In the world of web application security, the OWASP Zed Attack Proxy (ZAP) stands out as one of the most versatile and user-friendly tools available. This open-source security scanner is an essential resource for both beginners and experienced professionals in the field of cybersecurity. In this article, we will delve into what OWASP ZAP is, how it works, its features, and how to leverage it effectively for your web application security needs.
What is OWASP ZAP?
OWASP ZAP is an open-source web application security scanner and a powerful proxy tool developed by the Open Web Application Security Project (OWASP). It is designed for finding vulnerabilities in web applications through various methods, including automated scanning, fuzzing, and manual testing. ZAP is particularly user-friendly, making it an excellent choice for both novice developers and seasoned security professionals.
You can easily download OWASP ZAP for free from the official website: OWASP ZAP Download. This accessibility makes it a popular choice among organizations of all sizes, from startups to large enterprises.
Key Features of OWASP ZAP
1. Proxy Functionality
One of the standout features of OWASP ZAP is its proxy capability. By configuring your browser to route traffic through ZAP, you can intercept and analyze requests and responses between the browser and the web application. This functionality is crucial for understanding how data flows and for identifying potential vulnerabilities.
2. Automated Scanning
OWASP ZAP offers automated scanning tools that can quickly assess a web application for common vulnerabilities. Users can initiate scans that cover a wide range of security issues, including SQL injection, cross-site scripting (XSS), and insecure configurations. This automated process saves time and ensures that key vulnerabilities are not overlooked.
3. Fuzzing Tools
Fuzzing is a technique used to discover vulnerabilities by sending a large number of unexpected inputs to a web application. OWASP ZAP includes robust fuzzing capabilities that allow users to test how applications respond to different types of data. This is particularly useful for identifying buffer overflows and other critical vulnerabilities.
4. Extensive Reporting
After a scan, OWASP ZAP generates comprehensive reports detailing any vulnerabilities found. These reports are essential for security teams to understand the risks associated with their applications and to prioritize remediation efforts. The reporting features allow for customization, enabling users to focus on specific areas of concern.
5. Add-ons and Integrations
ZAP supports a wide range of add-ons that enhance its functionality. Users can extend its capabilities with features like API scanning, advanced authentication support, and integration with CI/CD pipelines. This flexibility allows organizations to tailor OWASP ZAP to their specific security needs.
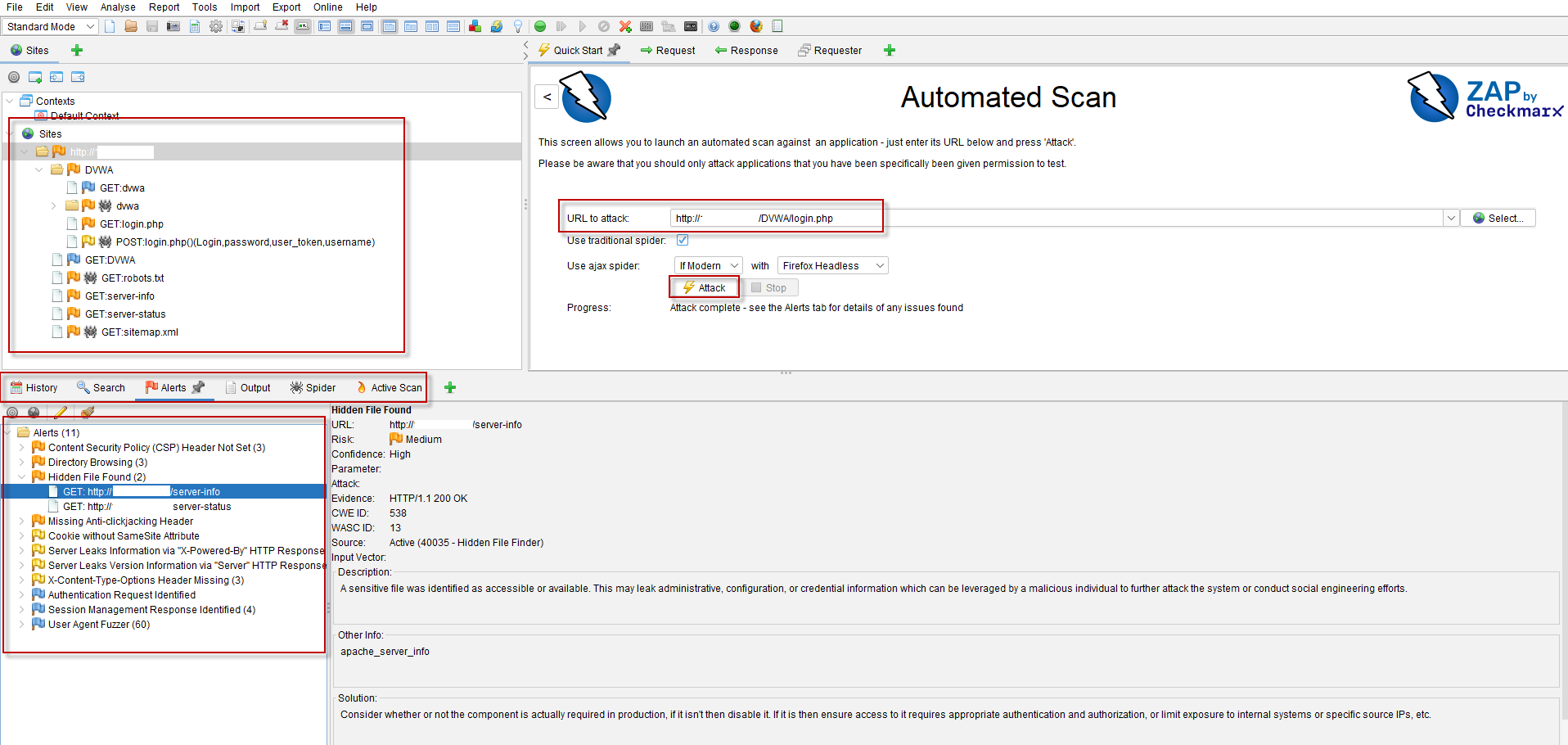
