NMAP, short for Network Mapper, is an essential and powerful network scanning tool available in Kali Linux. With its extensive range of features and flexibility, Nmap has become the go-to tool for network administrators, security professionals, and ethical hackers alike. In this comprehensive guide, we will explore the capabilities of Nmap and provide an in-depth understanding of its usage in Kali Linux. We will cover various Nmap commands and demonstrate practical examples to highlight its effectiveness in network reconnaissance, vulnerability scanning, and network mapping.
NMAP comes pre-installed with Kali Linux , making it easily accessible for users. However, it’s essential to keep Nmap updated to leverage the latest features and vulnerability signatures.
Basic Nmap commands based on key features:
Nmap offers a wide range of features that make it indispensable for network security professionals. Some key features include :
- Host Discovery : Host discovery is the fundamental step in any network assessment. Nmap provides several techniques to identify live hosts within a network. For instance, the “-sP” command performs a ping scan to determine which hosts are online. Here’s an example:
Command : nmap -sP 192.168.148.130

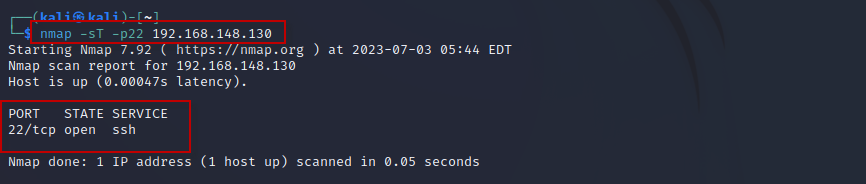
- Port Scanning : Port scanning enables the identification of open ports on target systems, revealing potential entry points for attackers. Nmap offers a variety of scanning options, including TCP, UDP, SYN, and others. The “-sT” command conducts a TCP scan on specific ports. Consider the following example:
Command : nmap -sT -p22 192.168.148.130
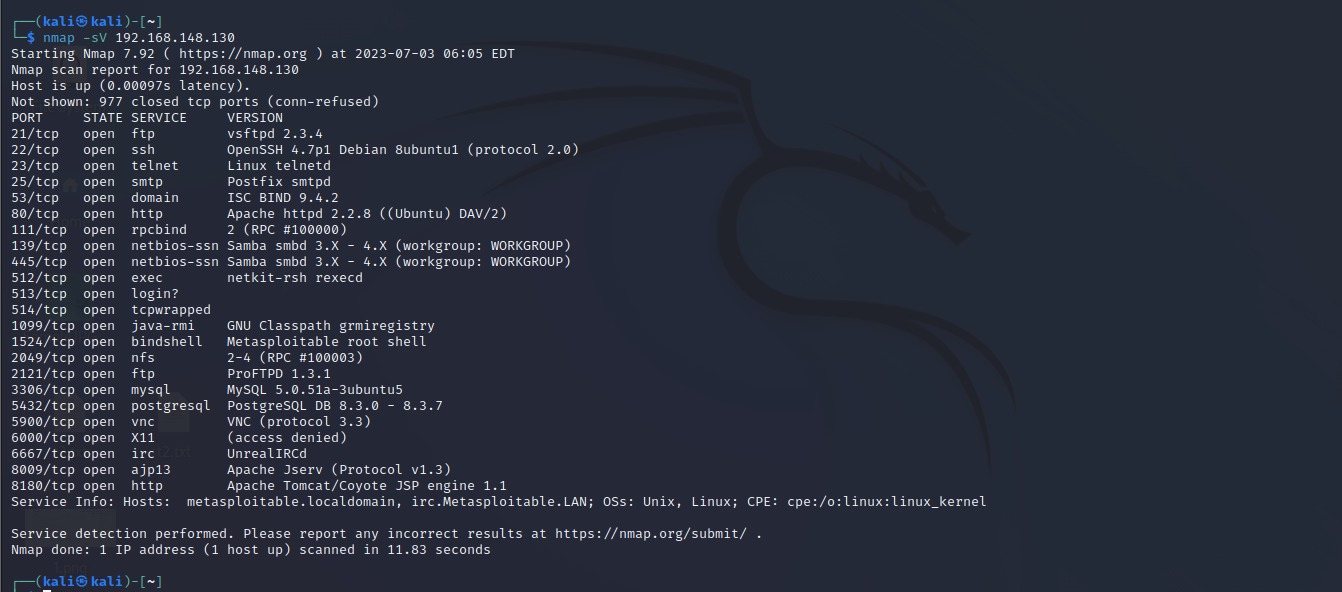
