
In the realm of cybersecurity, cracking password hashes is a crucial skill for ethical hackers and security professionals. One of the most efficient ways to do this is through RainbowCrack and rainbow tables. Unlike traditional brute-force methods, which can be... Read more
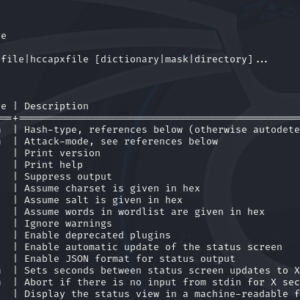
Hashcat is a powerful password recovery tool widely used for cracking hashes. It supports a variety of hash algorithms, including MD5, and can leverage wordlists to streamline the cracking process. This article will walk you through using Hashcat in Kali... Read more

In the realm of cybersecurity and digital investigations, “Google hacking” — also known as Google dorking — is a potent technique for uncovering hidden or sensitive information on the web. This approach leverages Google’s advanced search operators to extract valuable... Read more