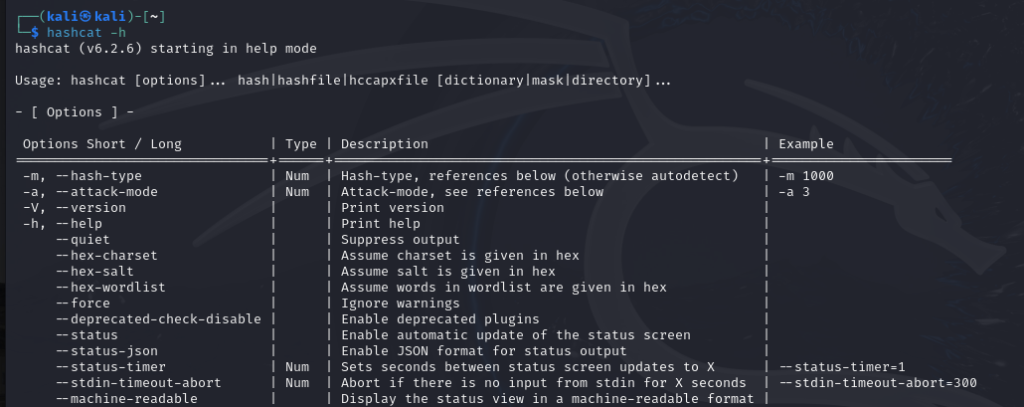
Hashcat is a powerful password recovery tool widely used for cracking hashes. It supports a variety of hash algorithms, including MD5, and can leverage wordlists to streamline the cracking process. This article will walk you through using Hashcat in Kali Linux to crack MD5 hashes, covering the entire process from setting up the environment to viewing the cracked passwords.
Step 1: Log into Kali Linux and Verify the Environment
To begin, log into your Kali Linux system. Use the username kali and the password you’ve set for your installation.
Once logged in, navigate through the menu:
- Select Applications
- Go to 05 – Password Attacks
- Click on Hashcat
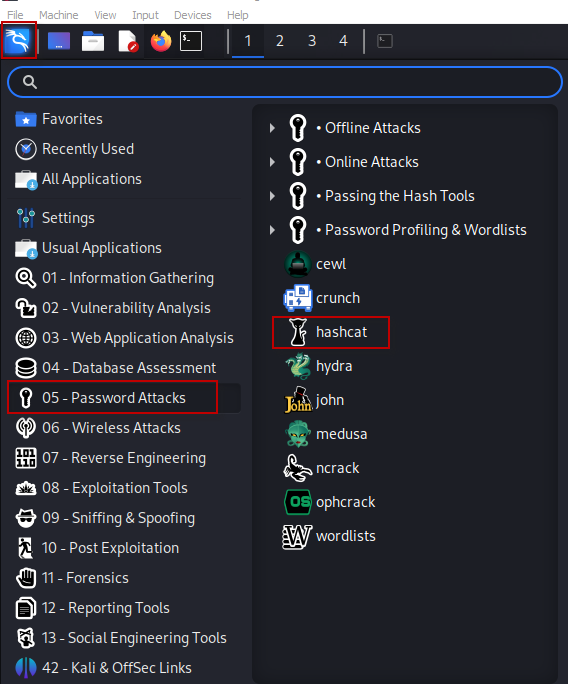
This will ensure that Hashcat is installed and ready for use.
Step 2: Create a File Containing MD5 Hashes
Before we can crack passwords, we need to simulate the scenario of having MD5 hashes. In a real-world scenario, an attacker would typically have compromised a system to obtain password hashes. For our exercise, we will manually create a file with several MD5 hashes.
Open a terminal window and enter the following commands to generate hashes for five different passwords:
$ echo -n 'Password' | md5sum | awk '{ print $1 }' > my_pw_hashes.txt
$ echo -n 'Password123' | md5sum | awk '{ print $1 }' >> my_pw_hashes.txt
$ echo -n 'Letmein!' | md5sum | awk '{ print $1 }' >> my_pw_hashes.txt
$ echo -n 'ilovedogs' | md5sum | awk '{ print $1 }' >> my_pw_hashes.txt
$ echo -n '1234abcd' | md5sum | awk '{ print $1 }' >> my_pw_hashes.txt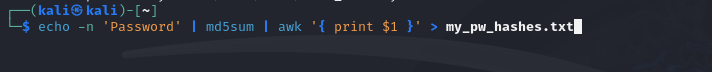
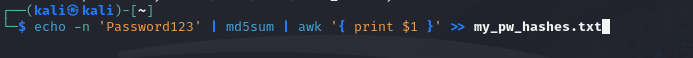 These commands create MD5 hashes of five different passwords and save them to a file named
These commands create MD5 hashes of five different passwords and save them to a file named my_pw_hashes.txt.