- Version Detection : Knowing the software versions running on target systems is crucial for assessing vulnerabilities and ensuring proper security measures. Nmap’s version detection feature (“-sV”) allows you to retrieve this information. Here’s an example of scanning a specific IP address for version detection:
Command : nmap -sV 192.168.148.130
- Scriptable Interaction : Nmap offers an extensive scripting engine that allows users to create and execute scripts to automate tasks and perform advanced network scanning. These scripts, written in various programming languages, can be used to gather specific information, detect vulnerabilities, or even launch attacks. For example, the following command executes an HTTP vulnerability scan:
Command : nmap –script vuln 192.168.148.130

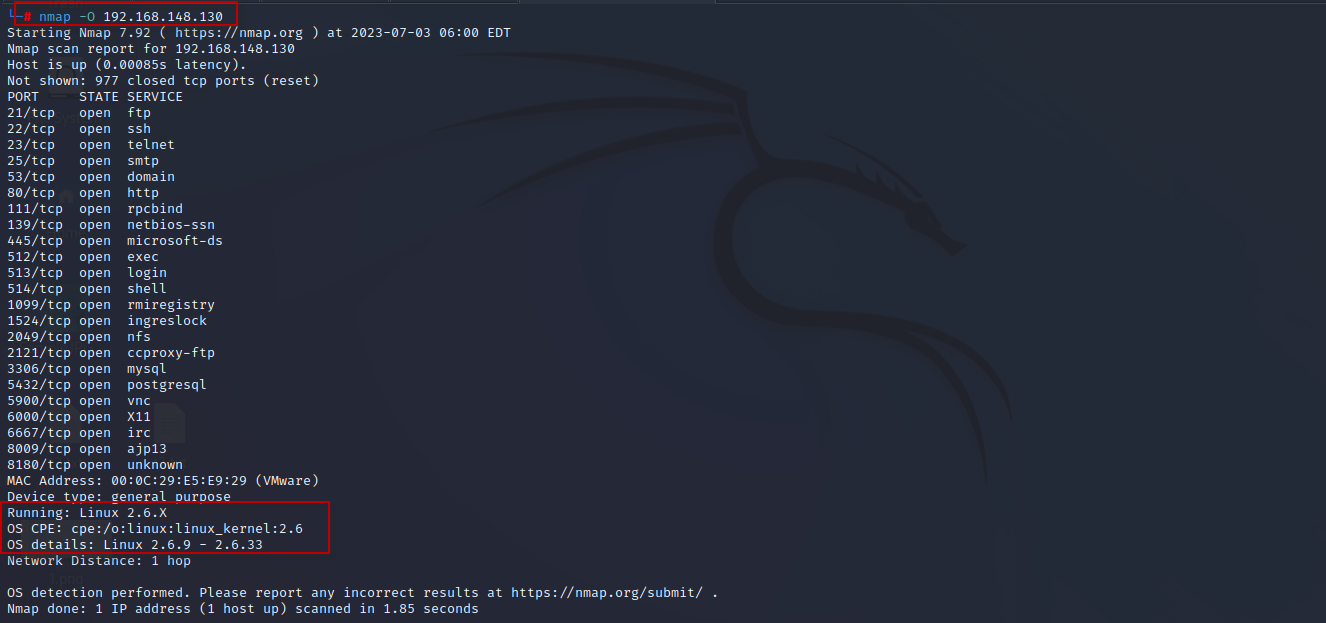
- OS Fingerprinting : It is the process of determining the operating system running on a target machine. Nmap’s OS fingerprinting capabilities (“-O”) analyze various network parameters to make an educated guess about the underlying OS. Here’s an example of OS fingerprinting:
Command : nmap -O 192.168.148.130
Conclusion:
Nmap is an indispensable tool for network exploration and security assessment. Its comprehensive set of features, including host discovery, port scanning, service version detection, and script customization, makes it an essential asset for security professionals and system administrators. By leveraging Nmap’s capabilities, organizations can identify potential vulnerabilities, secure their network infrastructure, and proactively defend against potential threats.
Remember, while Nmap is a powerful tool, it is crucial to use it responsibly and ethically. Always obtain proper authorization before scanning any network, and adhere to legal and ethical guidelines. By leveraging Nmap effectively, security professionals can strengthen the security posture of their organizations and ensure the protection of critical assets.

