In today’s security-conscious digital landscape, web application security is more critical than ever. Penetration testers and ethical hackers use a range of tools to identify vulnerabilities in websites and web apps. One such powerful tool is Skipfish, a high-performance web application security scanner that comes pre-installed in Kali Linux. In this guide, we’ll explore how to use Skipfish efficiently, from launching the tool to analyzing its output for identifying vulnerabilities.
What is Skipfish?
Skipfish is a fully automated, high-speed web application vulnerability scanner developed by Google. Designed for security auditing, it prepares an interactive site map for the target web application by carrying out a recursive crawl and dictionary-based probes. The output is presented in a clear, easy-to-navigate HTML report that highlights security issues.
The tool is highly efficient and is especially useful in the early stages of a security audit to quickly identify potential vulnerabilities.
Launching Skipfish in Kali Linux
Since Skipfish comes pre-installed with Kali Linux, you don’t need to download or install it manually. Follow the steps below to access and launch it:
- Open your Kali Linux machine.
- Navigate through the following menu:
-
- Click on Applications
- Go to Web Application Analysis
- Select Skipfish
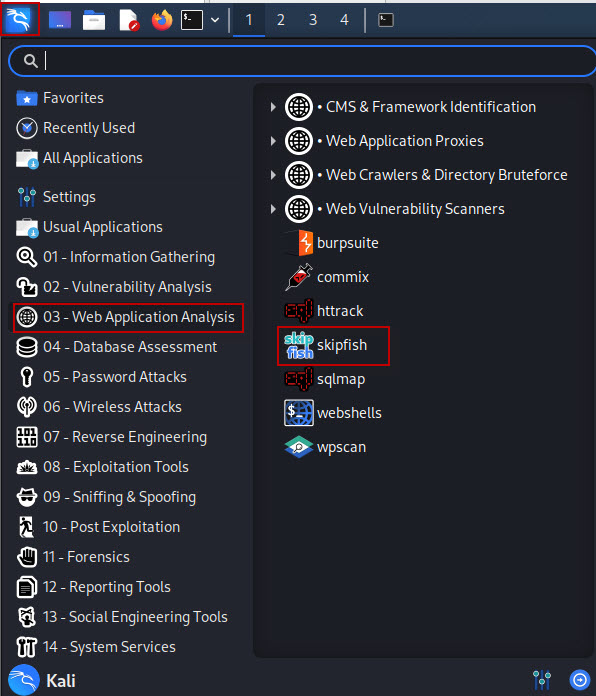
This will open a terminal window ready for Skipfish commands.
Viewing Help Options
To explore the various scanning options available with Skipfish, run the help command in the terminal:
$ skipfish -h
This will display a comprehensive list of flags and options that you can use to tailor your scans according to the needs of your assessment. Whether you want to throttle scan speed, use custom dictionaries, or tweak authentication settings, the -h command is your go-to resource.
Running a Basic Scan
Let’s look at a basic example of scanning a test website using Skipfish. The syntax for initiating a scan is as follows:
$ skipfish -o <output directory path> <target URL>For instance, to scan the popular vulnerable testing site http://testphp.vulnweb.com/ and save the output to a directory on your desktop, use the command:
$ skipfish -o /home/kali/Desktop/Save http://testphp.vulnweb.com/
Here’s a breakdown of the command:
-o /home/kali/Desktop/Save: This flag specifies the output directory. All scan results will be stored here.http://testphp.vulnweb.com/: This is the target URL you want to scan.
Analyzing the Output
After the scan is complete, navigate to the specified output directory:
cd /home/kali/Desktop/SaveYou will find a file named index.html inside the folder. Open this file with a browser to view a detailed, interactive report.