To check that your hashes were created correctly, use the following command:
$ cat my_pw_hashes.txt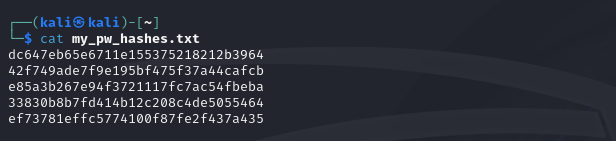
The output should display the five MD5 hashes you’ve just generated.
Step 3: Start Hashcat in Kali
Next, we need to familiarize ourselves with the Hashcat command options. Open a new terminal and type:
$ man hashcat
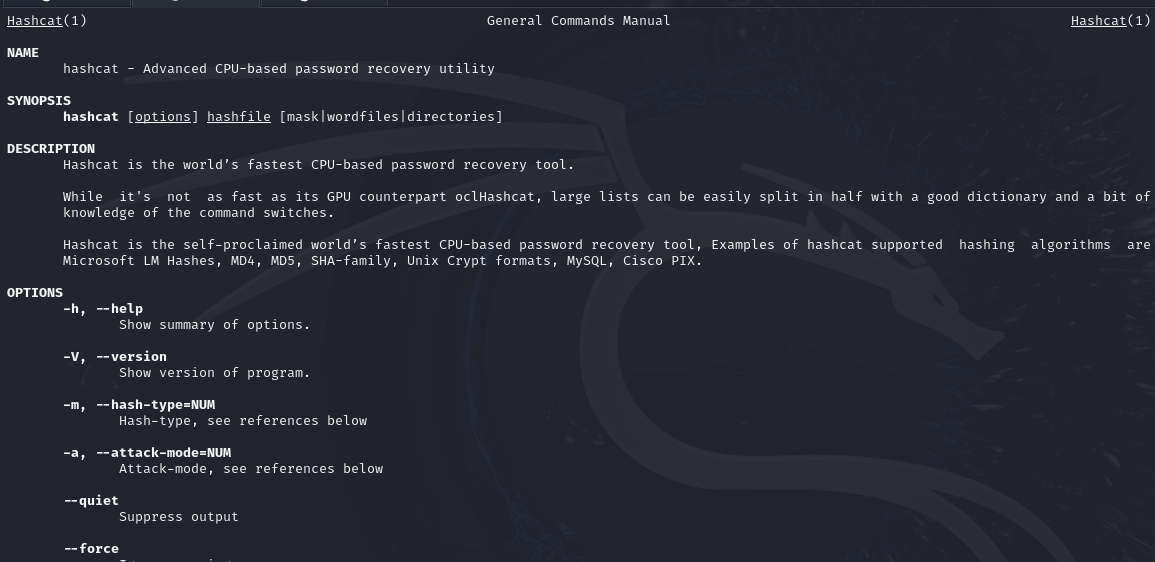
This command opens the Hashcat manual, where you can explore the different options available. Pay special attention to the -m and -a options:
- -m specifies the hash type. For MD5 hashes, use
0. - -a defines the attack mode. The straightforward (dictionary) attack mode is
0.
Make sure to scroll through the manual to understand the different values you can use with these options.
Step 4: View Available Wordlists
Hashcat requires a wordlist to effectively crack the hashes. Kali Linux comes with several built-in wordlists. To view these, execute:
$ ls -lh /usr/share/wordlists/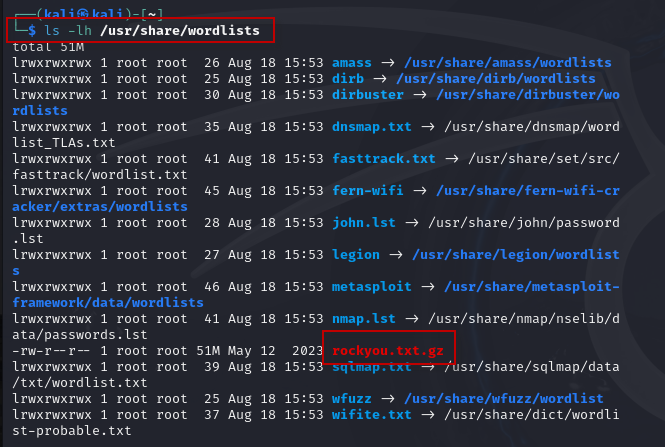
Among the available lists, rockyou.txt is particularly popular, containing over 14 million passwords.
