
SQL Injection (SQLi) vulnerabilities represent one of the most significant threats to web applications today. By exploiting these vulnerabilities, attackers can gain unauthorized access to databases, allowing them to view, insert, delete, or modify records. This article will delve into... Read more

In the ever-evolving landscape of web security, HTTP Host header attacks have emerged as a significant threat. These attacks exploit vulnerabilities in how websites handle HTTP Host headers, leading to various security issues, including password reset poisoning. This article delves... Read more
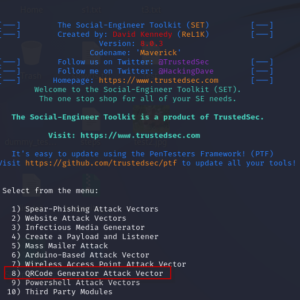
In the world of cybersecurity, social engineering is a powerful tool for exploiting human psychology to gain unauthorized access to systems and data. One of the most intriguing methods within the Social Engineering Toolkit (SET) is the QRCode Generator Attack... Read more

In the realm of cybersecurity and digital investigations, “Google hacking” — also known as Google dorking — is a potent technique for uncovering hidden or sensitive information on the web. This approach leverages Google’s advanced search operators to extract valuable... Read more