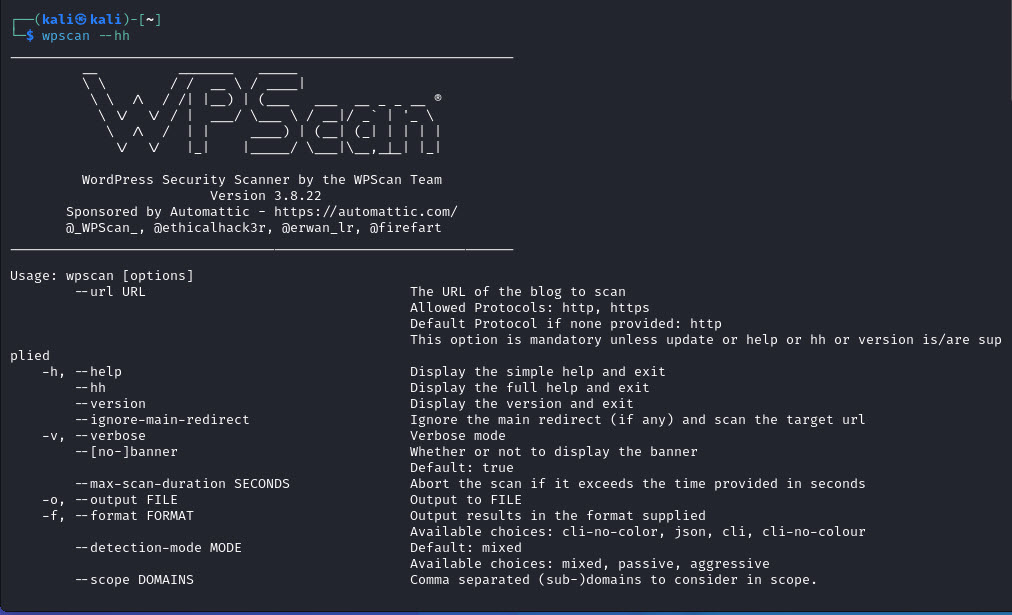
You can get the complete help menu using:
$ wpscan --hh1. Scan a WordPress Website
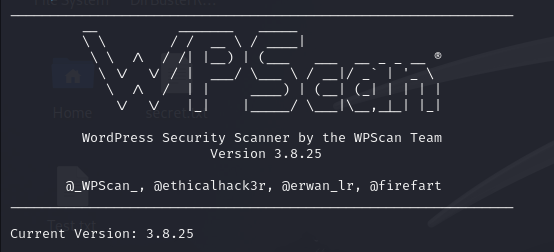
To perform a basic vulnerability scan on a WordPress site:
$ wpscan --url https://example.com
This scans the target for general vulnerabilities, plugins, themes, and exposed configuration files.
2. Output Scan Results to a File
You can export the scan results to a file (e.g., for reporting or analysis):
$ wpscan --url https://example.com/ -o /home/kali/Desktop/output.txt
This is helpful for keeping a record of your penetration tests.
3. Force Scan a Website
Use --force to bypass warnings and continue scanning, such as when a website isn’t clearly identified as WordPress but you still want to scan it:
$ wpscan --url https://example.com/ --force4. Enumerate WordPress Users
To find usernames (which can be later used for brute-force attacks):
$ wpscan --url https://example.com -e uYou can also enumerate plugins (vp) and themes (vt):
$ wpscan --url https://example.com -e vp,vt5. Use API Token for Full Vulnerability Data
Register for a free API token at https://wpscan.com. Then:
$ wpscan --url https://example.com --api-token YOUR_API_TOKENThis unlocks access to detailed plugin and theme vulnerability data.
6. Brute Force WordPress Logins (Authorized Testing Only)
If you have permission, test for weak login credentials:
$ wpscan --url https://example.com -U users.txt -P passwords.txtNote: Only use this command on systems you own or have explicit permission to test.
WPScan Best Practices
- Always update WPScan and its database before running a scan.
- Never scan websites without permission — it is illegal and unethical.
- Use API tokens to get complete vulnerability data.
- Combine WPScan with other tools like Nmap, Nikto, or Burp Suite for broader assessments.
- Use output files to document your findings for later analysis or reporting.
Real-World Use Case
Let’s say you’re testing a website called https://testsite.com. Here’s a full scan sequence:
$ wpscan --url https://testsite.com --api-token YOUR_API_TOKEN -e u,vp,vt --force -o /home/kali/Desktop/testsite_scan.txtThis command:
- Scans the site with API-powered vulnerability data
- Enumerates users, plugins, and themes
- Forces scanning even if detection is uncertain
- Saves the result to a file for review
Conclusion
WPScan is an essential WordPress security scanner, and using it on Kali Linux gives ethical hackers and developers the edge they need to detect and fix vulnerabilities before attackers do. With its powerful features and up-to-date vulnerability database, WPScan should be part of every security toolkit.
Whether you’re a security researcher or a WordPress site admin, WPScan can help you strengthen your defenses with minimal setup and maximum effectiveness.