
In today’s digital world, security is paramount, especially when it comes to web applications. With the growing number of cyber threats, it’s essential to have reliable tools that help detect vulnerabilities and ensure your web application is secure. One such tool is Wapiti, a powerful and easy-to-use web application vulnerability scanner written in Python. Wapiti is specifically designed to help penetration testers, ethical hackers, and security professionals perform vulnerability assessments on web applications in Kali Linux, an operating system known for its robust suite of security tools.
What is Wapiti?
Wapiti is an open-source web application vulnerability scanner that allows users to audit the security of their web applications. The tool performs what is called a “black-box” scan, meaning it does not require access to the source code of the application. Instead, it works by scanning the deployed web pages, forms, and scripts of the web application, injecting payloads to identify potential vulnerabilities.
The tool operates by first scanning for areas where it can inject data, such as forms, query strings, and URL parameters. Once this information is collected, Wapiti acts like a fuzzer, testing different inputs and payloads to uncover vulnerabilities such as SQL injection, cross-site scripting (XSS), and more.
One of the most appealing aspects of Wapiti is its simplicity. It is easy to install and use, even for beginners, and works effectively on Kali Linux, making it a great addition to the toolkit of cybersecurity professionals.
Features of Wapiti
Wapiti comes packed with features that can help detect various types of vulnerabilities in web applications. Let’s take a closer look at some of its key features:
1. Database Injection (SQL and XPath)
Wapiti can detect SQL injection vulnerabilities in web applications. This includes PHP, ASP, and JSP-based SQL injections, as well as XPath injections. SQL injections are one of the most common and dangerous vulnerabilities, as they can allow attackers to access or manipulate a database without proper authorization. Wapiti scans input points such as form fields and URL parameters to identify these vulnerabilities.
2. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) vulnerabilities are another common attack vector that Wapiti helps to detect. XSS allows attackers to inject malicious scripts into a web page, which can then be executed in the user’s browser. Wapiti can identify both reflected and permanent XSS vulnerabilities, which can lead to the theft of session cookies, credentials, and other sensitive data.
3. File Disclosure Detection
Wapiti is also capable of detecting file disclosure vulnerabilities, including local and remote file inclusion issues. This can occur when web applications improperly handle file paths, allowing an attacker to access sensitive files or even execute arbitrary code. By using tools such as Nikto’s database, Wapiti can search for potentially dangerous files or misconfigured servers.
4. Command Execution Vulnerabilities
Wapiti can identify command execution vulnerabilities such as the use of functions like eval(), system(), or passtru(), which allow attackers to execute arbitrary commands on the server. This type of vulnerability is extremely dangerous, as it can lead to full system compromise.
5. XXE (XML External Entity) Injection
XML External Entity (XXE) injection is a vulnerability in XML parsers that can allow attackers to execute arbitrary code or steal sensitive files from the server. Wapiti can identify XXE vulnerabilities in applications that use XML for data input or configuration.
6. CRLF Injection
Carriage Return Line Feed (CRLF) injection is a type of vulnerability that can be used to manipulate HTTP headers and response splitting. Wapiti scans for this vulnerability, which could allow attackers to perform actions like web cache poisoning, session fixation, or redirecting users to malicious websites.
7. Weak htaccess Configuration Bypass
Web applications using .htaccess files to configure web server security can be vulnerable to bypassing weak configurations. Wapiti scans for such misconfigurations, helping ensure that web servers are properly secured.
8. Backup Script Detection
Wapiti can search for backup copies of scripts or other sensitive files stored on the server. These files, if left unsecured, can expose sensitive information, making the web application vulnerable to attacks.
9. Shellshock Detection
Shellshock is a vulnerability in the Bash shell that allows attackers to execute arbitrary commands on a server. Wapiti can detect this vulnerability and help security professionals address it before attackers can exploit it.
10. Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) occurs when an attacker can manipulate a server to send unauthorized requests to internal resources. Wapiti can detect SSRF vulnerabilities by using an external Wapiti website to test requests.
How to Use Wapiti in Kali Linux
Wapiti is pre-installed in Kali Linux, so you don’t need to worry about installing it manually. Simply open your terminal and you can start using the tool right away. To get help and see all available options, run:
$ wapiti -h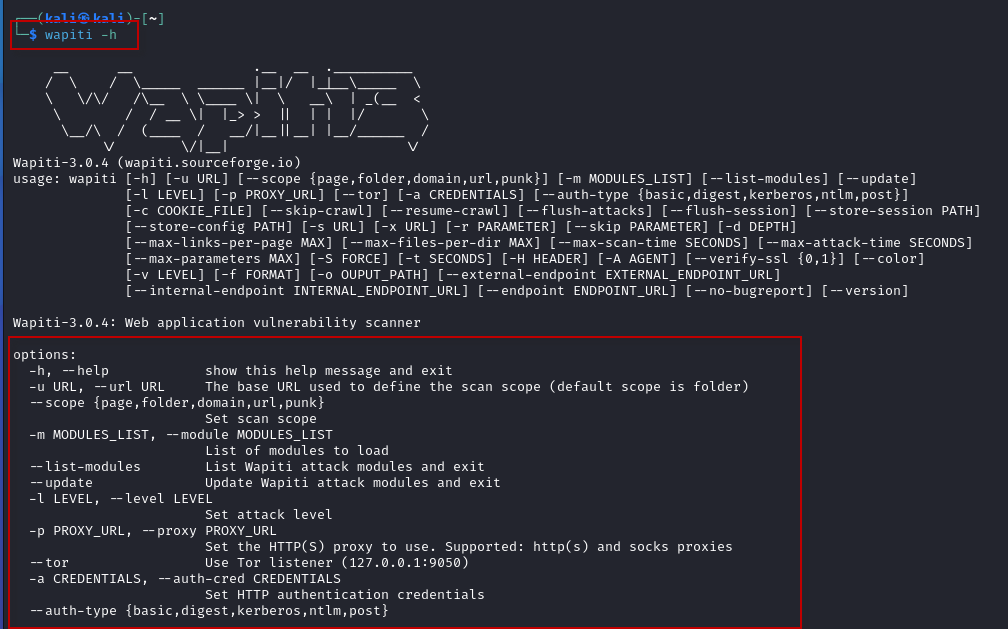
This will display the available options and commands for the tool.