How to Use OWASP ZAP for Automated Scanning
Using OWASP ZAP to perform automated scans is straightforward. Here’s a step-by-step guide to get you started:
- Download and Install ZAP: First, download OWASP ZAP from the official site and install it on your machine.
- Configure the Proxy: Set up your browser to use ZAP as a proxy. This typically involves changing the browser’s network settings to direct traffic through ZAP.
- Explore the Application: Navigate through your web application while ZAP captures the traffic. This step allows ZAP to build a comprehensive map of the application and its endpoints.
- Run an Automated Scan: Once you’ve explored the application, initiate an automated scan by selecting the relevant options in ZAP. The tool will analyze the application for vulnerabilities, leveraging its extensive scanning capabilities.
- Review the Results: After the scan completes, review the findings in the reports generated by ZAP. These reports will highlight any vulnerabilities discovered, along with details on their severity and suggested remediation steps.
- Remediate Vulnerabilities: Collaborate with your development team to address any identified vulnerabilities, ensuring that your application is secure before going live.
Benefits of Using OWASP ZAP
1. Cost-Effective Solution
Being an open-source tool, OWASP ZAP is free to use, making it a cost-effective solution for organizations looking to enhance their security posture without incurring high software costs.
2. User-Friendly Interface
OWASP ZAP’s intuitive user interface makes it accessible even to those with limited security knowledge. This ease of use encourages teams to incorporate regular security testing into their development processes.
3. Comprehensive Coverage
ZAP covers a wide range of vulnerabilities, allowing organizations to address various security issues in one tool. Its extensive feature set makes it suitable for different testing scenarios.
4. Community Support and Resources
As part of the OWASP community, ZAP benefits from continuous updates and contributions from security professionals worldwide. Users can access a wealth of resources, including documentation, forums, and tutorials, to enhance their understanding and use of the tool.
Conclusion
OWASP ZAP is an invaluable resource for any organization looking to secure its web applications. With its powerful scanning capabilities, proxy features, and user-friendly interface, it provides a comprehensive solution for identifying and addressing vulnerabilities. By regularly incorporating OWASP ZAP into your security practices, you can significantly reduce the risk of attacks and protect sensitive data.
Whether you are a developer, security professional, or part of an IT team, OWASP ZAP should be an essential part of your web application security toolkit. Download it today from OWASP ZAP Download and start your journey toward more secure web applications.










1 Comment
Comments are closed.