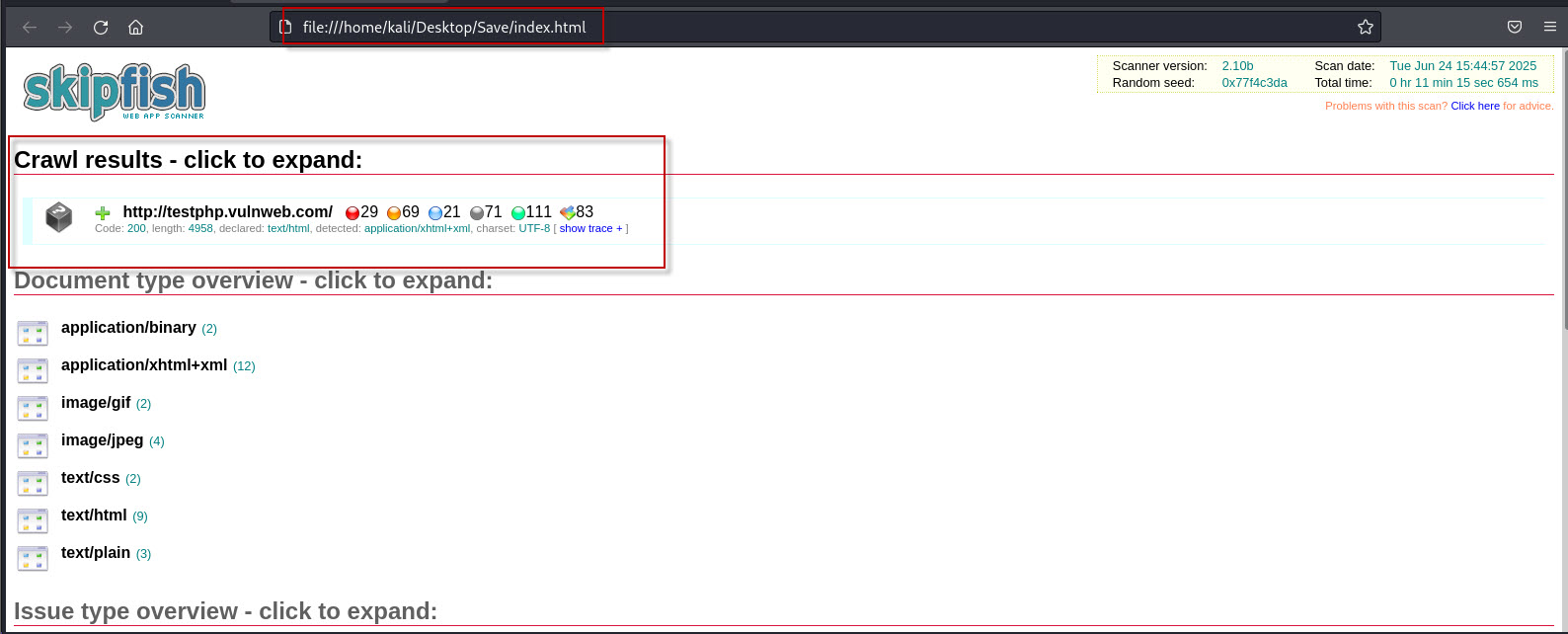
The report provides:
- A site map showing the pages that were scanned.
- A list of vulnerabilities detected.
- An “Issue Type Overview” section where different types of security flaws (e.g., XSS, SQL Injection, insecure cookies) are categorized.
- The ability to click on the scanned URL and see the list of identified vulnerabilities for that specific page.

This interface makes it simple to drill down into individual findings and prioritize them for manual verification or reporting.
Best Practices for Using Skipfish
- Run on test environments: Skipfish is aggressive in its scanning and could overwhelm production servers. Always use it in a safe, controlled testing environment.
- Combine with manual verification: Although Skipfish automates the vulnerability discovery process, it’s important to manually verify each finding before reporting it.
- Regular updates: While Skipfish itself isn’t updated as frequently as other tools, combining it with updated testing environments ensures more accurate results.
- Use dictionaries wisely: Customize dictionaries when targeting specific web applications for improved detection of logic flaws or business-related vulnerabilities.
Conclusion
Skipfish remains a fast and efficient tool for web application scanning, especially useful for initial reconnaissance. With its integration into Kali Linux, it’s accessible and ready to use for penetration testers and ethical hackers alike. While it doesn’t replace manual testing or more advanced scanners, it’s an excellent starting point for identifying potential security issues in any web application.
For anyone getting started with web application security testing, Skipfish offers a simple yet powerful approach to discovering vulnerabilities—all from the convenience of your Kali Linux environment.