Scanning a Web Application
To perform a basic scan on a web application, use the following command:
$ wapiti -u http://192.168.140.10/mutillidae/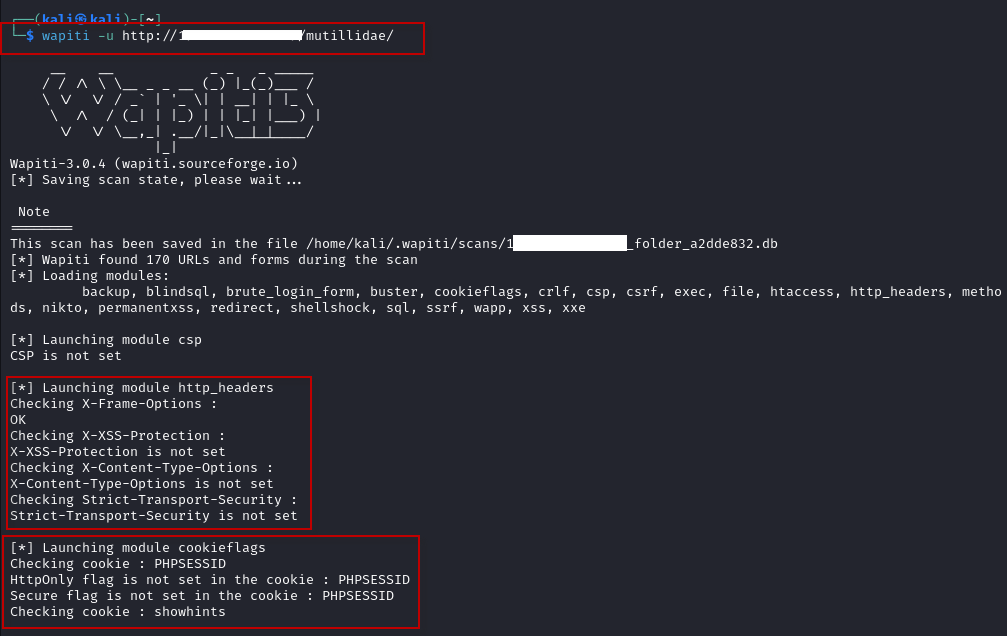
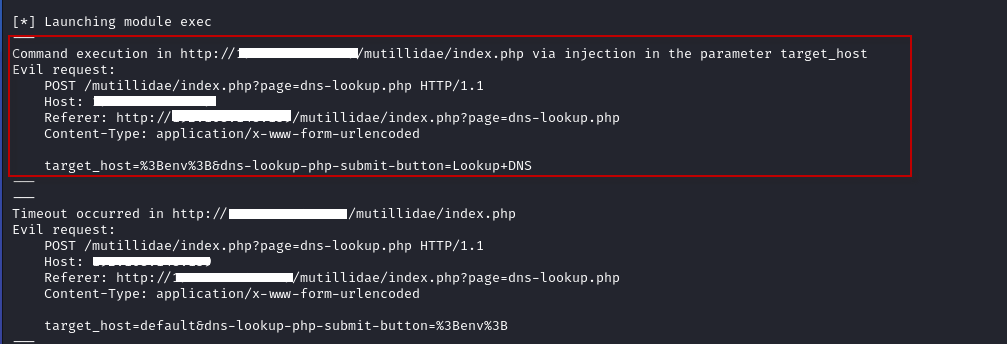
This command tells Wapiti to scan the web application at the specified URL. Wapiti will automatically detect vulnerabilities and perform various tests, such as SQL injection, XSS, and more.
Reviewing the Report
After the scan is complete, Wapiti generates a detailed report. You can find the generated report in the following directory:
/home/kali/.wapiti/generated_report/This report will provide you with detailed information about any vulnerabilities that were found, including their type, severity, and recommendations for remediation.
Conclusion
Wapiti is a versatile and user-friendly web application vulnerability scanner that can help security professionals identify vulnerabilities in web applications. With its comprehensive detection capabilities for SQL injection, XSS, file disclosure, and other common vulnerabilities, Wapiti is an essential tool for web application security testing. Its ease of use, combined with its powerful scanning engine, makes it an invaluable resource for penetration testers, ethical hackers, and anyone looking to ensure the security of their web applications. By incorporating Wapiti into your security toolkit, you can proactively address vulnerabilities and help protect your web applications from potential threats.