Since this file is compressed, you’ll need to unzip it. Change to the wordlists directory:
$ cd /usr/share/wordlists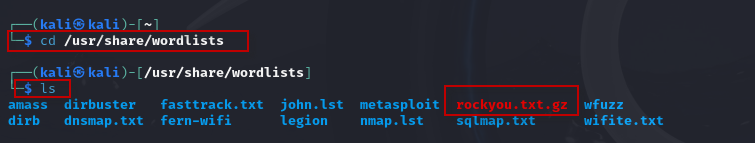
Now, extract the rockyou.txt.gz file using:
$ sudo gzip -d rockyou.txt.gz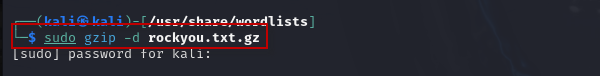
After extraction, list the contents to ensure the rockyou.txt file is present:
$ ls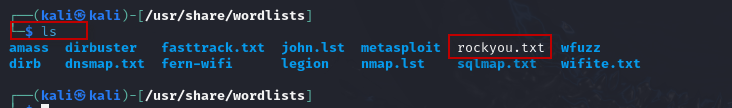
To get a sense of the passwords in the list, you can view the file with:
$ more rockyou.txt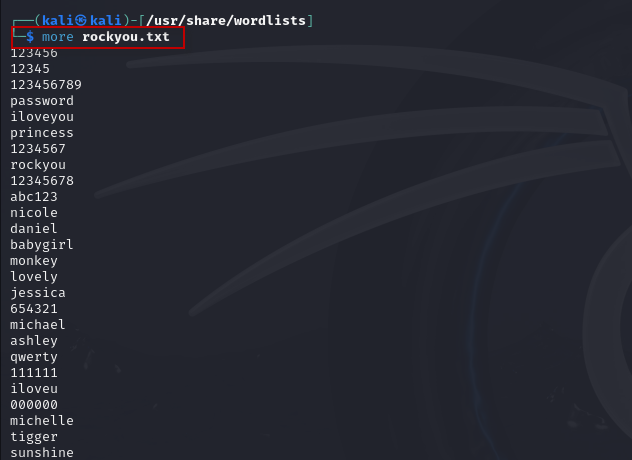
Press q or Ctrl + Z to exit the file viewer and return to the terminal.
Step 5: Crack Hashes with Hashcat
Now we’re ready to crack the hashes using Hashcat. Enter the following command:
$ sudo hashcat -m 0 -a 0 -o cracked.txt my_pw_hashes.txt /usr/share/wordlists/rockyou.txtThis command instructs Hashcat to use:
-m 0for MD5 hashes-a 0for the straight attack mode-o cracked.txtto output the cracked passwords to a new file

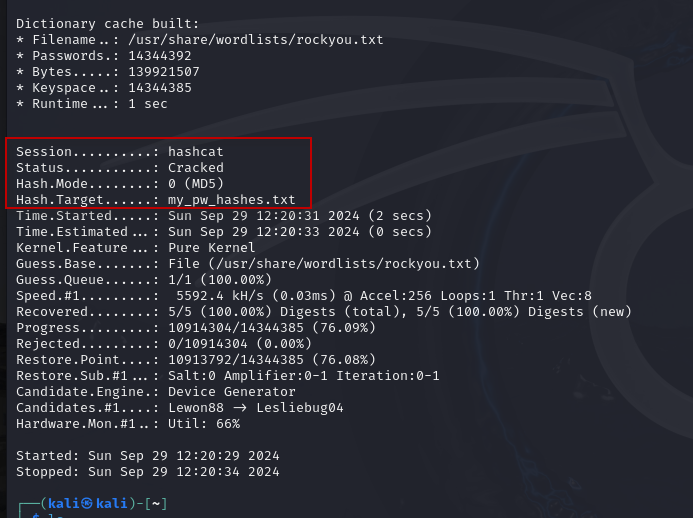
Once the command executes, it should quickly process the hashes and crack all five passwords.
To view the cracked passwords, use:
$ sudo cat cracked.txt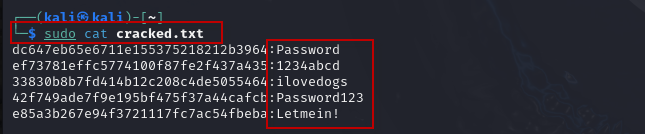
You should see the plaintext passwords corresponding to the MD5 hashes you created earlier.
Conclusion
Using Hashcat in Kali Linux provides a robust method for cracking MD5 hashes through straightforward steps. By generating hashes, utilizing built-in wordlists, and executing Hashcat commands, you can effectively recover plaintext passwords. This powerful tool not only aids in ethical hacking exercises but also enhances your understanding of password security and the vulnerabilities associated with weak password choices.
For further learning, consider experimenting with different attack modes and hash types to deepen your knowledge of Hashcat’s capabilities.








3 Comments
Comments are closed.