
Introduction
Command execution or injection attacks are a type of vulnerability that can compromise the security of web applications. These attacks allow malicious users to execute arbitrary commands on the server, often leading to unauthorized access to sensitive data or system control. In this article, we will demonstrate how command execution and injection work using the DVWA (Damn Vulnerable Web Application) hosted on a Metasploitable2 virtual machine. We will focus on how attackers can exploit these vulnerabilities in a low-security environment to execute system commands, bypass security controls, and gain access to sensitive files.
What is Command Execution/Injection?
Command execution or injection occurs when an attacker is able to insert or inject commands into a vulnerable web application form or input field. These commands are then executed by the server, allowing the attacker to execute arbitrary system-level operations. This is a significant security risk, as it can lead to the disclosure of sensitive information, system manipulation, or even full server control.
In the context of DVWA, a vulnerable web application intentionally designed for security testing, attackers can experiment with command injection techniques to understand and exploit such weaknesses. By manipulating inputs in forms, attackers can run arbitrary commands on the server and interact with the operating system as if they were the system administrator.
Setting Up the DVWA Environment
For this demonstration, we are using Metasploitable2, a vulnerable virtual machine containing several intentionally insecure applications for penetration testing practice. We access the DVWA application hosted on this machine through a web browser. Once logged into the DVWA interface, we set the security level to “Low” to ensure that no significant validation or filtering mechanisms are in place.
The target application in this scenario is a simple form that allows users to input an IP address and submit it to ping the provided IP. At the low-security level, there is little to no input validation or sanitization, which opens up the possibility for command execution and injection attacks.
Executing Commands with a Vulnerable Form
In this particular DVWA lab, the form is designed to perform a ping on a specified IP address. The attacker can input the IP address “127.0.0.1” (the local loopback address) into the form’s text box and click on the submit button. By default, this will send a ping request to the specified IP address.

However, due to the lack of input validation in the form, the attacker can inject arbitrary commands. In this case, we can take advantage of the semicolon (;) operator to separate the ping command from additional commands that we want to execute.
For example, when we input the following payload in the text box:
127.0.0.1; whoami
The server will execute the ping command followed by the whoami command. The whoami command reveals the identity of the currently logged-in user. By exploiting this, the attacker can gain insight into the user privileges on the server.
Using Different Command Separators
While the semicolon (;) is a commonly used command separator, it is often filtered or blocked by application owners who implement basic security controls. In such cases, attackers can try using alternative command separators, such as && or | (pipe), to execute multiple commands in one go.
Let’s look at some variations of command injection payloads:
- Using
&&(AND Operator)
The&&operator ensures that only if the first command (ping) is successful, the next command will execute. This is useful when trying to chain multiple commands. For example:
127.0.0.1&&pwd
Here, after the ping command, the pwd (print working directory) command will be executed. This provides information about the current directory of the server, potentially exposing the file structure.
- Using
|(Pipe Operator)
Another option is using the pipe operator|, which allows the output of one command to be sent as input to another. For example:
127.0.0.1|whoami
This command executes the whoami command after the ping, giving the attacker information about the server’s user privileges. Similarly, running:
127.0.0.1|pwd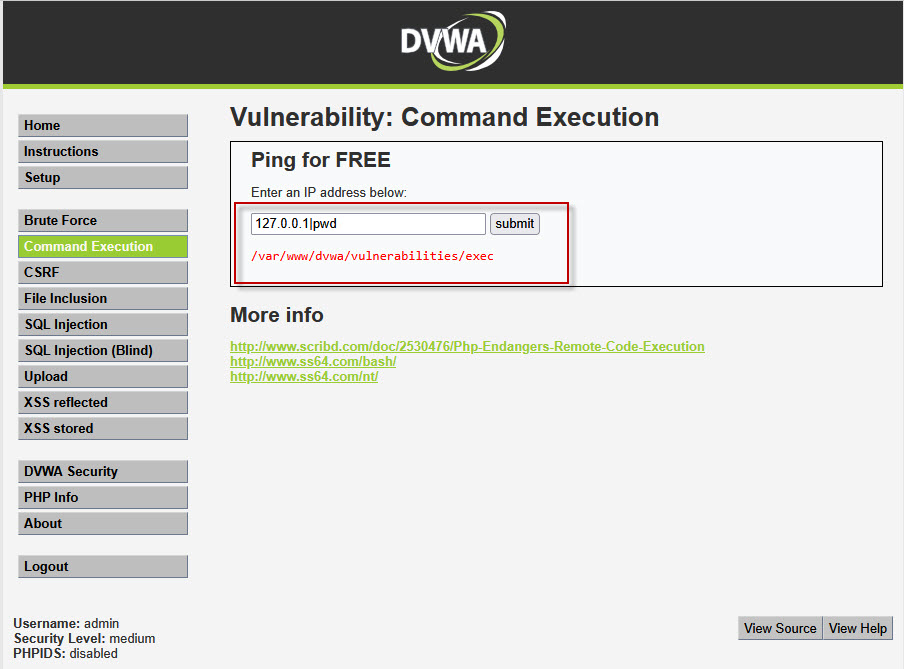
would display the working directory path of the system.
Exploring Sensitive Files with Command Injection
One of the more critical risks of command injection is the potential exposure of sensitive files. If the attacker successfully executes the injection payload, they can use commands like cat /etc/passwd to reveal user account information stored in the system’s password file.
For example:
127.0.0.1;cat /etc/passwd
This command would execute the cat /etc/passwd command, revealing the contents of the /etc/passwd file, which contains sensitive information about users, including usernames and hashed passwords.
Bypassing Basic Security Filters
In a more secure environment, input validation measures may block characters like ;, &&, and |, which are typically used in command injection attacks. However, attackers often find ways to bypass such filters by using alternative characters or encoding techniques.
For example, by using URL encoding or Unicode encoding, an attacker may be able to disguise the malicious input and execute commands without being detected. Furthermore, some filters may only block specific patterns, leaving room for other separators or techniques to work.
Command execution and injection vulnerabilities pose a significant security risk to web applications. In our demonstration with DVWA, we observed how an attacker could manipulate input fields to execute arbitrary system commands on the server. This could lead to the exposure of sensitive information or even full control of the system.
To prevent such attacks, developers should implement rigorous input validation and sanitization, ensuring that only valid data is processed by the server. Using prepared statements, parameterized queries, and limiting the execution of system commands within the web application are critical practices for mitigating command injection risks.
By understanding the techniques behind command injection, organizations can better secure their applications and safeguard sensitive data from malicious actors.










1 Comment
Comments are closed.