John the Ripper is a powerful and widely-used password cracking tool available in Kali Linux. This tool is essential for security professionals, ethical hackers, and anyone interested in testing password strength. In this guide, we will explore how to effectively use John the Ripper to crack MD5 hashes, providing a comprehensive step-by-step process. Whether you’re a beginner or an experienced user, this article will equip you with the knowledge to utilize John the Ripper effectively.
Step 1: Accessing John the Ripper Help File
Before you begin using John the Ripper, it’s important to understand its functionalities and commands. You can access the help file directly from the terminal. Simply type the following command:
$ john -h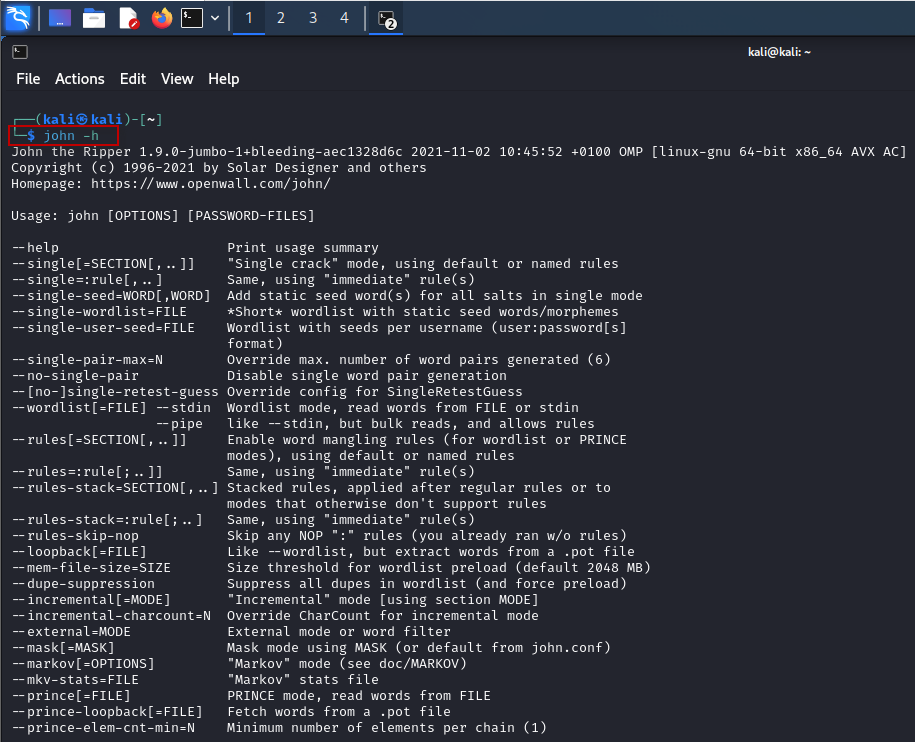
This command will display a list of options and usage instructions for John the Ripper, allowing you to familiarize yourself with its capabilities. If you prefer a graphical interface, you can log into your Kali Linux system and navigate through the menu: Applications > 05 – Password Attacks > Click on John
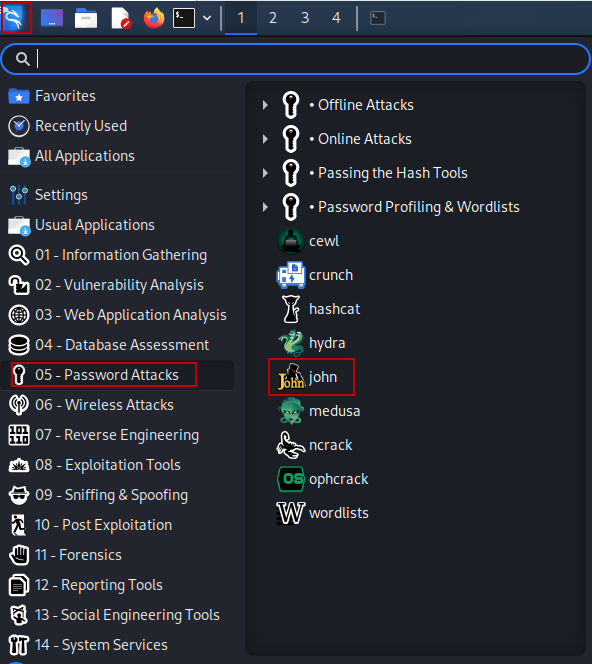
This alternative method provides an easy way to access the tool without needing to use the command line.
Step 2: Creating a File Containing MD5 Hashes
To crack passwords effectively, we first need to simulate a scenario in which we have MD5 hashes. In real-world scenarios, attackers often obtain these hashes from compromised systems. For this exercise, we will manually create a file containing several MD5 hashes.
Open a terminal window and enter the following commands to generate hashes for five different passwords:
$ echo -n 'admin' | md5sum | awk '{ print $1 }' > hash_passwords.txt
$ echo -n 'password' | md5sum | awk '{ print $1 }' >> hash_passwords.txt
$ echo -n 'admin@123' | md5sum | awk '{ print $1 }' >> hash_passwords.txt
$ echo -n 'Password1234' | md5sum | awk '{ print $1 }' >> hash_passwords.txt
$ echo -n 'Administrator' | md5sum | awk '{ print $1 }' >> hash_passwords.txt
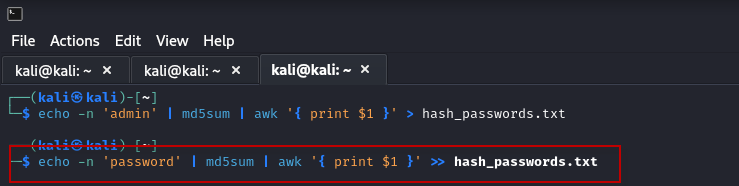
These commands create MD5 hashes for the specified passwords and save them to a file named hash_passwords.txt. To verify that your hashes were created correctly, use the following command:
$ cat hash_passwords.txt
This command will display the five MD5 hashes you just generated, allowing you to confirm their accuracy.
Step 3: Cracking Hashes with John the Ripper
Now that we have our hashes, it’s time to crack them using John the Ripper. Use the following command to start cracking the hashes stored in hash_passwords.txt:
$ john --format=raw-md5 hash_passwords.txt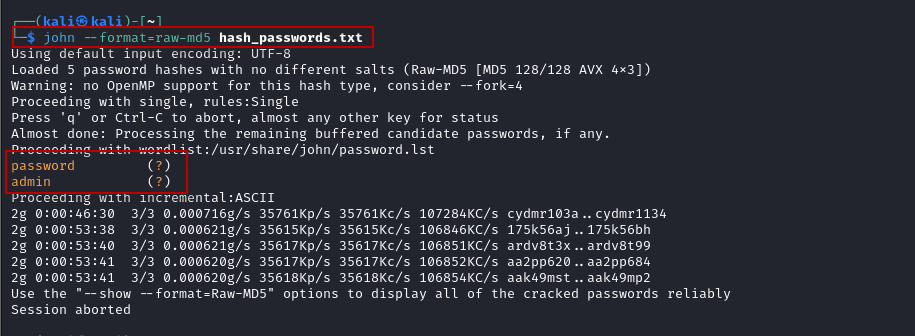
As John processes the hashes, it will display the cracked passwords in orange. You can expect common passwords like “password” and “admin” to be cracked almost immediately, as they are included in John’s default wordlists.
For hashes that John cannot crack with its built-in wordlists, it will switch to incremental strategies, using brute force on the remaining hashes. If you allow John to run long enough, it will eventually crack the remaining passwords. This process may take between 10-20 minutes, depending on the complexity of the hashes. You can press Ctrl-C or q at any time to abort the process if you’ve already cracked enough passwords.
Step 4: Using Larger Wordlists
The default wordlist in John the Ripper is relatively small, which can limit its effectiveness against more complex passwords. To improve your cracking success, consider using larger wordlists such as rockyou.txt, a well-known resource in the password cracking community.
To utilize the rockyou.txt wordlist, run the following command:
$ john --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-md5 hash_passwords.txtThis command instructs John to use the larger wordlist, which may increase the likelihood of cracking more complex passwords.
Note: Extract the rockyou.txt.gz file using command “sudo gzip -d rockyou.txt.gz”.
Step 5: Utilizing Brute Force
For a more exhaustive approach to cracking, you can instruct John the Ripper to perform a brute force attack. This method can be significantly slower but is effective for cracking complex passwords. To initiate brute force cracking, enter the following command:
$ john --format=raw-md5 hash_passwords.txt --incrementalKeep in mind that brute force attacks can take a considerable amount of time, especially for longer or more complex passwords. A powerful GPU may require hours to crack even an 8-character password. Despite MD5 being considered weak by today’s standards, you may still be surprised by the duration it takes to crack even a single MD5 hash using brute force. You can abort the process at any time by pressing Ctrl-C or q.
Step 6: Displaying Cracked Passwords
Once you’ve completed the cracking process, you may want to review the cracked passwords. If you interrupted the cracking session, you can still view the cracked passwords by using the --show option. Run the following command:
$ john --show --format=raw-md5 hash_passwords.txt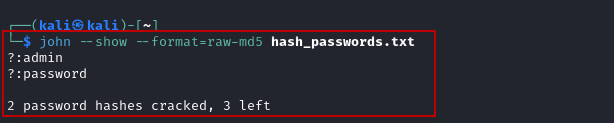
This command will display the cracked passwords alongside their corresponding hashes, giving you a clear overview of your cracking success.
Conclusion
John the Ripper is an essential tool for anyone interested in password security and ethical hacking. By following the steps outlined in this guide, you can effectively use John the Ripper to crack MD5 hashes and enhance your understanding of password security.
As you become more proficient with John the Ripper, consider exploring additional wordlists and advanced cracking techniques. Always remember that ethical hacking practices emphasize using these tools responsibly and only in authorized environments.








4 Comments
Comments are closed.